
Algo-trading was 😵💫, we made it 🤩
Jesse





Jesse is an advanced crypto trading framework that aims to simplify researching and defining YOUR OWN trading strategies for backtesting, optimizing, and live trading.
What is Jesse?
Watch this video to get a quick overview of Jesse:

Why Jesse?
In short, Jesse is more accurate than other solutions, and way more simple.
In fact, it is so simple that in case you already know Python, you can get started today, in matter of minutes, instead of weeks and months.
Key Features
- 📝 Simple Syntax: Define both simple and advanced trading strategies with the simplest syntax in the fastest time.
- 📊 Comprehensive Indicator Library: Access a complete library of technical indicators with easy-to-use syntax.
- 📈 Smart Ordering: Supports market, limit, and stop orders, automatically choosing the best one for you.
- ⏰ Multiple Timeframes and Symbols: Backtest and livetrade multiple timeframes and symbols simultaneously without look-ahead bias.
- 🔒 Self-Hosted and Privacy-First: Designed with your privacy in mind, fully self-hosted to ensure your trading strategies and data remain secure.
- 🛡️ Risk Management: Built-in helper functions for robust risk management.
- 📋 Metrics System: A comprehensive metrics system to evaluate your trading strategy's performance.
- 🔍 Debug Mode: Observe your strategy in action with a detailed debug mode.
- 🔧 Optimize Mode: Fine-tune your strategies using AI, without needing a technical background.
- 📈 Leveraged and Short-Selling: First-class support for leveraged trading and short-selling.
- 🔀 Partial Fills: Supports entering and exiting positions in multiple orders, allowing for greater flexibility.
- 🔔 Advanced Alerts: Create real-time alerts within your strategies for effective monitoring.
- 🤖 JesseGPT: Jesse has its own GPT, JesseGPT, that can help you write strategies, optimize them, debug them, and much more.
- 🔧 Built-in Code Editor: Write, edit, and debug your strategies with a built-in code editor.
- 📺 Youtube Channel: Jesse has a Youtube channel with screencast tutorials that go through example strategies step by step.
Dive Deeper into Jesse's Capabilities
Stupid Simple
