



Author = https://martinmueller.dev
cdk-prowler
The current Prowler version is 2.10.0
An AWS CDK custom construct for deploying Prowler to your AWS Account. The following description about Prowler is taken from https://github.com/prowler-cloud/prowler
Prowler is a security tool to perform AWS security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. It contains all CIS controls listed here https://d0.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf and more than 100 additional checks that help on GDPR, HIPAA …
It generates security html results which are stored in an s3 bucket:
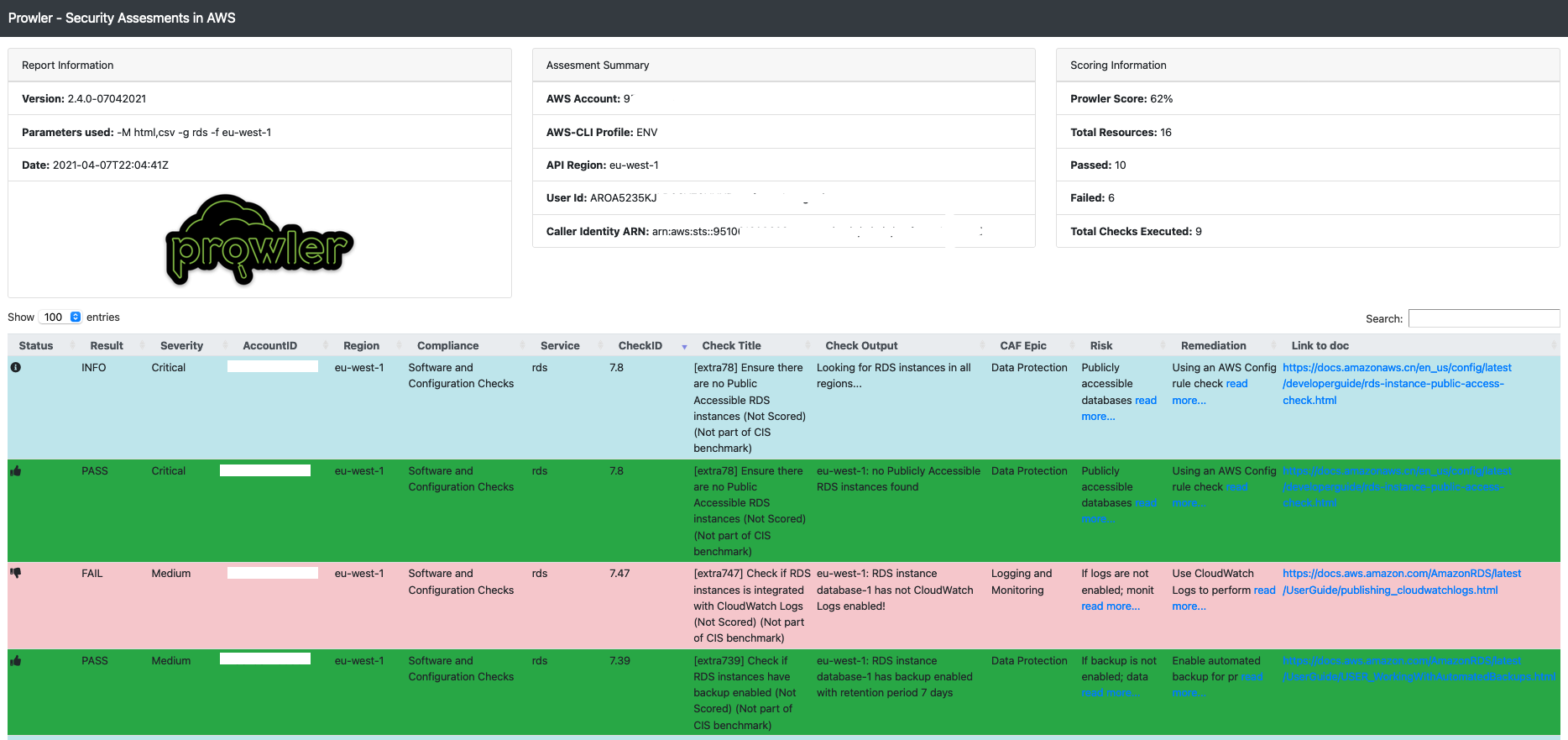
