
Research
Security News
Malicious npm Package Typosquats react-login-page to Deploy Keylogger
Socket researchers unpack a typosquatting package with malicious code that logs keystrokes and exfiltrates sensitive data to a remote server.
@aws-cdk/aws-ecr-assets
Advanced tools
Package description
@aws-cdk/aws-ecr-assets is an AWS CDK library that allows you to build and publish Docker images to Amazon Elastic Container Registry (ECR) as part of your AWS Cloud Development Kit (CDK) applications. This package simplifies the process of managing Docker images within your CDK stacks.
Building Docker Images
This feature allows you to build Docker images from a specified directory and include them in your CDK stack. The Docker image is built and uploaded to an ECR repository automatically.
const ecrAssets = require('@aws-cdk/aws-ecr-assets');
const cdk = require('@aws-cdk/core');
class MyStack extends cdk.Stack {
constructor(scope, id, props) {
super(scope, id, props);
new ecrAssets.DockerImageAsset(this, 'MyDockerImage', {
directory: path.join(__dirname, 'my-docker-image')
});
}
}
const app = new cdk.App();
new MyStack(app, 'MyStack');Using Docker Images in ECS
This feature demonstrates how to use a Docker image built with @aws-cdk/aws-ecr-assets in an Amazon ECS task definition. The Docker image is referenced directly from the ECR repository.
const ecs = require('@aws-cdk/aws-ecs');
const ecrAssets = require('@aws-cdk/aws-ecr-assets');
const cdk = require('@aws-cdk/core');
class MyStack extends cdk.Stack {
constructor(scope, id, props) {
super(scope, id, props);
const asset = new ecrAssets.DockerImageAsset(this, 'MyDockerImage', {
directory: path.join(__dirname, 'my-docker-image')
});
new ecs.ContainerImage.fromDockerImageAsset(asset);
}
}
const app = new cdk.App();
new MyStack(app, 'MyStack');Dockerode is a Node.js module that provides a Docker Remote API client. It allows you to manage Docker containers, images, and other Docker resources programmatically. Unlike @aws-cdk/aws-ecr-assets, which is tightly integrated with AWS CDK and ECR, Dockerode is a more general-purpose Docker client.
Node Docker API is another Node.js client for the Docker Remote API. It provides a simple and flexible way to interact with Docker from Node.js applications. While it offers similar functionalities to Dockerode, it is not specifically designed for integration with AWS services like @aws-cdk/aws-ecr-assets.
The AWS SDK for JavaScript provides a comprehensive set of tools for interacting with AWS services, including ECR. While you can use the AWS SDK to manage ECR repositories and images, it does not provide the same level of abstraction and integration with CDK as @aws-cdk/aws-ecr-assets.
Changelog
1.77.0 (2020-12-07)
VpcLink.fromVpcLinkId() API has been
replaced with VpcLink.fromVpcLinkAttributes().@aws-cdk/secretsmanager:parseOwnedSecretName flag.minify or sourceMap are now gathered under a new bundling prop.bundlingEnvironment is now bundling.environmentbundlingDockerImage is now bundling.dockerImageexecuteBatchBuild on CodeBuildAction (#11741) (3dcd1a8), closes #11662any but only works if a map is passed (#11768) (f85c08c), closes #11483Readme
The APIs of higher level constructs in this module are experimental and under active development. They are subject to non-backward compatible changes or removal in any future version. These are not subject to the Semantic Versioning model and breaking changes will be announced in the release notes. This means that while you may use them, you may need to update your source code when upgrading to a newer version of this package.
This module allows bundling Docker images as assets.
Images are built from a local Docker context directory (with a Dockerfile),
uploaded to ECR by the CDK toolkit and/or your app's CI-CD pipeline, and can be
naturally referenced in your CDK app.
import { DockerImageAsset } from '@aws-cdk/aws-ecr-assets';
const asset = new DockerImageAsset(this, 'MyBuildImage', {
directory: path.join(__dirname, 'my-image')
});
The directory my-image must include a Dockerfile.
This will instruct the toolkit to build a Docker image from my-image, push it
to an AWS ECR repository and wire the name of the repository as CloudFormation
parameters to your stack.
By default, all files in the given directory will be copied into the docker
build context. If there is a large directory that you know you definitely
don't need in the build context you can improve the performance by adding the
names of files and directories to ignore to a file called .dockerignore, or
pass them via the exclude property. If both are available, the patterns
found in exclude are appended to the patterns found in .dockerignore.
The ignoreMode property controls how the set of ignore patterns is
interpreted. The recommended setting for Docker image assets is
IgnoreMode.DOCKER. If the context flag
@aws-cdk/aws-ecr-assets:dockerIgnoreSupport is set to true in your
cdk.json (this is by default for new projects, but must be set manually for
old projects) then IgnoreMode.DOCKER is the default and you don't need to
configure it on the asset itself.
Use asset.imageUri to reference the image (it includes both the ECR image URL
and tag.
You can optionally pass build args to the docker build command by specifying
the buildArgs property:
const asset = new DockerImageAsset(this, 'MyBuildImage', {
directory: path.join(__dirname, 'my-image'),
buildArgs: {
HTTP_PROXY: 'http://10.20.30.2:1234'
}
});
You can optionally pass a target to the docker build command by specifying
the target property:
const asset = new DockerImageAsset(this, 'MyBuildImage', {
directory: path.join(__dirname, 'my-image'),
target: 'a-target'
})
Depending on the consumer of your image asset, you will need to make sure the principal has permissions to pull the image.
In most cases, you should use the asset.repository.grantPull(principal)
method. This will modify the IAM policy of the principal to allow it to
pull images from this repository.
If the pulling principal is not in the same account or is an AWS service that
doesn't assume a role in your account (e.g. AWS CodeBuild), pull permissions
must be granted on the resource policy (and not on the principal's policy).
To do that, you can use asset.repository.addToResourcePolicy(statement) to
grant the desired principal the following permissions: "ecr:GetDownloadUrlForLayer",
"ecr:BatchGetImage" and "ecr:BatchCheckLayerAvailability".
FAQs
Unknown package
We found that @aws-cdk/aws-ecr-assets demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 4 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Security News
Socket researchers unpack a typosquatting package with malicious code that logs keystrokes and exfiltrates sensitive data to a remote server.
Security News
The JavaScript community has launched the e18e initiative to improve ecosystem performance by cleaning up dependency trees, speeding up critical parts of the ecosystem, and documenting lighter alternatives to established tools.
Product
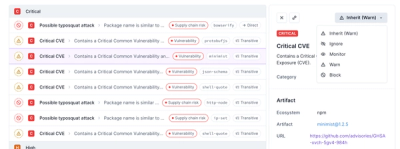
Socket now supports four distinct alert actions instead of the previous two, and alert triaging allows users to override the actions taken for all individual alerts.