gitlab-ci-verify













Validate and lint your gitlab ci files using ShellCheck, the Gitlab API, curated checks or even build your own checks
Features
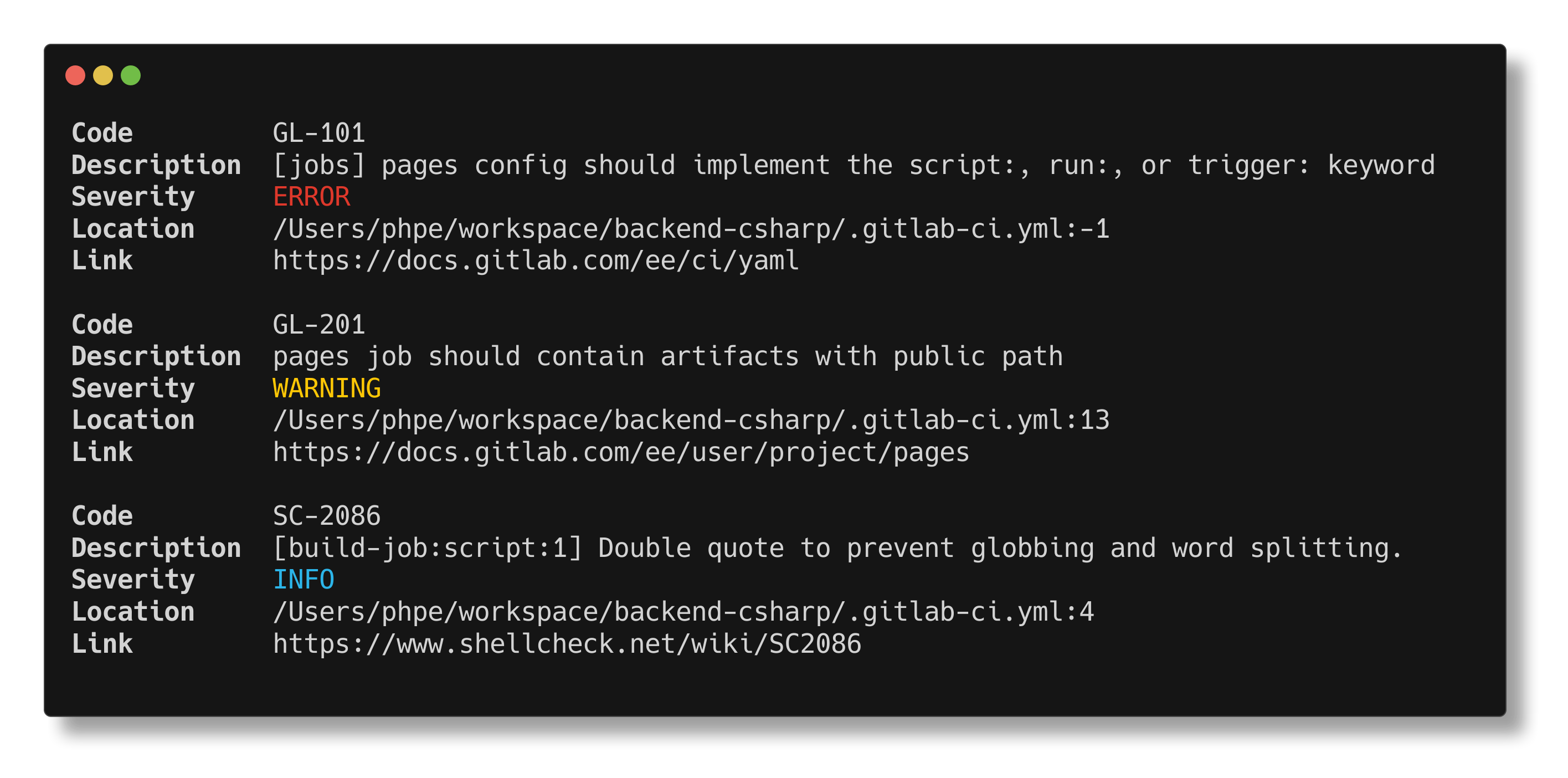
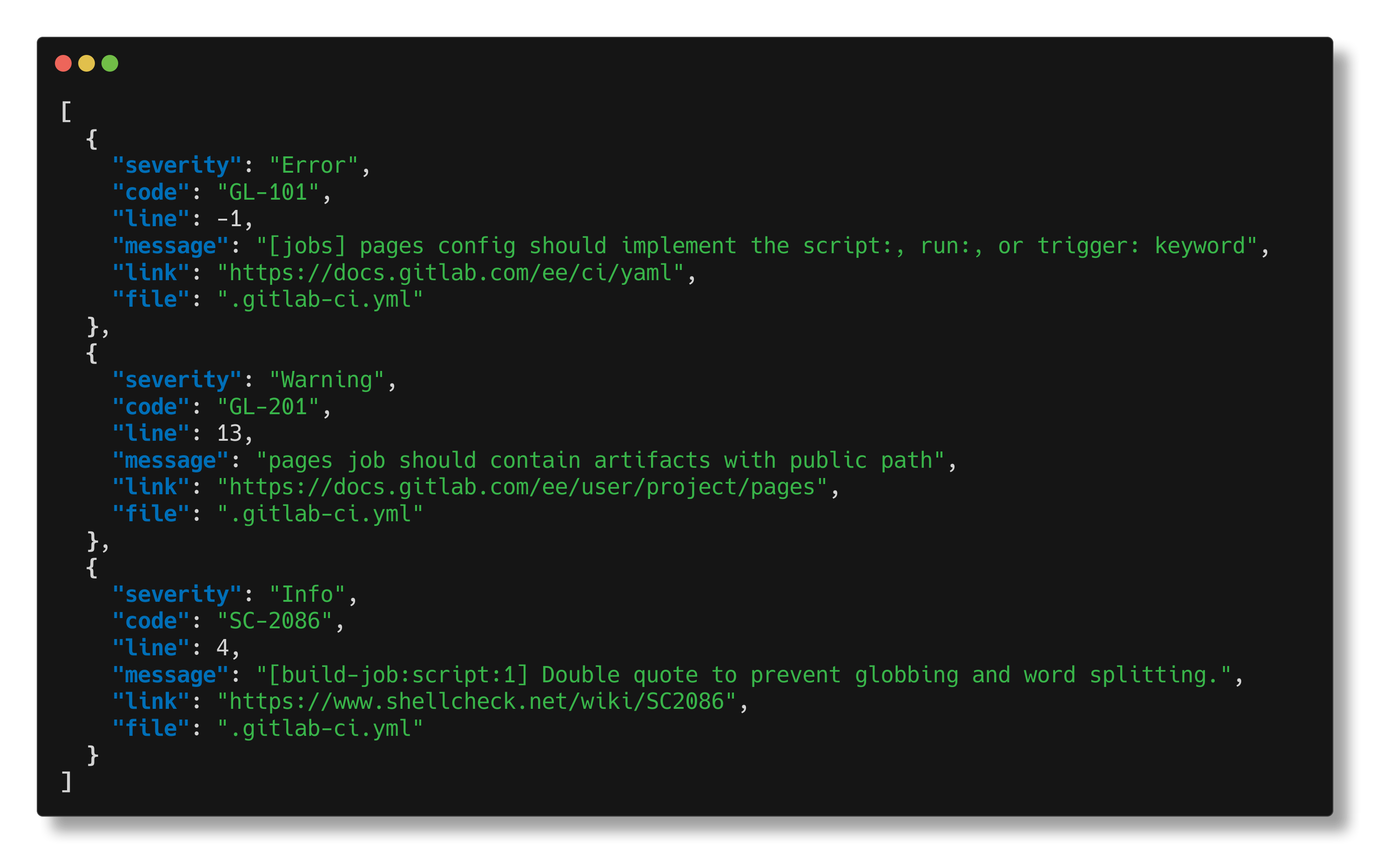
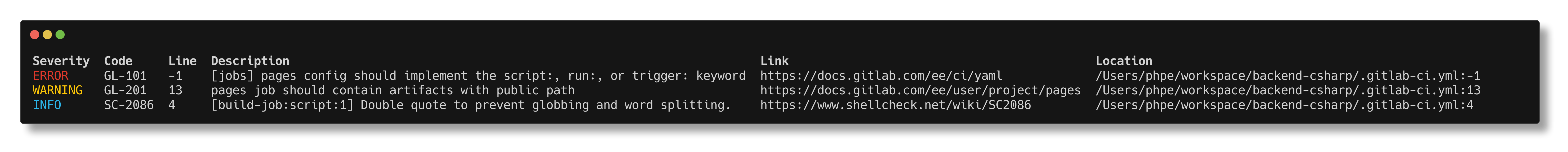
Example output
Installation
Install with pipx
Using pipx you can just use the following command use gitlab-ci-verify as it is:
pipx install gitlab-ci-verify-bin
Install as library using pip
If you want to use it directly using the subprocess module you can install it with pip:
pip install gitlab-ci-verify
And use the package like this:
from gitlab_ci_verify import verify_file
valid, findings = verify_file("/path/to/repo")
valid, findings = verify_file("/path/to/repo", "include.yml")
print(f"Valid: {valid}")
print(f"Findings: {findings}")
Also see the python wrapper documentation
Manual
Linux (64-bit)
curl -LO https://github.com/timo-reymann/gitlab-ci-verify/releases/download/$(curl -Lso /dev/null -w %{url_effective} https://github.com/timo-reymann/gitlab-ci-verify/releases/latest | grep -o '[^/]*$')/gitlab-ci-verify_linux-amd64 && \
chmod +x gitlab-ci-verify_linux-amd64 && \
sudo mv gitlab-ci-verify_linux-amd64 /usr/local/bin/gitlab-ci-verify
Darwin (Intel)
curl -LO https://github.com/timo-reymann/gitlab-ci-verify/releases/download/$(curl -Lso /dev/null -w %{url_effective} https://github.com/timo-reymann/gitlab-ci-verify/releases/latest | grep -o '[^/]*$')/gitlab-ci-verify_darwin-amd64 && \
chmod +x gitlab-ci-verify_darwin-amd64 && \
sudo mv gitlab-ci-verify_darwin-amd64 /usr/local/bin/gitlab-ci-verify
Windows
Download the latest release for Windows and put in
your PATH.
