Product
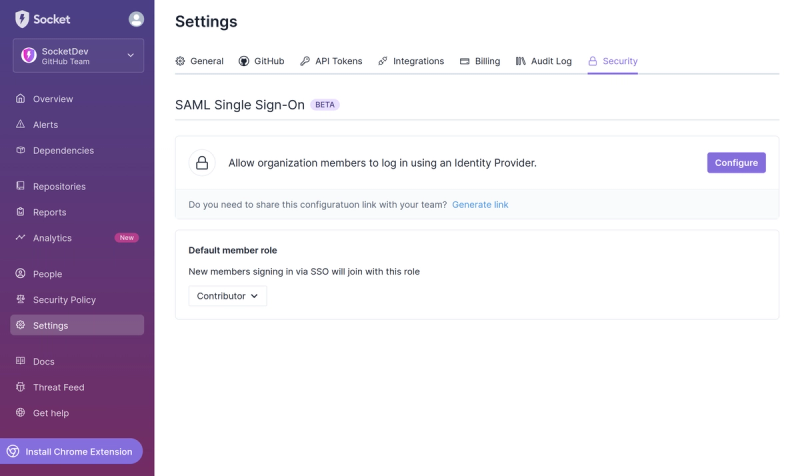
Introducing SSO
Streamline your login process and enhance security by enabling Single Sign-On (SSO) on the Socket platform, now available for all customers on the Enterprise plan, supporting 20+ identity providers.
passport-ldaplng
Advanced tools
Readme
Passport authentication strategy against LDAP server. This module is a Passport strategy wrapper for ldapauth-fork
var LdapStrategy = require('passport-ldapauth').Strategy;
passport.use(new LdapStrategy({
server: {
url: 'ldap://localhost:389',
...
}
}));
If you wish to e.g. do some additional verification or initialize user data to local database you may supply a verify callback which accepts user object and then calls the done callback supplying a user, which should be set to false if user is not allowed to authenticate. If an exception occured, err should be set.
var LdapStrategy = require('passport-ldapauth').Strategy;
passport.use(new LdapStrategy({
server: {
url: 'ldap://localhost:389',
...
}
},
function(user, done) {
...
return done(null, user);
}
));
npm install passport-ldapauth
server: LDAP settings. These are passed directly to ldapauth-fork. See its documentation for all available options.
url: e.g. ldap://localhost:389adminDn: e.g. cn='root'adminPassword: Password for adminDnsearchBase: e.g. o=users,o=example.comsearchFilter: LDAP search filter, e.g. (uid={{username}}). Use literal {{username}} to have the given username used in the search.searchAttributes: Optional array of attributes to fetch from LDAP server, e.g. ['displayName', 'mail']. Defaults to undefined, i.e. fetch all attributestlsOptions: Optional object with options accepted by Node.js tls module.usernameField: Field name where the username is found, defaults to username
passwordField: Field name where the password is found, defaults to password
passReqToCallback: When true, req is the first argument to the verify callback (default: false):
passport.use(new LdapStrategy(..., function(req, user, done) {
...
done(null, user);
}
));
var express = require('express'),
passport = require('passport'),
LdapStrategy = require('passport-ldapauth').Strategy;
var OPTS = {
server: {
url: 'ldap://localhost:389',
adminDn: 'cn=root',
adminPassword: 'secret',
searchBase: 'ou=passport-ldapauth',
searchFilter: '(uid={{username}})'
}
};
var app = express();
passport.use(new LdapStrategy(OPTS));
app.configure(function() {
app.use(express.bodyParser());
app.use(passport.initialize());
});
app.post('/login', passport.authenticate('ldapauth', {session: false}), function(req, res) {
res.send({status: 'ok'});
});
app.listen(8080);
Simple example config for connecting over ldaps:// to a server requiring some internal CA certificate (often the case in corporations using Windows AD).
var fs = require('fs');
var opts = {
server: {
url: 'ldaps://ad.corporate.com:636',
adminDn: 'non-person@corporate.com',
adminPassword: 'secret',
searchBase: 'dc=corp,dc=corporate,dc=com',
searchFilter: '(&(objectcategory=person)(objectclass=user)(|(samaccountname={{username}})(mail={{username}})))',
searchAttributes: ['displayName', 'mail'],
tlsOptions: {
ca: [
fs.readFileSync('/path/to/root_ca_cert.crt')
]
}
}
};
...
Instead of providing a static configuration object, you can pass to the LdapStrategy a function that will take care of fetching the configuration.
Example (here process.nextTick illustrates the asynchronous workings; in a real world this will for example be a database query):
function getLDAPConfiguration(callback) {
process.nextTick(function() {
var opts = {
server: {
url: 'ldap://localhost:389',
adminDn: 'cn=root',
adminPassword: 'secret',
searchBase: 'ou=passport-ldapauth',
searchFilter: '(uid={{username}})'
}
};
callback(null, opts);
});
}
var LdapStrategy = require('passport-ldapauth').Strategy;
passport.use(new LdapStrategy(getLDAPConfiguration,
function(user, done) {
...
return done(null, user);
}
));
MIT
FAQs
LDAP authentication strategy for Passport
The npm package passport-ldaplng receives a total of 3 weekly downloads. As such, passport-ldaplng popularity was classified as not popular.
We found that passport-ldaplng demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Streamline your login process and enhance security by enabling Single Sign-On (SSO) on the Socket platform, now available for all customers on the Enterprise plan, supporting 20+ identity providers.

Security News
Tea.xyz, a crypto project aimed at rewarding open source contributions, is once again facing backlash due to an influx of spam packages flooding public package registries.
Security News
As cyber threats become more autonomous, AI-powered defenses are crucial for businesses to stay ahead of attackers who can exploit software vulnerabilities at scale.