Craft complex trading strategies with remarkably simple Python. Access 300+ indicators, multi-symbol/timeframe support, spot/futures trading, partial fills, and risk management tools. Focus on logic, not boilerplate.
class GoldenCross(Strategy):
def should_long(self):
short_ema = ta.ema(self.candles, 8)
long_ema = ta.ema(self.candles, 21)
return short_ema > long_ema
def go_long(self):
entry_price = self.price - 10
qty = utils.size_to_qty(self.balance*0.05, entry_price)
self.buy = qty, entry_price
self.take_profit = qty, entry_price*1.2
self.stop_loss = qty, entry_price*0.9
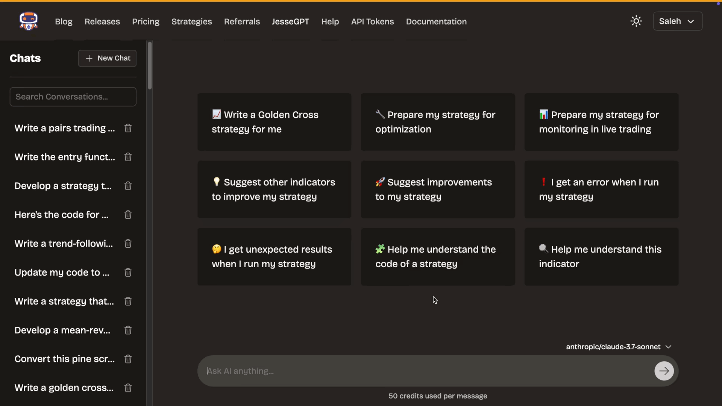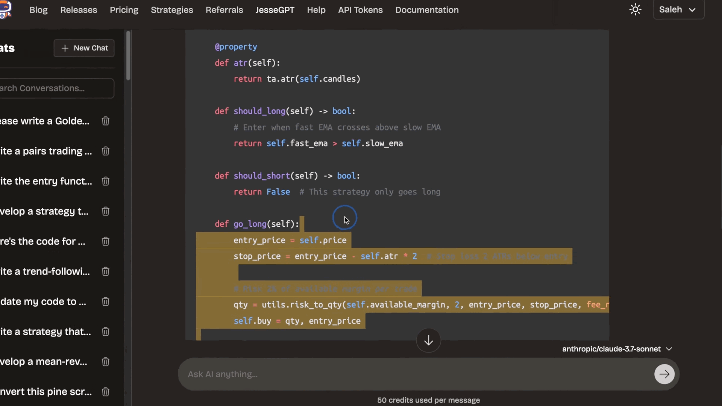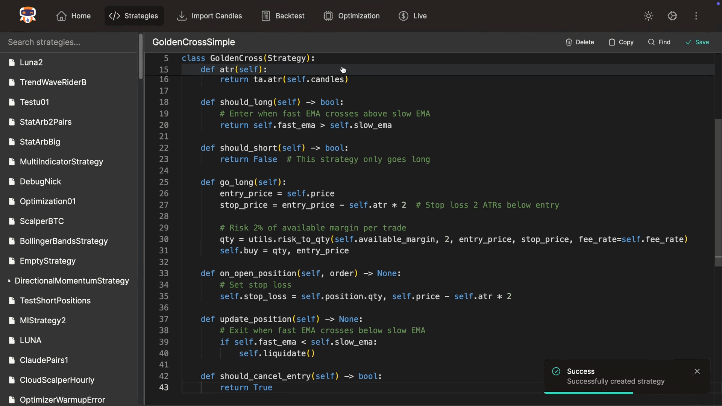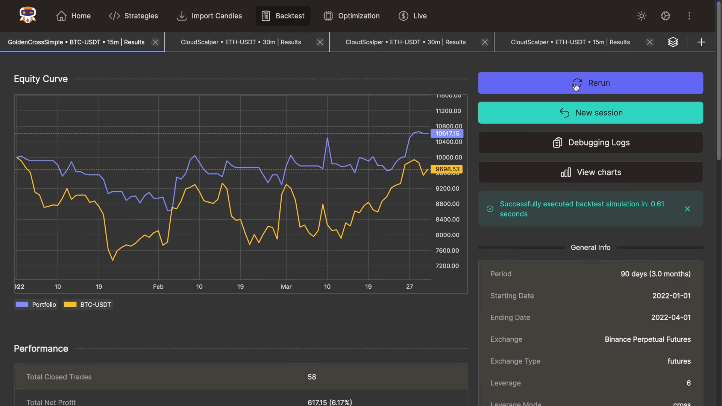
Backtest
Execute highly accurate and fast backtests without look-ahead bias. Utilize debugging logs, interactive charts with indicator support, and detailed performance metrics to validate your strategies thoroughly.
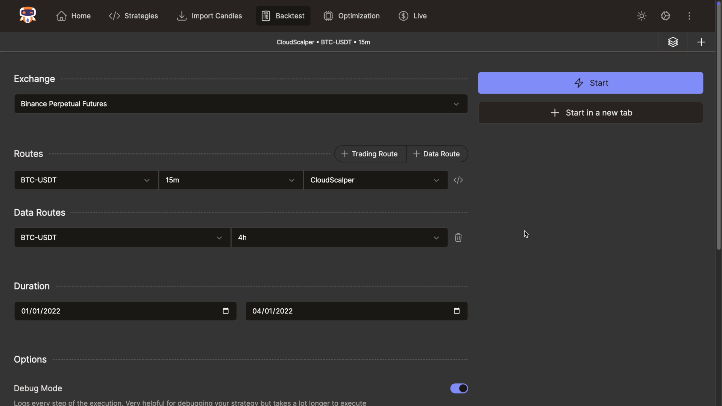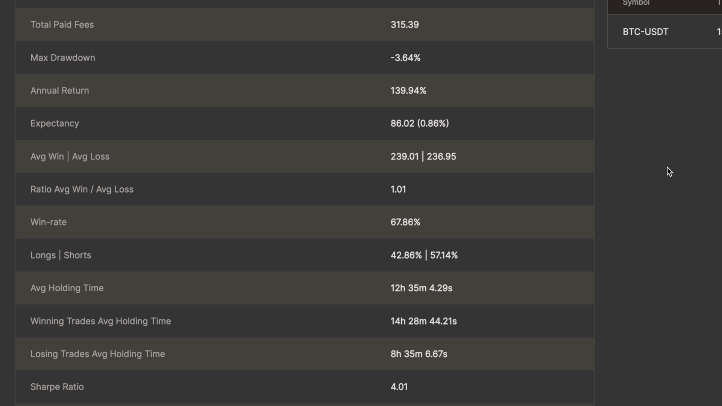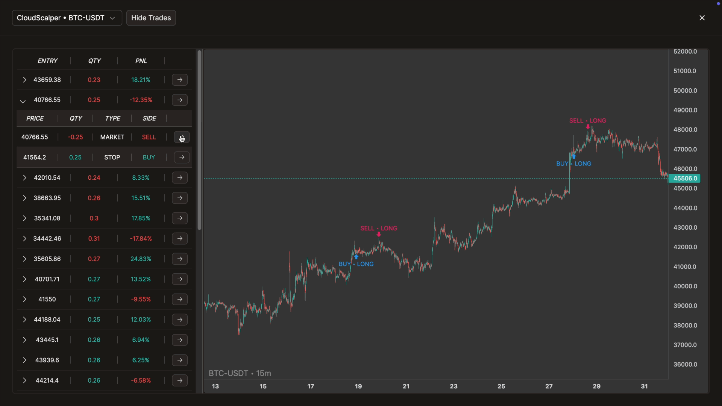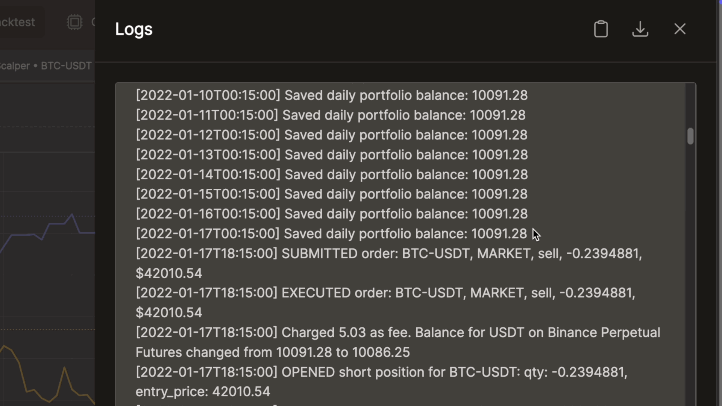
