
Research
PyPI Package Impersonates SymPy to Deliver Cryptomining Malware
Malicious PyPI package sympy-dev targets SymPy users, a Python symbolic math library with 85 million monthly downloads.
aquilax
Advanced tools
Enterprise-Grade Application Security Testing from Your Terminal
Installation • Quick Start • Features • Documentation • Support
AquilaX CLI is a professional command-line tool that integrates with the AquilaX Application Security Platform. It helps developers and security teams find and fix security issues early in the development process, right from their terminal or CI/CD pipeline.
Whether you're a developer checking code before commit, a security professional running automated scans, or a DevOps engineer integrating security into pipelines, AquilaX CLI provides enterprise-level security scanning with an easy-to-use interface.
Scan your code for various security vulnerabilities with specialized scanners:
pip install aquilax
git clone https://github.com/AquilaX-AI/AquilaX-Client.git
cd AquilaX-Client
pip install -e .
aquilax --version
Login with your AquilaX API token:
aquilax login YOUR_API_TOKEN
For on-premise installations:
aquilax login YOUR_API_TOKEN --server https://your-aquilax-instance.com
Set your default organization and group to streamline commands:
aquilax --set-org YOUR_ORG_ID
aquilax --set-group YOUR_GROUP_ID
Start a security scan with real-time monitoring:
aquilax scan https://github.com/your-org/your-repo --sync
Authenticate with the AquilaX platform:
aquilax login <token> [--server <url>]
Options:
<token> - Your AquilaX API authentication token--server - (Optional) Custom server URL for on-premise installations (default: https://aquilax.ai)Example:
aquilax login eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9...
aquilax login my_token --server https://aquilax.mycompany.com
Remove stored authentication credentials:
aquilax logout
Configure your default organization ID:
aquilax --set-org <org_id>
Configure your default group ID:
aquilax --set-group <group_id>
Initiate a comprehensive security scan on a Git repository:
aquilax scan <git_uri> [options]
Options:
| Option | Description | Default |
|---|---|---|
--scanners | List of scanners to use | All 8 scanners |
--branch | Git branch to scan | main |
--sync | Enable real-time monitoring | Disabled |
--format | Output format (json or table) | table |
Examples:
# Basic scan with all scanners
aquilax scan https://github.com/myorg/myrepo
# Scan specific branch with real-time updates
aquilax scan https://github.com/myorg/myrepo --branch develop --sync
# Run only specific scanners
aquilax scan https://github.com/myorg/myrepo --scanners secret_scanner sast_scanner
# Output results as JSON
aquilax scan https://github.com/myorg/myrepo --format json
Specialized scan command optimized for CI/CD pipelines:
aquilax ci-scan <git_uri> [options]
Options:
| Option | Description | Default |
|---|---|---|
--org-id | Organization ID (overrides default) | From config |
--group-id | Group ID (overrides default) | From config |
--branch | Git branch to scan | main |
--sync | Enable real-time monitoring | Disabled |
--fail-on-vulns | Fail pipeline if any vulnerabilities found | Disabled |
--format | Output format (json or table) | table |
--output-dir | Directory for PDF reports | Current directory |
--save-pdf | Save PDF report locally | Disabled |
CI/CD Examples:
# Basic CI/CD scan
aquilax ci-scan https://github.com/myorg/myrepo
# Fail build if vulnerabilities exceed thresholds
aquilax ci-scan https://github.com/myorg/myrepo --fail-on-vulns
# CI/CD with custom org/group and JSON output
aquilax ci-scan https://github.com/myorg/myrepo \
--org-id 507f1f77bcf86cd799439011 \
--group-id 507f1f77bcf86cd799439012 \
--format json
GitLab CI Example:
security_scan:
stage: test
script:
- pip install aquilax
- aquilax login $AQUILAX_TOKEN
- aquilax ci-scan $CI_REPOSITORY_URL --branch $CI_COMMIT_BRANCH --fail-on-vulns
GitHub Actions Example:
- name: AquilaX Security Scan
run: |
pip install aquilax
aquilax login ${{ secrets.AQUILAX_TOKEN }}
aquilax ci-scan ${{ github.repository }} --fail-on-vulns
Fetch detailed results from a completed scan:
aquilax pull <scan_id> [options]
Options:
| Option | Description | Default |
|---|---|---|
--org-id | Organization ID | From config |
--group-id | Group ID | From config |
--format | Output format (json or table) | table |
Example:
aquilax pull 507f1f77bcf86cd799439013 --format table
List all organizations accessible to your account:
aquilax get orgs
Output:
Organizations List:
+-------------------+---------------------------+
| Organization Name | Organization ID |
+===================+===========================+
| My Company | 507f1f77bcf86cd799439011 |
| Test Org | 507f1f77bcf86cd799439014 |
+-------------------+---------------------------+
List all groups within an organization:
aquilax get groups [--org-id <org_id>]
If --org-id is not provided, uses the default organization from your configuration.
