
Security News
npm Adopts OIDC for Trusted Publishing in CI/CD Workflows
npm now supports Trusted Publishing with OIDC, enabling secure package publishing directly from CI/CD workflows without relying on long-lived tokens.
MapReader is a open-source python library for exploring and analyzing map images at scale.
It contains two different pipelines:
MapReader was developed in the Living with Machines project to analyze large collections of historical maps but is a generalizable computer vision tool which can be applied to any images in a wide variety of domains.
The MapReader classification pipeline enables users to train a classification model to recognize visual features within map images and to identify patches containing these features across entire map collections:
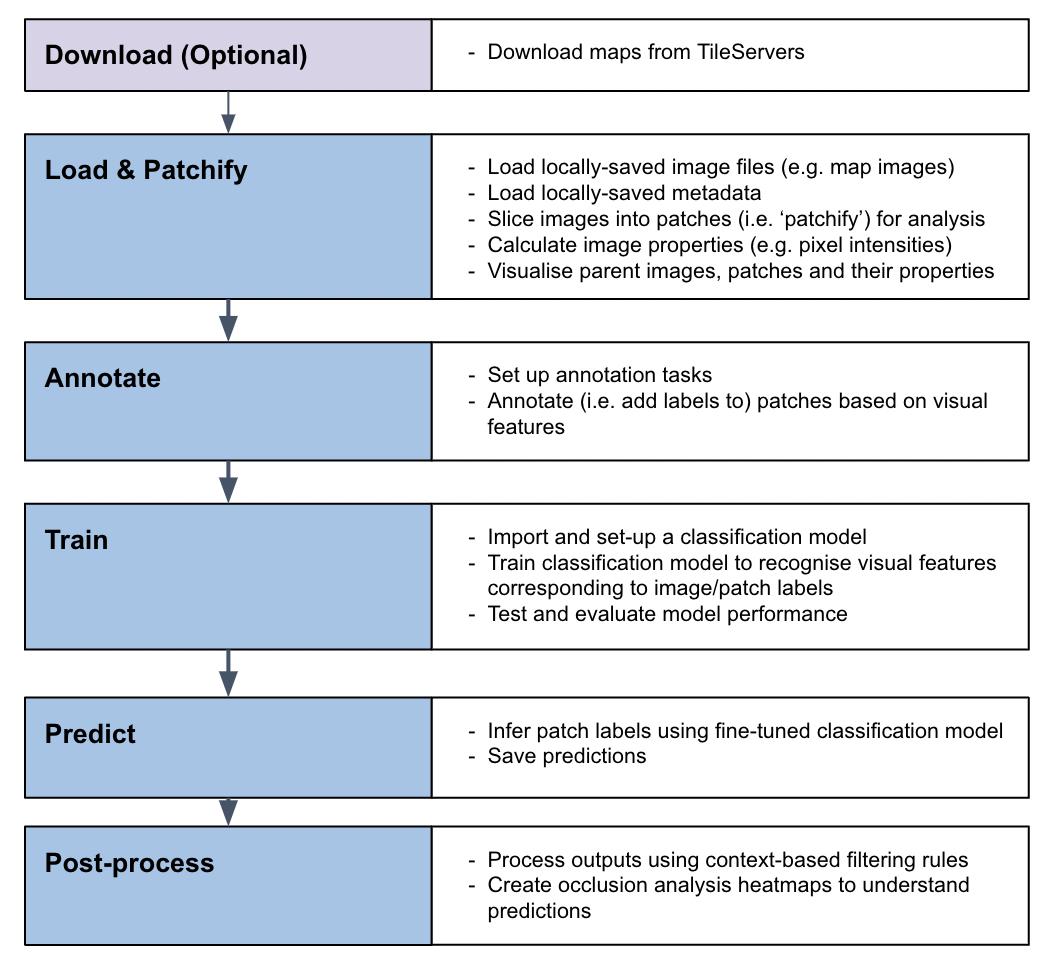
The MapReader text spotting pipeline enables users to detect and recognize text in map images using a pre-trained text spotting model:

The MapReader documentation can be found at https://mapreader.readthedocs.io/en/latest/.
New users should refer to the Installation instructions and Input guidance for help with the initial set up of MapReader.
All users should refer to our User Guide for guidance on how to use MapReader. This contains end-to-end instructions on how to use the MapReader pipeline.
Developers and contributors may also want to refer to the API documentation and Contribution guide for guidance on how to contribute to the MapReader package.
All users are encouraged to join our community! Please refer to the Community and contributions page for information on ways to get involved.
Join our Slack workspace! Please fill out this form to receive an invitation to the Slack workspace.
This repository contains everything needed for running MapReader.
The repository is structured as follows:
mapreader/: Contains the source code for the MapReader library.docs/: Contains the documentation for the MapReader library.tests/ and test_text_spotting/: Contains the tests for the MapReader library.Our worked examples can be found in the mapreader-examples repository.
We also have a number of other MapReader and map related repositories which can be found on the maps-as-data GitHub organisation page.
If you use MapReader in your work, please cite:
This work was supported by Living with Machines (AHRC grant AH/S01179X/1), Data/Culture (AHRC grant AH/Y00745X/1) and The Alan Turing Institute (EPSRC grant EP/N510129/1).
Living with Machines, funded by the UK Research and Innovation (UKRI) Strategic Priority Fund, is a multidisciplinary collaboration delivered by the Arts and Humanities Research Council (AHRC), with The Alan Turing Institute, the British Library and the Universities of Cambridge, East Anglia, Exeter, and Queen Mary University of London.
Maps above reproduced with the permission of the National Library of Scotland https://maps.nls.uk/index.html
Katie McDonough 🔬 🤔 📖 📆 👀 📢 ✅ | Daniel C.S. Wilson 🔬 🤔 📢 📖 | Kasra Hosseini 💻 🤔 🔬 👀 📢 | Rosie Wood 💻 📖 🤔 📢 ✅ 👀 🚧 🔬 | Kalle Westerling 💻 📖 🚧 👀 📢 | Chris Fleet 🔣 | Kaspar Beelen 🤔 👀 🔬 |
Andy Smith 💻 📖 🧑🏫 👀 | Adam Cox 💻 ⚠️ |
FAQs
A computer vision pipeline for the semantic exploration of maps/images at scale
We found that mapreader demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 2 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
npm now supports Trusted Publishing with OIDC, enabling secure package publishing directly from CI/CD workflows without relying on long-lived tokens.

Research
/Security News
A RubyGems malware campaign used 60 malicious packages posing as automation tools to steal credentials from social media and marketing tool users.

Security News
The CNA Scorecard ranks CVE issuers by data completeness, revealing major gaps in patch info and software identifiers across thousands of vulnerabilities.