
Security News
VulnCon 2025: NVD Scraps Industry Consortium Plan, Raising Questions About Reform
At VulnCon 2025, NIST scrapped its NVD consortium plans, admitted it can't keep up with CVEs, and outlined automation efforts amid a mounting backlog.
pip install hek
import hek
# get device current username
user = hek.system.username()
# print username
print(user)
import hek
os_name = hek.system.oname()
print(os_name)
from hek import system
# new file path
path = "dog.jpg"
# file url
url = "https://example/dog_picure.jpg"
# download content
result = system.download_content(url=url, path=path)
# print result
print(result)
import hek
# process name
name = "chrome.exe"
# kill process
res = hek.system.process.kill_process(name=name)
print(res)
from hek import system
# targeted process name\user
name = "chrome.exe"
# will return process PID\ID
name = system.process.getnamebypid(name=pid)
# print process PID\ID
print(name)
from hek import system
# targeted process PID\id
pid = "2779"
# will return process name
name = system.process.getnamebypid(pid=pid)
# print process name
print(name)
import hek
# request tor session
tor_session = hek.tor.get_session()
# tor get request
result = tor_session.get("http://httpbin.org/ip").text
# print result
print(result)
import hek
# adding host manually
host = "127.0.0.1:9050"
# request session
session = hek.tor.get_session(host=host)
# request your proxy identity..
identity = session.identity(host=host)
# print proxy identity
print(identity)
import hek
result = hek.proxy.checkproxy( # function to check if proxy is working
url="https://github.com/", # targeted url
user_agent="Mozilla/5.0", # user agent
proxy="185.61.94.65:61616" # HTTP/HTTPS proxy
)
if "Working" in result: # It'll return Working if It's alive end exception if not
print("Alive proxy")
It'll return Working if It's alive end exception if not
import hek
url = "github.com" # targeted url
ip = hek.ipstuff.siteip(url) # grap ip by url
print(ip)
import hek
ip = "192.168.0.1" # targeted device ip address
port = 80 # targeted port
result = hek.ipstuff.portscan(ip=ip, port=port, timeout=3) # checking if opened port or not
if result == True:
print("Opened port.")
elif result == False:
print("Closed port.")
import hek
ip = "192.168.0.1" # targeted device ip address
result = hek.ipstuff.checkssh(ip) # checking if device is shh by the device ip
if result == True:
print("is ssh")
elif result == False:
print("isn't ssh")
import hek
ip = "192.168.0.1" # targeted device ip address
result = hek.ipstuff.checkrdp(ip) # checking if device is rdp by the device ip.
if result == True:
print("is rdp")
elif result == False:
print("isn't rdp")
import hek
ip = "192.168.0.1" # targeted ip address
result = hek.ipstuff.checkip(ip) # checking if ip exist, It'll return True is exist and False if not.
if result == True:
print("ip exist")
elif result == False:
print("ip doesn't exist")
It'll return True is exist and False if not.
import hek
# get ip
ip = hek.ipstuff.myip(find="query")
# print ip
print(ip)
you could get your ip information by removing find="query" also you can change query and get other info about your ip.
import hek
# server ip
ip = "192.168.0.1"
# targeted port
port = 80
# check
result = hek.server.portscan(ip=ip, port=port)
print(result)
import hek
# server ip
ip = "192.168.0.1"
# targeted port
port = 430
# check
result = hek.server.get_banner(address=ip, port=port)
print(result)
import hek
# server ip
ip = "192.168.0.1"
# server port
port = 80
# set server data
server = hek.server.set_socket(host=ip, port=port)
# connect to server
r = server.connect()
print(f"connected: {r}")
import hek
# server ip
ip = "192.168.0.1"
# server port
port = 80
# set server data
server = hek.server.set_socket(host=ip, port=port)
# connect to server
r = server.connect()
print(f"connected: {r}")
# the packet
packet = "hi im packet"
# send packet
result = server.sendpacket()
print(result)
data = server.recv(bufsize=1048)
print(data)
server.close()
from hek import server
# get the server value
server = server.socket()
# create socket
sock = server.socket()
# connect to a server
result = server.connect(sock, host="192.168.0.1", port=80)
# connection result True if connected
print(result)
# the packet
packet = "im a packet"
# send packet
result = server.sendpacket(sock, packet=packet, host="192.168.0.1", port=80)
print(result)
# receive data
server.recv(sock, bufsize=1048)
# close connection
server.close(sock)
import hek, threading
# start sniffing network
def sniff():
hek.network.arp.start_arp(
# your interface mostly It'll be wlan0
interface="wlan0",
# ip of the router that the device is connected to
router="192.168.0.1",
# device ip address that you want to sniff
device="192.168.0.112"
)
# this function will run wireshark according to the entered data
def monitor_traffic():
hek.wireshark.monitor_device(
# your interface mostly It'll be wlan0
interface="wlan0",
# device ip address
device="192.168.0.112"
)
threading.Thread(target=monitor_traffic).start() # run wireshark
threading.Thread(target=sniff).start() # start sniffing
import hek
# start sniffing network
def sniff():
hek.network.arp.start_arp(
# your interface mostly It'll be wlan0
interface="wlan0",
# ip of the router that the device is connected to
router="192.168.0.1",
# device ip address that you want to sniff
device="192.168.0.112"
)
sniff()
This function is for linux also requires wifi adapter.
import hek
# connect to wifi
result = hek.wifi.connect(ssid="Wifi ssid/Name", # wifi ssid/name
password="wifi-password" # wifi password
)
# connection result
print(result)
This function for linux.
import hek
# Start monitor mode
result = hek.net.monitor_start(name="wlan0")
# Output
print(result)
This function for linux.
import hek
# stop monitor mode
result = hek.net.monitor_stop(name="wlan0mon")
# Output
print(result)
import hek
data = hek.Image.extracexif(filename="hek.jpg") # grab exif data
print(data) # print data
import hek
hek.screen.screenshot(filename="test.png")
import hek
hek.webcam.webcamshot(filename="test.png")
import hek
hek.screen.capture_video(filename="filename.avi", seconds=5)
import hek
hek.webcam.capture_video(filename="webname.avi", seconds=3)
This program uses MIT license.
FAQs
A python library mostly used for pentesting and automate some tasks.
We found that hek demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
At VulnCon 2025, NIST scrapped its NVD consortium plans, admitted it can't keep up with CVEs, and outlined automation efforts amid a mounting backlog.
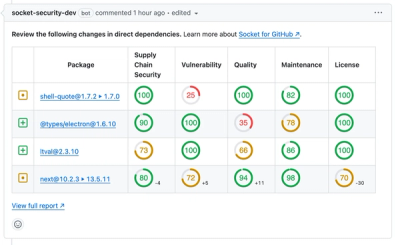
Product
We redesigned our GitHub PR comments to deliver clear, actionable security insights without adding noise to your workflow.
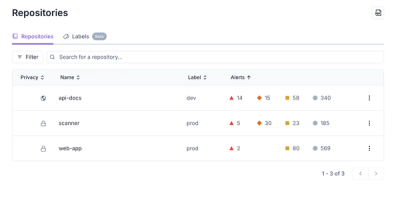
Product
Our redesigned Repositories page adds alert severity, filtering, and tabs for faster triage and clearer insights across all your projects.