Retrieve comprehensive details about a specific scan:
aquilax get scan-details --scan-id <scan_id> [options]
Options:
| Option | Description | Default |
|---|---|---|
--org-id | Organization ID | From config |
--group-id | Group ID | From config |
--format | Output format (json or table) | table |
Example:
aquilax get scan-details --scan-id 507f1f77bcf86cd799439013
Beautiful, color-coded console output:
╭─────────────────┬──────────────────────┬─────────────────────────┬──────────┬─────────┬────────╮
│ Scanner │ Path │ Vulnerability │ Severity │ CWE │ OWASP │
├─────────────────┼──────────────────────┼─────────────────────────┼──────────┼─────────┼────────┤
│ secret_scanner │ config/database.yml │ Hardcoded API Key │ HIGH │ CWE-798 │ A02 │
│ sast_scanner │ app/controllers/... │ SQL Injection │ CRITICAL │ CWE-89 │ A03 │
│ sca_scanner │ package.json │ Vulnerable Dependency │ MEDIUM │ CWE-937 │ A06 │
╰─────────────────┴──────────────────────┴─────────────────────────┴──────────┴─────────┴────────╯
Machine-readable output for automation and integration:
aquilax scan https://github.com/myorg/myrepo --format json
{
"scan_id": "507f1f77bcf86cd799439013",
"status": "COMPLETED",
"findings": [
{
"scanner": "secret_scanner",
"path": "config/database.yml",
"vuln": "Hardcoded API Key",
"severity": "HIGH",
"cwe": ["CWE-798"],
"owasp": ["A02"]
}
]
}
AquilaX CLI enforces security policies configured at the group level in your AquilaX platform. Scans will fail if vulnerabilities exceed defined thresholds.
Threshold Categories:
Example Policy:
Security Policy Thresholds:
- total: 10
- CRITICAL: 0
- HIGH: 2
- MEDIUM: 5
- LOW: 10
If thresholds are exceeded:
Thresholds exceeded: CRITICAL (2) > 0; HIGH (5) > 2
Pipeline failed due to security policy violations.
You can configure AquilaX CLI using environment variables:
export AQUILAX_SERVER="https://your-instance.com"
Authentication and defaults are stored at:
~/.aquilax/config.json%USERPROFILE%\.aquilax\config.jsonExample configuration:
{
"apiToken": "your_api_token",
"baseUrl": "https://aquilax.ai",
"org_id": "507f1f77bcf86cd799439011",
"group_id": "507f1f77bcf86cd799439012"
}
Pre-Commit Security Checks:
# Add to .git/hooks/pre-commit
aquilax scan $(git config --get remote.origin.url) --branch $(git branch --show-current)
Jenkins Pipeline:
stage('Security Scan') {
steps {
sh 'pip install aquilax'
sh 'aquilax login ${AQUILAX_TOKEN}'
sh 'aquilax ci-scan ${GIT_URL} --fail-on-vulns --format json > scan-results.json'
}
}
Azure DevOps:
- task: CmdLine@2
inputs:
script: |
pip install aquilax
aquilax login $(AQUILAX_TOKEN)
aquilax ci-scan $(Build.Repository.Uri) --fail-on-vulns
Scheduled Scans:
#!/bin/bash
# Scan all repositories in your organization
for repo in $(cat repos.txt); do
aquilax scan $repo --sync --format json > "scans/$(basename $repo).json"
done
Problem: ModuleNotFoundError: No module named 'aquilax'
Solution: Ensure the package is installed and your virtual environment is activated:
pip install aquilax
source venv/bin/activate # Linux/Mac
venv\Scripts\activate # Windows
Problem: 401 Unauthorized when running commands
Solution: Verify your API token is correct and has necessary permissions:
aquilax logout
aquilax login YOUR_CORRECT_TOKEN
Problem: Scan fails with "Repository not accessible"
Solution:
--branch your-branch-nameProblem: Thresholds exceeded errors
Solution:
--format json to get detailed findings for remediationProblem: Cannot connect to AquilaX server
Solution:
# For on-premise installations, verify server URL
aquilax login YOUR_TOKEN --server https://your-correct-url.com
# Check if server is accessible
curl https://your-aquilax-server.com/health
We welcome contributions to AquilaX CLI! Here's how you can help:
git checkout -b feature/amazing-feature)git commit -m 'Add amazing feature')git push origin feature/amazing-feature)git clone https://github.com/AquilaX-AI/AquilaX-Client.git
cd AquilaX-Client
pip install -e .
This project is licensed under the Apache License 2.0. See the LICENSE file for details.
Need help? We're here for you!
✅ Complete Security Coverage - Multiple specialized scanners in one tool
✅ Fast & Efficient - Quick scans without slowing down your workflow
✅ Works Everywhere - Compatible with any Git repository
✅ Automation Ready - Perfect for CI/CD pipelines
✅ Easy to Use - Clean, understandable output
✅ Enterprise Trusted - Used by security teams worldwide
Made with ❤️ by the AquilaX Team
FAQs
AquilaX CLI Client
We found that aquilax demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 2 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Malicious PyPI package sympy-dev targets SymPy users, a Python symbolic math library with 85 million monthly downloads.
Product
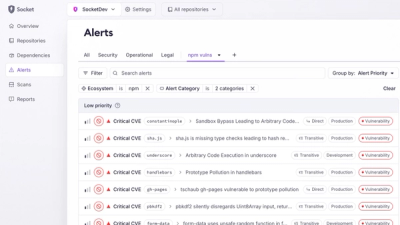
Create and share saved alert views with custom tabs on the org alerts page, making it easier for teams to return to consistent, named filter sets.

Product
Socket’s Rust and Cargo support is now generally available, providing dependency analysis and supply chain visibility for Rust projects.