
Research
/Security News
60 Malicious Ruby Gems Used in Targeted Credential Theft Campaign
A RubyGems malware campaign used 60 malicious packages posing as automation tools to steal credentials from social media and marketing tool users.
Azure.MixedReality.Authentication
Advanced tools
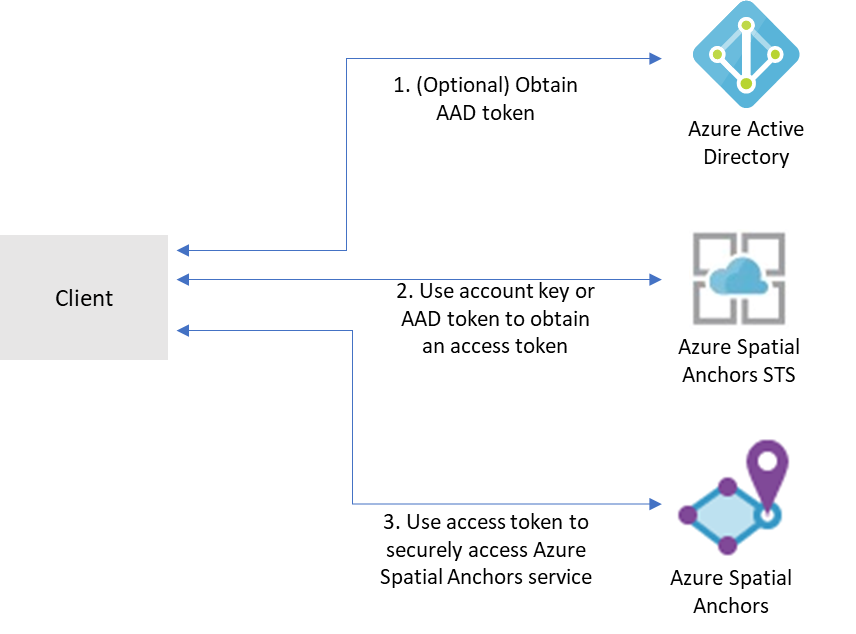
Mixed Reality services, like Azure Spatial Anchors, Azure Remote Rendering, and others, use the Mixed Reality security token service (STS) for authentication. This package supports exchanging Mixed Reality account credentials for an access token from the STS that can be used to access Mixed Reality services.
Install the Azure Mixed Reality Authentication client library for .NET with NuGet:
dotnet add package Azure.MixedReality.Authentication
Add a package reference:
<PackageReference Include="Azure.MixedReality.Authentication" Version="1.0.0" />
Mixed Reality services support a few different forms of authentication:
See here for detailed instructions and information.
Below are some examples of some common authentication scenarios, but more examples and information can be found at Azure.Identity.
Use the MixedRealityStsClient constructor overload accepting an AzureKeyCredential to configure account key
authentication with the Mixed Reality STS:
AzureKeyCredential keyCredential = new AzureKeyCredential(accountKey);
MixedRealityStsClient client = new MixedRealityStsClient(accountId, accountDomain, keyCredential);
Note: Account key authentication is not recommended for production applications.
TokenCredential aadCredential = new ClientSecretCredential(tenantId, clientId, clientSecret, new TokenCredentialOptions
{
AuthorityHost = new Uri($"https://login.microsoftonline.com/{tenantId}")
});
MixedRealityStsClient client = new MixedRealityStsClient(accountId, accountDomain, aadCredential);
Task deviceCodeCallback(DeviceCodeInfo deviceCodeInfo, CancellationToken cancellationToken)
{
Debug.WriteLine(deviceCodeInfo.Message);
Console.WriteLine(deviceCodeInfo.Message);
return Task.FromResult(0);
}
TokenCredential deviceCodeCredential = new DeviceCodeCredential(deviceCodeCallback, tenantId, clientId, new TokenCredentialOptions
{
AuthorityHost = new Uri($"https://login.microsoftonline.com/{tenantId}"),
});
MixedRealityStsClient client = new MixedRealityStsClient(accountId, accountDomain, deviceCodeCredential);
AccessToken token = await client.GetTokenAsync();
See here for more information about using device code authentication flow.
Use the DefaultAzureCredential object with includeInteractiveCredentials: true to use default interactive authentication
flow:
TokenCredential credential = new DefaultAzureCredential(includeInteractiveCredentials: true);
MixedRealityStsClient client = new MixedRealityStsClient(accountId, accountDomain, credential);
The MixedRealityStsClient is the client library used to access the Mixed Reality STS to get an access token.
Tokens obtained from the Mixed Reality STS have a lifetime of 24 hours.
We guarantee that all client instance methods are thread-safe and independent of each other (guideline). This ensures that the recommendation of reusing client instances is always safe, even across threads.
Client options | Accessing the response | Long-running operations | Handling failures | Diagnostics | Mocking | Client lifetime
AzureKeyCredential keyCredential = new AzureKeyCredential(accountKey);
MixedRealityStsClient client = new MixedRealityStsClient(accountId, accountDomain, keyCredential);
AccessToken token = await client.GetTokenAsync();
See the authentication examples above for more complex authentication scenarios.
Some Mixed Reality client libraries might accept an access token in place of a credential. For example:
// GetMixedRealityAccessTokenFromWebService is a hypothetical method that retrieves
// a Mixed Reality access token from a web service. The web service would use the
// MixedRealityStsClient and credentials to obtain an access token to be returned
// to the client.
AccessToken accessToken = await GetMixedRealityAccessTokenFromWebService();
SpatialAnchorsAccount account = new SpatialAnchorsAccount(accountId, accountDomain);
SpatialAnchorsClient client = new SpatialAnchorsClient(account, accessToken);
Note: The SpatialAnchorsClient usage above is hypothetical and may not reflect the actual library. Consult the
documentation for the client library you're using to determine if and how this might be supported.
Libraries supporting the Mixed Reality Authentication are coming soon.
This project welcomes contributions and suggestions. Most contributions require you to agree to a Contributor License Agreement (CLA) declaring that you have the right to, and actually do, grant us the rights to use your contribution. For details, visit https://cla.microsoft.com.
When you submit a pull request, a CLA-bot will automatically determine whether you need to provide a CLA and decorate the PR appropriately (e.g., label, comment). Simply follow the instructions provided by the bot. You will only need to do this once across all repos using our CLA.
This project has adopted the Microsoft Open Source Code of Conduct. For more information see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.
FAQs
Package Description
We found that azure.mixedreality.authentication demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 2 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
/Security News
A RubyGems malware campaign used 60 malicious packages posing as automation tools to steal credentials from social media and marketing tool users.

Security News
The CNA Scorecard ranks CVE issuers by data completeness, revealing major gaps in patch info and software identifiers across thousands of vulnerabilities.

Research
/Security News
Two npm packages masquerading as WhatsApp developer libraries include a kill switch that deletes all files if the phone number isn’t whitelisted.