And in your Codebuild Report group:
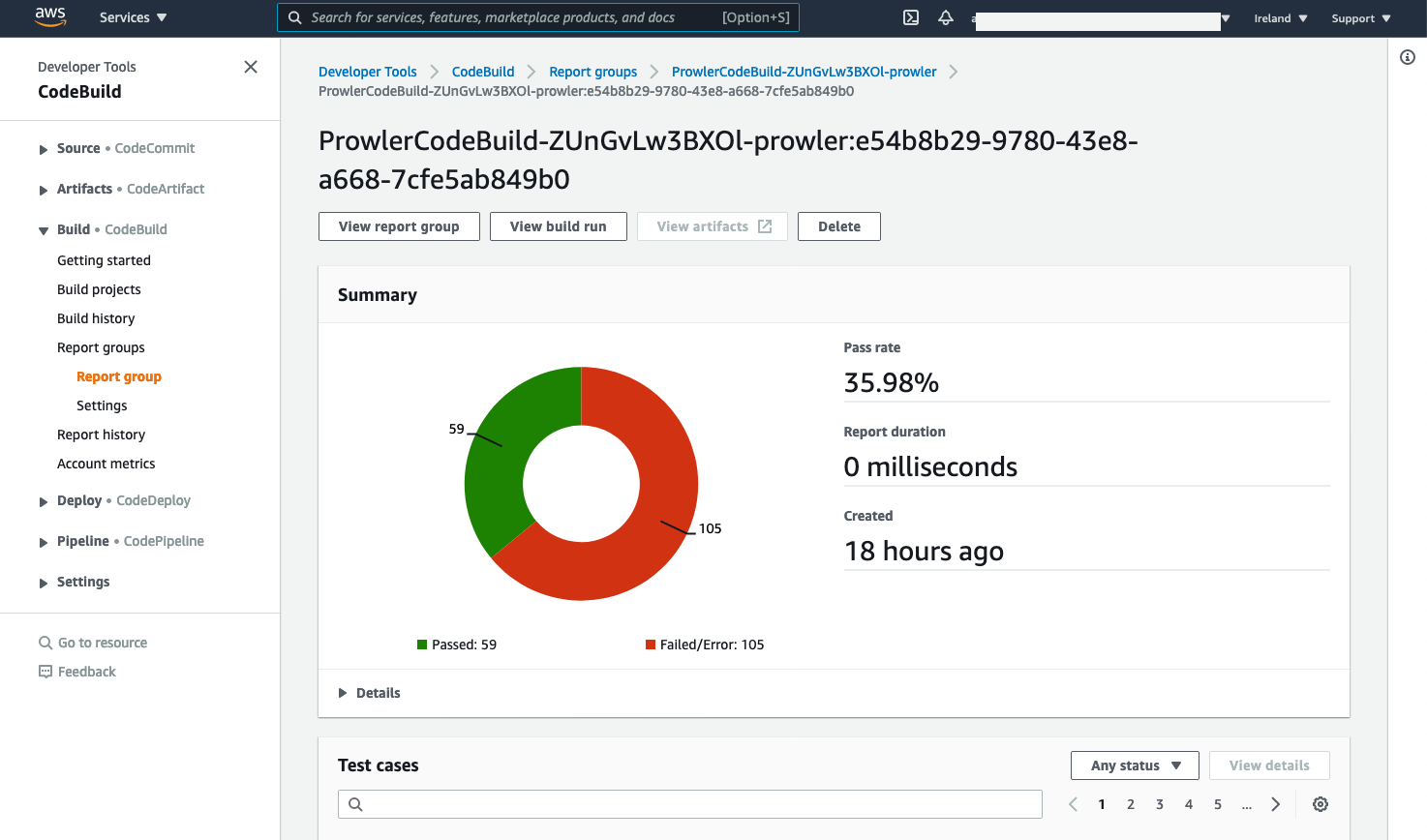
AWS AMI
If you just want to make the Prowler security checks in your account try my Prowler AWS Marketplace AMI. With just $1 Prowler will do over 180 security checks across a huge amount of AWS services in all your regions. Don't forget the terminate the Ec2 instance when the Prowler stack got created for not paying more than that $1 :).
With buying the AMI you support my on my passion for creating open source products like this cdk-prowler construct. Furthermore you enable me to work on future features like mentioned in the Planned Features section. Thank you so much :) !