Install with go
go install github.com/timo-reymann/gitlab-ci-verify@latest
Supported platforms
The following platforms are supported (and have prebuilt binaries /
ready to use integration):
- Linux
- Darwin
- Windows
- pre-commit (x86 & ARM)
- Docker (x86 & ARM)
Where to find the latest release for your platform
Binaries
Binaries for all of these can be found on
the latest release page.
Docker
For the docker image, check the docker hub.
Usage
Command Line
gitlab-ci-verify --help
Containerized
docker run --rm -it -v $PWD:/workspace -e GITLAB_TOKEN="your token" timoreymann/gitlab-ci-verify
As pre-commit hook
- repo: https://github.com/timo-reymann/gitlab-ci-verify
rev: v2.1.12
hooks:
- id: gitlab-ci-verify
Authentication with GitLab
The tool takes a few sources into consideration in the following order when authenticating with GitLab:
--gitlab-token commandline flag- netrc in your home folder
- Vault token specified via
--gitlab-token vault://<path>#<field> with environment variable VAULT_ADDR set to base
url for
vault, and either VAULT_TOKEN set or ~/.vault-token present
GITLAB_TOKEN environment variable
For the project detection, all git remote URLs of the repository are tried, and the first URL that returns a valid API
response is used. In case you cloned via SSH it tries to convert it to the HTTPs host automatically. If the ssh URL
differs from the HTTPs url you should specify it manually using the --gitlab-base-url, without protocol e.g.
--gitlab-base-url git.example.com
Ignoring findings
You can ignore findings by adding comments in the format # gitlab-ci-verify: ignore:<check_id> to your CI YAML files.
This works in several places:
