
Security News
The Changelog Podcast: Practical Steps to Stay Safe on npm
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.


Sarah Gooding
July 19, 2025
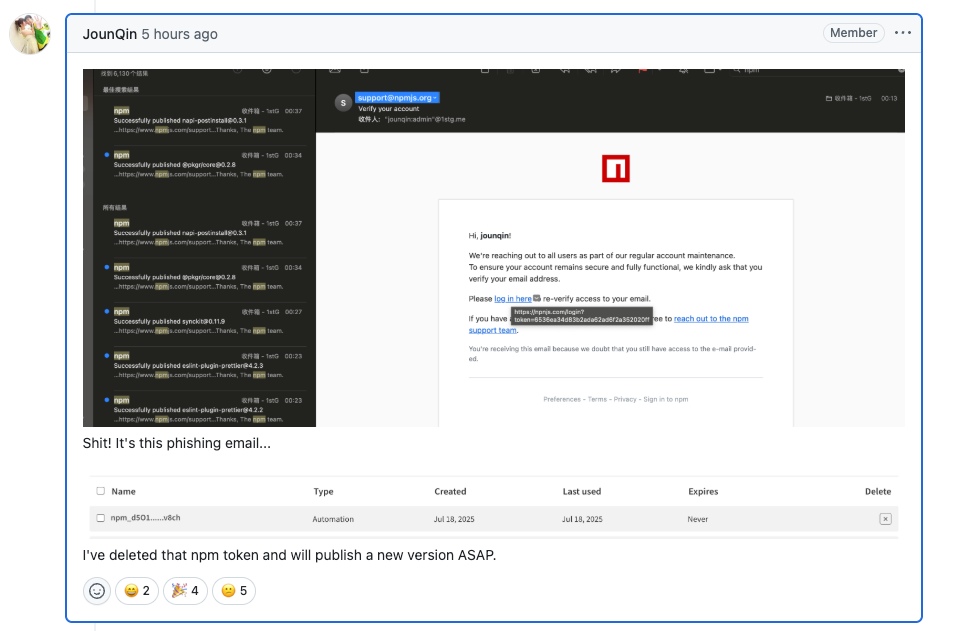
Hours after we reported on the npm phishing campaign using the typosquatted npnjs.com site, we’re now seeing the first major fallout: popular npm packages, including eslint-config-prettier and eslint-plugin-prettier, were compromised when a maintainer’s npm token was stolen via the phishing email.
A suspicious activity report in GitHub issue on the eslint-config-prettier repo revealed that four new versions of eslint-config-prettier were published with no corresponding commits or PRs on GitHub. Maintainers quickly discovered the new versions contained malicious code, including a Windows-specific payload attempting to load node-gyp.dll via rundll32.
Malicious releases included:
The injected code attempted to execute a DLL on Windows machines, potentially allowing remote code execution.
The maintainer confirmed their npm token was compromised via the npnjs.com phishing email. The attackers used the stolen credentials to publish malicious versions of multiple packages without touching the GitHub repos, making the attack harder to spot.
Registration emails and maintainer metadata are easily accessible in npm’s package info, which threat actors scrape to build target lists of package maintainers.
Prettier and ESLint integrations are widely used in thousands of projects. Tools like Dependabot and Renovate automatically pick up the “latest” versions of packages, meaning that CI/CD pipelines and developers could have unknowingly installed compromised versions.
The affected maintainer was quick to respond and took the following actions:
node_modules, clear npm caches, and reinstall from clean, updated versions.latest tags in CI pipelines.This is a textbook example of multi-stage supply chain compromise:
More reports of compromised credentials are likely to roll in as attackers target other maintainers, leveraging scraped npm metadata and what has so far proved to be a very convincing automated phishing campaign.
At Socket, we detect suspicious package activity, such as new versions with unexpected install scripts or binaries, to help developers catch these incidents before they spread. Install the free Socket GitHub App to enable real-time pull request scanning to catch malicious dependencies before they are merged.
This incident shows how quickly phishing attacks on maintainers can escalate into ecosystem-wide threats. We are continuing to monitor the npm ecosystem for signs of further malicious publishing activity and will share updates as this attack campaign unfolds.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.

Security News
Experts push back on new claims about AI-driven ransomware, warning that hype and sponsored research are distorting how the threat is understood.

Security News
Ruby's creator Matz assumes control of RubyGems and Bundler repositories while former maintainers agree to step back and transfer all rights to end the dispute.