Product
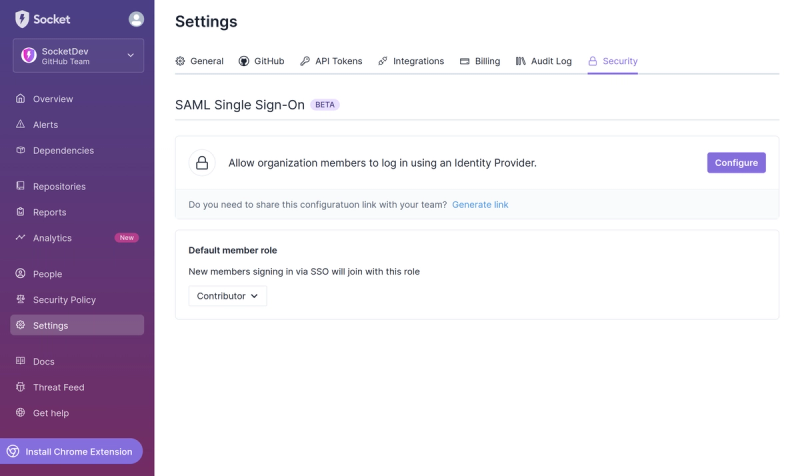
Introducing SSO
Streamline your login process and enhance security by enabling Single Sign-On (SSO) on the Socket platform, now available for all customers on the Enterprise plan, supporting 20+ identity providers.
Readme
It can load a yaml file based on NODE_ENV or passed env (or using development as default). It uses ursa for encryption.
It can deep merge default section and env section of your yaml perfectly.
You can have yaml file
default:
username: Admin
password: Password
days:
- Monday
- Tuesday
- Friday
devices:
android: true
ios: false
development:
password: local
devices:
ios: true
production:
password: decrypt(A7YzqIBjGgXWKA9yl81hgSal7djwBuXK5nBS15JswtzyxKWXilS8buiTZ2XqK9czq)
configs = Yml.load 'config.yml'
# { username: 'Admin', password: 'local', days: ['Monday', 'Tuesday', 'Friday'], devices: { android: true, ios: true } }
configs = Yml.load 'config.yml', 'production', { key: 'security.key.pem' }
# { username: 'Admin', password: 'decrypted_pass', days: ['Monday', 'Tuesday', 'Friday'], devices: { android: true, ios: false } }
If you have defined NODE_ENV in your system, you dont need to pass the env parameter.
# if NODE_ENV = 'production' is set in server, these lines have same result
configs = Yml.load 'config.yml', { key: 'security.key.pem' }
configs = Yml.load 'config.yml', 'production', { key: 'security.key.pem' }
# { username: 'Admin', password: 'decrypted_pass', days: ['Monday', 'Tuesday', 'Friday'], devices: { android: true, ios: false } }
You should create public/private keys with a command like this:
openssl rsa -in security.key.pem -pubout -out security.pub
You can store public key in the machine which responsible for generating the encrypted information. And use private key in the machine which should load the .yml file.
You can use the helper method provided in the library to generate the encrypted phrase, instead of storing the password or critical information.
Yml = require 'yml'
Yml.encrypt 'password', 'security.pub'
# A7YzqIBjGgXWKA9yl81hgSal7djwBuXK5nBS15JswtzyxKWXilS8buiTZ2XqK9czq
# You can store this value in your .yml file
You can read more about encryption here.
FAQs
Read Yaml files based on NODE_ENV or passed env + support for encryption
The npm package yml receives a total of 1,099 weekly downloads. As such, yml popularity was classified as popular.
We found that yml demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 2 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Streamline your login process and enhance security by enabling Single Sign-On (SSO) on the Socket platform, now available for all customers on the Enterprise plan, supporting 20+ identity providers.

Security News
Tea.xyz, a crypto project aimed at rewarding open source contributions, is once again facing backlash due to an influx of spam packages flooding public package registries.
Security News
As cyber threats become more autonomous, AI-powered defenses are crucial for businesses to stay ahead of attackers who can exploit software vulnerabilities at scale.