- In the same line as the finding:
pages:
artifacts: {}
- In the line above the finding:
pages:
artifacts: {}
- Globally for the file of the finding:
pages:
artifacts: {}
Writing custom policies
You can write custom policies for your projects
using Rego.
Find more information in the dedicated documentation for custom policies.
Motivation
Unfortunately, GitLab didn't provide a tool to validate CI configuration for quite a while.
Now that changed with the glab CLI providing glab ci lint but it is quite limited and under the hood just calls the
new CI Lint API.
Throughout the years quite some tools evolved, but most of them are either outdated, painful to use or install, and
basically also provide the lint functionality from the API.
As most of the logic in pipelines is written in shell scripts via the *script attributes these are lacking completely
from all tools out there as well as the official lint API.
The goal of gitlab-ci-verify is to provide the stock CI Lint functionality plus shellcheck.
Completed in the future some
rules to lint that common patterns are working as intended by GitLab
and void them from being pushed and leading to unexpected behavior.
Contributing
I love your input! I want to make contributing to this project as easy and transparent as possible, whether it's:
- Reporting a bug
- Discussing the current state of the configuration
- Submitting a fix
- Proposing new features
- Becoming a maintainer
To get started please read the Contribution Guidelines.
Development
Requirements
Test
make test-coverage-report
Build
make build
Credits
This whole project wouldn't be possible with the great work of the
following libraries/tools: