
Product
Introducing Socket Firewall Enterprise: Flexible, Configurable Protection for Modern Package Ecosystems
Socket Firewall Enterprise is now available with flexible deployment, configurable policies, and expanded language support.

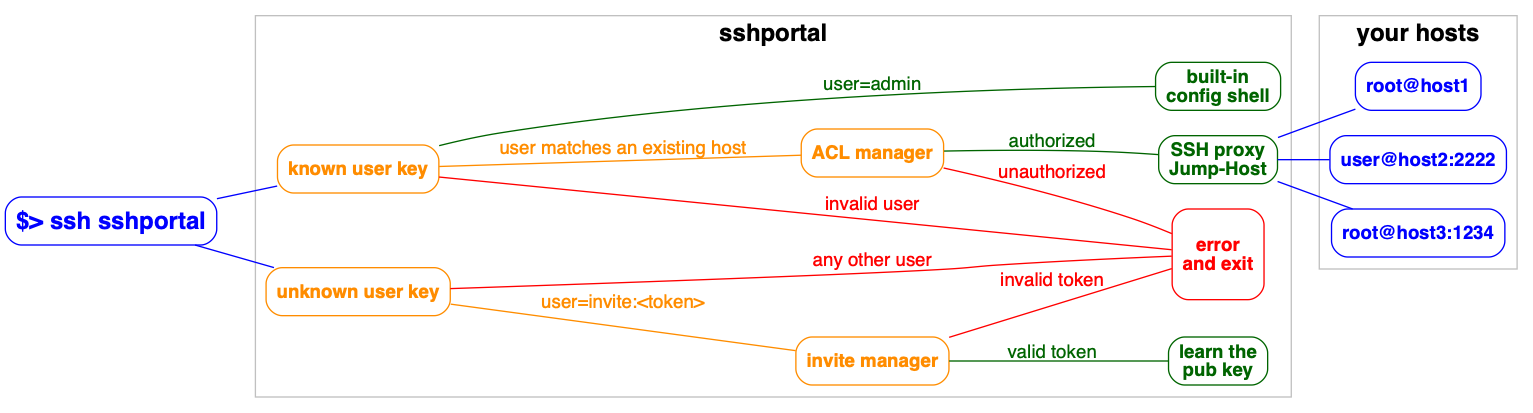
Jump host/Jump server without the jump, a.k.a Transparent SSH bastion
The original project is no longer being maintained. This fork includes important security fixes, some bugfixes and features but it is on MAINTENANCE mode and only security issues and major bugs will be fixed. You should consider using Teleport instead.
Packaged installation (.deb & .rpm) is privileged as it comes with a hardened systemd service and a SELinux module if you have enfored SELinux on your GNU/Linux distribution.
Get the latest version here
Note : by default, your package manager will automatically install sqlite (recommended dependency)
This installation will install sshportal as a systemd service, configure logrotate to keep 1 year of audit logs and add a systemd timer for session logs management. See packaging.
If mariadb is selected during the install, it will also automatically create the sshportal database if it doesn't exist.
apt install ./sshportal_x.x.x_xxx.deb
You will be asked if you want to use mariadb instead of sqlite (default). Make sure to install mariadb-server before as the package is not listed as a hard dependency in the control file.
To install SSHportal with mariadb:
apt install --no-install-recommends -y mariadb-server
DEBIAN_FRONTEND=noninteractive SSHPORTAL_MARIADB_SETUP=true apt install --no-install-recommends -y mariadb-server ./sshportal_x.x.x_xxx.deb
If you want to stick with sqlite, you just have to do this:
DEBIAN_FRONTEND=noninteractive apt install -y ./sshportal_x.x.x_xxx.deb
Make sure to install mariadb-server before if you want to use it as this package is not listed as a hard dependency in the control file.
There is no debconf in RedHat distribution so if you want an automatic mariadb setup you need to install sshportal with :
dnf install -y --setopt=install_weak_deps=False mariadb-server
SSHPORTAL_MARIADB_SETUP=true dnf install --setopt=install_weak_deps=False ./sshportal_x.x.x_xxx.rpm
If you want to stick with sqlite, you just have to do this:
dnf install -y ./sshportal_x.x.x_xxx.rpm
An automated build is setup on the Github registry.
# Start a server in background
# mount `pwd` to persist the sqlite database file
docker run -p 2222:2222 -d --name=sshportal -v "$(pwd):$(pwd)" -w "$(pwd)" ghcr.io/alterway/sshportal:latest
# check logs (mandatory on first run to get the administrator invite token)
docker logs -f sshportal
/var/log/sshportal/audit/audit.log if installed from a package manager :2023/09/01 15:03:18 info: system migrated
2023/09/01 15:03:18 info: 'sshportal' user created. Run 'ssh localhost -p 2222 -l invite:6tUguNFYxeOxdx0N' to associate your public key with this account
2023/09/01 15:03:18 info: SSH Server accepting connections on :2222, idle-timout=0s
ssh localhost -p 2222 -l invite:xxxxxxx
Welcome sshportal!
Your key is now associated with the user "sshportal@localhost".
ssh sshportal@localhost -p 2222
config> host create bart@foo.example.org
1
config>
config> host ls
ID | NAME | URL | KEY | PASS | GROUPS | COMMENT
+----+------+-------------------------+---------+------+---------+---------+
1 | foo | bart@foo.example.org:22 | default | | default |
Total: 1 hosts.
config>
host key to the serverconfig> host ls
ID | NAME | URL | KEY | GROUPS | UPDATED | CREATED | COMMENT | HOP | LOGGING
-----+------+-----+-----+--------+---------+---------+---------+-----+----------
Total: 0 hosts.
config> key ls
ID | NAME | TYPE | LENGTH | HOSTS | UPDATED | CREATED | COMMENT
-----+---------+---------+--------+-------+--------------+--------------+-----------------------
2 | host | ed25519 | 1 | 0 | 1 minute ago | 1 minute ago | created by sshportal
1 | default | ed25519 | 1 | 0 | 1 minute ago | 1 minute ago | created by sshportal
ssh bart@foo.example.org "$(ssh sshportal@localhost -p 2222 key setup host)"
ssh localhost -p 2222 -l foo
bart@foo>
This command doesn't create a user on the remote server, it only creates an account in the sshportal database.
config> user invite bob@example.com
User 2 created.
To associate this account with a key, use the following SSH user: 'invite:NfHK5a84jjJkwzDk'.
Demo gif:

authorized_keys)ttyplay for replay)scp supportrsync supporttunneling (local forward, remote forward, dynamic forward) supportsftp supportssh-agent supportX11 forwarding support.ssh/config, works with every tested SSH programming libraries and every tested SSH clients(Known) limitations
moshhealthcheck as this is a built-in command.sshportal embeds built-in backup/restore methods which basically import/export JSON objects:
# Backup
ssh portal config backup > sshportal.bkp
# Restore
ssh portal config restore < sshportal.bkp
This method is particularly useful as it should be resistant against future DB schema changes (expected during development phase).
I suggest you to be careful during this development phase, and use an additional backup method, for example:
# sqlite dump
sqlite3 sshportal.db .dump > sshportal.sql.bkp
# or just the immortal cp
cp sshportal.db sshportal.db.bkp
sshportal embeds a configuration CLI.
By default, the configuration user is the user starting the server for the first time. It fallbacks to root.
Each command can be run directly by using this syntax: ssh root@portal.example.org <command> [args]:
ssh root@portal.example.org host inspect toto
You can enter in interactive mode using this syntax: ssh root@portal.example.org

See Documentation for the list of shell commands.
By default, sshportal will return OK to anyone sshing using the healthcheck user without checking for authentication.
$ ssh healthcheck@localhost -p 2222
OK
the healtcheck user can be changed using the healthcheck-user option.
Alternatively, you can run the built-in healthcheck helper (requiring no ssh client nor ssh key):
Usage: sshportal healthcheck [--addr=host:port] [--wait] [--quiet]
$ sshportal healthcheck --addr=localhost:2222; echo $?
0
Wait for sshportal to be healthy, then connect
$ sshportal healthcheck --wait && ssh sshportal -l root
config>
Edit your ~/.ssh/config file (create it first if needed)
Host portal
User root # or 'sshportal' if you use the packaged binary
User root # or 'sshportal' if you use the packaged sshportal
Port 2222 # portal port
HostName 127.0.0.1 # portal hostname
# you can now run a shell using this:
ssh portal
# instead of this:
ssh localhost -p 2222 -l root
# or connect to hosts using this:
ssh hostname@portal
# instead of this:
ssh localhost -p 2222 -l hostname
sshportal is stateless but relies on a database to store configuration and logs.
By default, sshportal uses a local sqlite database which isn't scalable by design.
You can run multiple instances of sshportal sharing the same MySQL database, using sshportal --db-conn=user:pass@host/dbname?parseTime=true --db-driver=mysql.

See examples/mysql.

Install golangci-lint and run this in project root:
golangci-lint run
Perform integration tests
cd ./examples/integration && make
Perform unit tests
go test
FAQs
Unknown package
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Socket Firewall Enterprise is now available with flexible deployment, configurable policies, and expanded language support.

Security News
Open source dashboard CNAPulse tracks CVE Numbering Authorities’ publishing activity, highlighting trends and transparency across the CVE ecosystem.

Product
Detect malware, unsafe data flows, and license issues in GitHub Actions with Socket’s new workflow scanning support.