
Research
Malicious npm Packages Impersonate Flashbots SDKs, Targeting Ethereum Wallet Credentials
Four npm packages disguised as cryptographic tools steal developer credentials and send them to attacker-controlled Telegram infrastructure.
WARNING: since 0.2.0, completely new API is implemented (described below). 0.1.x API is not supported anymore.
sslkeylog is a module for easy generation of SSLKEYLOG files, which can be used later by Wireshark to decrypt SSL connections. This method works with any TLS cipher suite including elliptic curves crypto, and works regardless of the TLS version.
sslkeylog also allows one to use the keylog API introduced in Node.JS 12.3.0, in earlier versions of Node (up to v10). See use as a polyfill.
Further reading about SSLKEYLOG:
Node.js v10+ is required. Tested on v10 (LTS), v11, v12; OS X and Linux.
Install the module:
npm install -g sslkeylog
Set the SSLKEYLOGFILE environment variable as usual:
export SSLKEYLOGFILE=/tmp/keys.log
Then in your code, call the hookAll function at startup:
require('sslkeylog').hookAll();
That's it! Run your code and decryption keys will be logged to the specified file.
If you don't want to use SSLKEYLOGFILE or want to override it, you can use setLog:
sslkeylog.setLog('/tmp/otherkeys.log').hookAll();
hookAll will log decryption keys for every TLS connection initiated or received by the Node.JS process. This is okay for quick debugging, but is bad practice and may fail (because it patches Node.JS internals) or may be inconvenient if you have lots of connections.
Instead of calling hookAll, you may use (a combination of) other functions to log only certain connections:
To log all incoming connections to a tls.Server (or derivates such as https.Server
or http2.Server), use hookServer:
const myServer = https.createServer(...);
// ...
myServer.listen(...);
sslkeylog.hookServer(myServer);
To log outgoing connections for HTTPS requests made by your code, use hookAgent:
sslkeylog.hookAgent();
This will only work for requests that use the default agent. If the requests you're interested in specify a custom agent, you must hook this agent instead:
const myAgent = new Agent(...);
sslkeylog.hookAgent(myAgent);
// ...
https.request({ ..., agent: myAgent, ... })
// ...
For more advanced use cases where you want to log a particular connection,
you can pass the created TLSSocket to hookSocket. For example, with tls.connect:
const mySocket = tls.connect(...);
sslkeylog.hookSocket(mySocket);
// ...
With http2.connect:
const http2Session = http2.connect(...);
sslkeylog.hookSocket(http2Session.socket);
// ...
Note that you must call hookSocket as soon as the TLSSocket is created (in
the same loop tick), otherwise keys may not be logged properly.
For more advanced use cases, you can use the keylog API directly:
require('sslkeylog') will activate the polyfill. Then you can use the API as usual.If you are using Node 12.2.x or earlier, make sure usual compiling tools (make, g++, etc.) are installed; on Ubuntu / Debian, sudo apt-get install build-essentials should suffice.
To use in your project, install as usual:
$ npm install --save-dev sslkeylog
...or add to package.json and use npm/yarn to do the work.
For dev environment, clone the repository first:
$ git clone https://github.com/kolontsov/node-sslkeylog
$ cd node-sslkeylog
$ npm install
...
$ cd examples
Clone the repository, build with npm install and go to examples/ subdir. Open few terminal tabs or tmux/screen windows.
make server (starts https server on port 8000)make capture (starts tcpdump on loopback-interface, port 8000)make req (curl https://localhost:8000)Now you have sslkeylog.txt (written by https server) and test.pcap (written by tcpdump).