Example
import { ProwlerAudit } from 'cdk-prowler';
...
const app = new App();
const stack = new Stack(app, 'ProwlerAudit-stack');
new ProwlerAudit(stack, 'ProwlerAudit');
Architect diagram

Curious how I did the diagram? Have a look here https://martinmueller.dev/cdk-dia-eng .
cdk-prowler Properties
cdk-prowler supports some properties to tweak your stack. Like for running a Cloudwatch schedule to regualary run the Prowler scan with a defined cron expression.
API Reference
Constructs
ProwlerAudit
Creates a CodeBuild project to audit an AWS account with Prowler and stores the html report in a S3 bucket.
This will run onece at the beginning and on a schedule afterwards. Partial contribution from https://github.com/stevecjones
Initializers
import { ProwlerAudit } from 'cdk-prowler'
new ProwlerAudit(parent: Stack, id: string, props?: ProwlerAuditProps)
parentRequired
idRequired
propsOptional
Properties
codebuildProjectRequired
public readonly codebuildProject: Project;
enableSchedulerRequired
public readonly enableScheduler: boolean;
logsRetentionInDaysRequired
public readonly logsRetentionInDays: RetentionDays;
prowlerOptionsRequired
public readonly prowlerOptions: string;
prowlerSchedulerRequired
public readonly prowlerScheduler: string;
prowlerVersionRequired
public readonly prowlerVersion: string;
serviceNameRequired
public readonly serviceName: string;
Structs
ProwlerAuditProps
Initializer
import { ProwlerAuditProps } from 'cdk-prowler'
const prowlerAuditProps: ProwlerAuditProps = { ... }
additionalS3CopyArgsOptional
public readonly additionalS3CopyArgs: string;
An optional parameter to add to the S3 bucket copy command.
allowlistOptional
public readonly allowlist: Asset;
An Prowler-specific Allowlist file.
If a value is provided then this is passed to Prowler on runs using the '-w' flag.
If no value is provided, the -w parameter is not used. If you provide an asset that is zipped, it must contain
an 'allowlist.txt' file which will be passed to Prowler.
enableSchedulerOptional
public readonly enableScheduler: boolean;
- Type:
boolean
- Default: false
enables the scheduler for running prowler periodically.
Together with prowlerScheduler.
logsRetentionInDaysOptional
public readonly logsRetentionInDays: RetentionDays;
Specifies the number of days you want to retain CodeBuild run log events in the specified log group.
Junit reports are kept for 30 days, HTML reports in S3 are not deleted
prowlerOptionsOptional
public readonly prowlerOptions: string;
- Type:
string
- Default: '-M text,junit-xml,html,csv,json'
Options to pass to Prowler command, make sure at least -M junit-xml is used for CodeBuild reports.
Use -r for the region to send API queries, -f to filter only one region, -M output formats, -c for comma separated checks, for all checks do not use -c or -g, for more options see -h. For a complete assessment use "-M text,junit-xml,html,csv,json", for SecurityHub integration use "-r region -f region -M text,junit-xml,html,csv,json,json-asff -S -q"
prowlerSchedulerOptional
public readonly prowlerScheduler: string;
- Type:
string
- Default: 'cron(0 22 ** ? *)'
The time when Prowler will run in cron format.
Default is daily at 22:00h or 10PM 'cron(0 22 ** ? *)', for every 5 hours also works 'rate(5 hours)'. More info here https://docs.aws.amazon.com/AmazonCloudWatch/latest/events/ScheduledEvents.html.
prowlerVersionOptional
public readonly prowlerVersion: string;
- Type:
string
- Default: 2.5.0
Specifies the concrete Prowler version.
reportBucketOptional
public readonly reportBucket: IBucket;
An optional S3 bucket to store the Prowler reports.
reportBucketPrefixOptional
public readonly reportBucketPrefix: string;
An optional prefix for the report bucket objects.
serviceNameOptional
public readonly serviceName: string;
- Type:
string
- Default: : prowler
Specifies the service name used within component naming.
Cross Account Buckets
By providing your own Bucket you can have the CodeBuild project drop the Prowler results in another account. Make sure that you have your Bucket policy setup to allow the account running the Prowler reports access to writing those record.
Additionally, you will probably want to provide an additionalS3CopyArgs: '--acl bucket-owner-full-control' to ensure that those object can be read by the account owner.
Planned Features
Architecture

Misc
yes | yarn destroy && yarn deploy --require-approval never
Rerun Prowler on deploy
yarn deploy --require-approval never -c reRunProwler=true
Thanks To