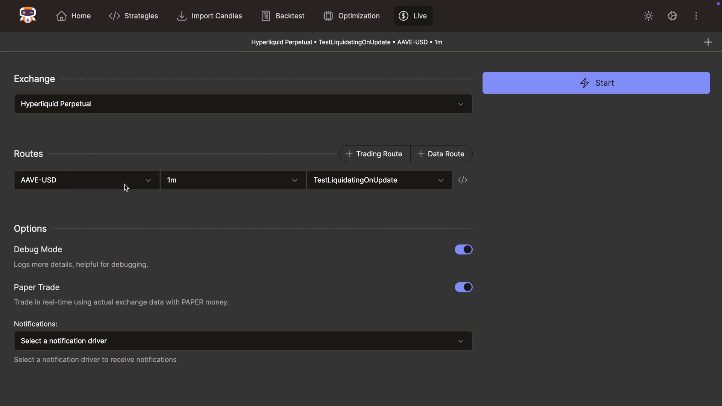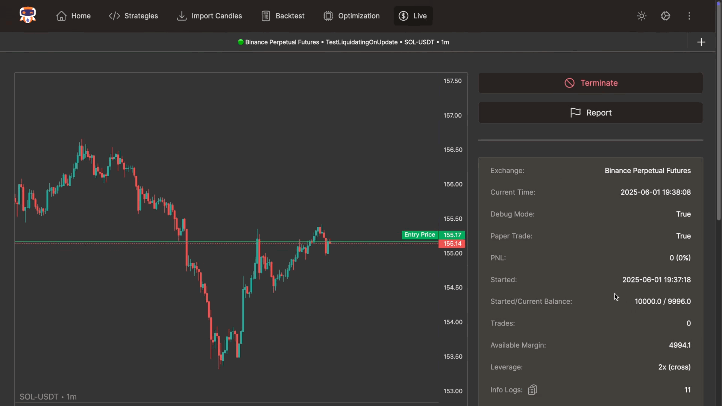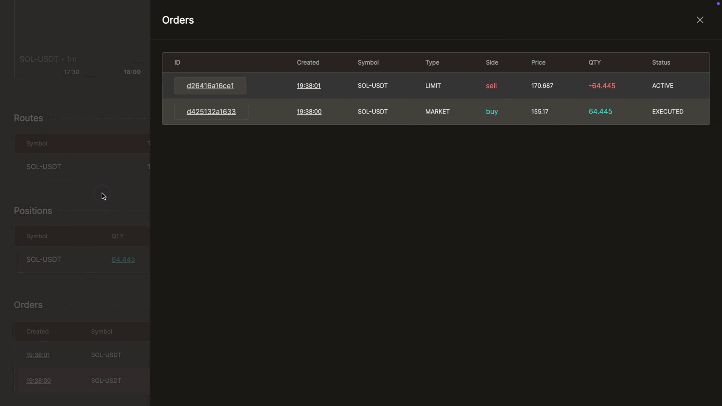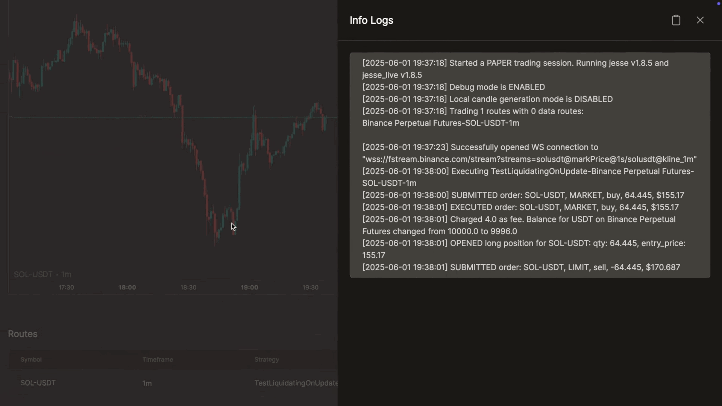
Live/Paper Trading
Deploy strategies live with robust monitoring tools. Supports paper trading, multiple accounts, real-time logs & notifications (Telegram, Slack, Discord), interactive charts, spot/futures, DEX, and a built-in code editor.
Benchmark
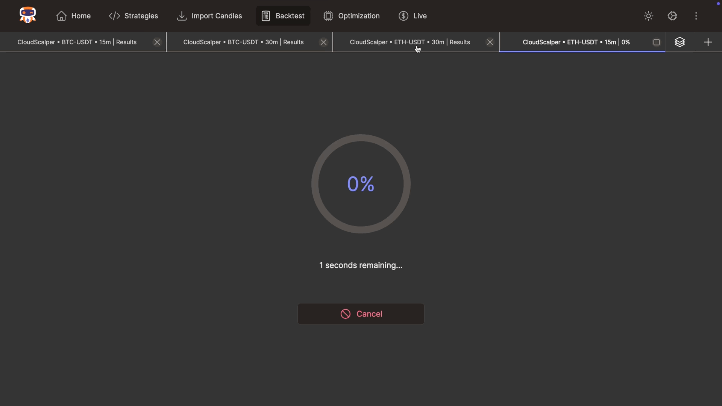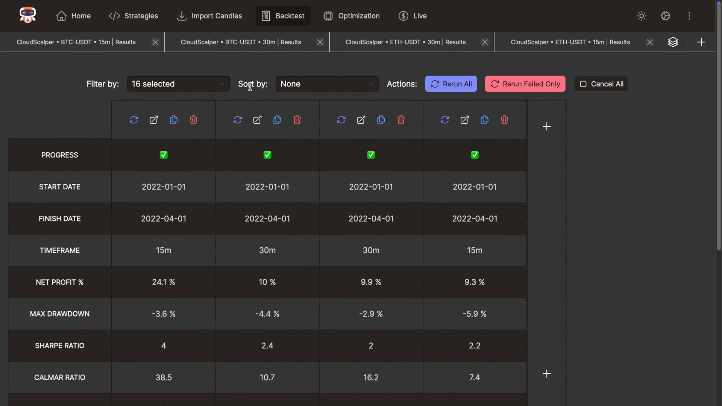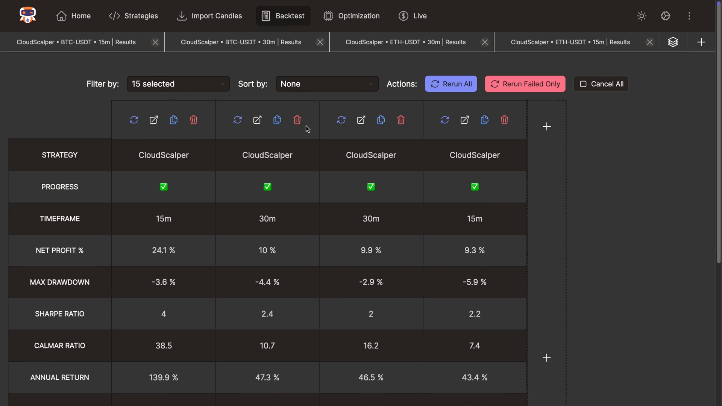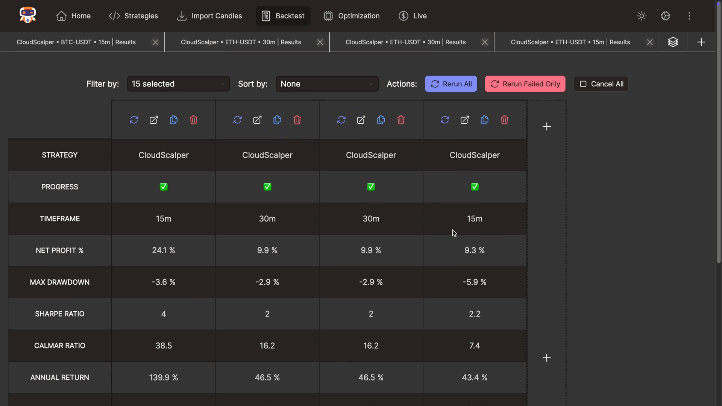
Accelerate research using the benchmark feature. Run batch backtests, compare across timeframes, symbols, and strategies. Filter and sort results by key performance metrics for efficient analysis.
AI
Leverage our AI assistant even with limited Python knowledge. Get help writing and improving strategies, implementing ideas, debugging, optimizing, and understanding code. Your personal AI quant.
Optimize Your Strategies
Unsure about optimal parameters? Let the optimization mode decide using simple syntax. Fine-tune any strategy parameter with the Optuna library and easy cross-validation.
@property
def slow_sma(self):
return ta.sma(self.candles, self.hp['slow_sma_period'])
@property
def fast_sma(self):
return ta.sma(self.candles, self.hp['fast_sma_period'])
def hyperparameters(self):
return [
{'name': 'slow_sma_period', 'type': int, 'min': 150, 'max': 210, 'default': 200},
{'name': 'fast_sma_period', 'type': int, 'min': 20, 'max': 100, 'default': 50},
]
Getting Started
Head over to the "getting started" section of the documentation. The
documentation is short yet very informative.
Resources
What's next?
You can see the project's roadmap here. Subscribe to our mailing list at jesse.trade to get the good stuff as soon they're released. Don't worry, We won't send you spam—Pinky promise.
Disclaimer
This software is for educational purposes only. USE THE SOFTWARE AT YOUR OWN RISK. THE AUTHORS AND ALL AFFILIATES ASSUME NO RESPONSIBILITY FOR YOUR TRADING RESULTS. Do not risk money that you are afraid to lose. There might be bugs in the code - this software DOES NOT come with ANY warranty.