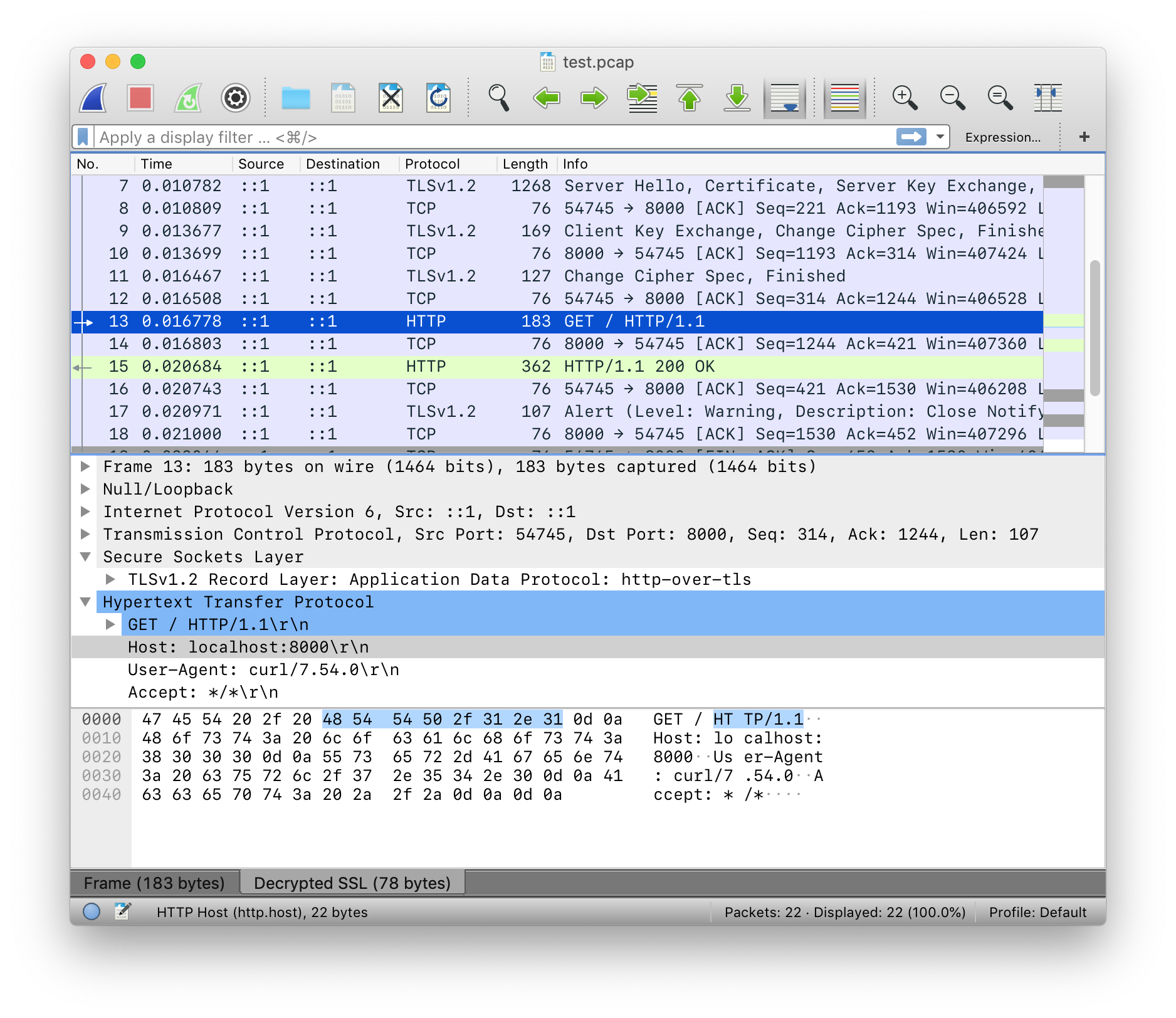
Open test.pcap in Wireshark, right-click on any TLS packet, choose Protocol Preferences → Open Secure Sockets Layer Preferences → (Pre)-Master-Secret log filename and fill full path to to sslkeylog.txt
Now you can see decrypted packets:
filename (String): Set filename at which (future) decryption keys will be logged.Sets the log filename. Returns the module object.
socket (tls.TLSSocket): Socket to log decryption keys for.Log keys for a particular client socket. This method must be called after creating the socket (i.e. at the same event loop tick) to guarantee that all keys are logged. Logging the same socket multiple times has no effect.
Returns the passed socket.
server (tls.Server): Server to log decryption keys for.Log keys for all (future) incoming connections to the passed server. Logging the same server multiple times has no effect.
Returns the passed server.
agent (https.Agent | undefined): Agent to log decryption keys for.Log keys for all (future) outgoing connections created by the passed agent.
If no agent is passed, https.globalAgent will be used.
Returns the patched agent.
Log every TLS socket that is created. This relies on patching TLSSocket#_init,
so it may break and is not guaranteed to remain compatible with future Node.JS releases.
Calling this method multiple times has no effect.
Not tested on production, use at your own risk. Issues/PRs are welcome.
MIT
[0.2.2] - 2019-06-11
FAQs
Server-side SSLKEYLOG generation
We found that sslkeylog demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Four npm packages disguised as cryptographic tools steal developer credentials and send them to attacker-controlled Telegram infrastructure.

Security News
Ruby maintainers from Bundler and rbenv teams are building rv to bring Python uv's speed and unified tooling approach to Ruby development.

Security News
Following last week’s supply chain attack, Nx published findings on the GitHub Actions exploit and moved npm publishing to Trusted Publishers.