Product
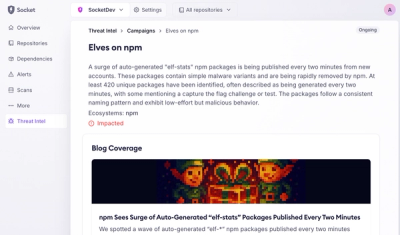
Introducing Supply Chain Attack Campaigns Tracking in the Socket Dashboard
Campaign-level threat intelligence in Socket now shows when active supply chain attacks affect your repositories and packages.
Implementation of ip-hash balancing algorithm, based on round-robin.
$ npm install ip-hash --save
const iphash = require('ip-hash');
let servers = [
'server-1',
'server-2',
'server-3'
];
let assign = iphash(servers);
assign('192.168.0.1'); // => 'server-1'
assign('192.168.0.2'); // => 'server-2'
assign('192.168.0.3'); // => 'server-3'
assign('192.168.0.1'); // => 'server-1'
$ make test
ip-hash is released under the MIT license.
FAQs
ip-hash balancing algorithm
The npm package ip-hash receives a total of 2 weekly downloads. As such, ip-hash popularity was classified as not popular.
We found that ip-hash demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Campaign-level threat intelligence in Socket now shows when active supply chain attacks affect your repositories and packages.

Research
Malicious PyPI package sympy-dev targets SymPy users, a Python symbolic math library with 85 million monthly downloads.

Security News
Node.js 25.4.0 makes require(esm) stable, formalizing CommonJS and ESM compatibility across supported Node versions.