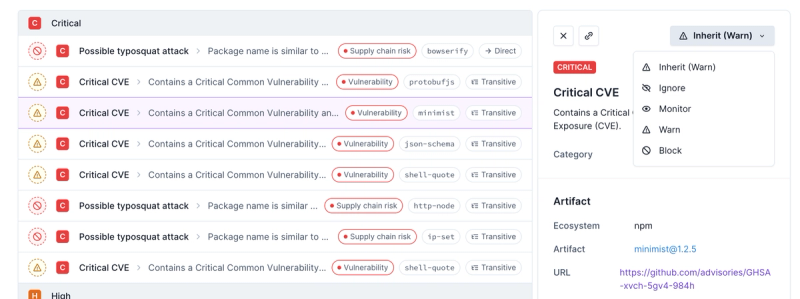
Product
Introducing Enhanced Alert Actions and Triage Functionality
Socket now supports four distinct alert actions instead of the previous two, and alert triaging allows users to override the actions taken for all individual alerts.
@aws-cdk/aws-secretsmanager
Advanced tools
Changelog
1.67.0 (2020-10-07)
monocdk. Note that monocdk is still experimental.. in the name (#10441) (063798b), closes #10109addExecuteFileCommand arguments cannot be omitted (#10692) (7178374), closes #10687InitCommand.shellCommand() renders an argv command instead (#10691) (de9d2f7), closes #10684Readme
import * as secretsmanager from '@aws-cdk/aws-secretsmanager';
In order to have SecretsManager generate a new secret value automatically, you can get started with the following:
The Secret construct does not allow specifying the SecretString property
of the AWS::SecretsManager::Secret resource (as this will almost always
lead to the secret being surfaced in plain text and possibly committed to
your source control).
If you need to use a pre-existing secret, the recommended way is to manually
provision the secret in AWS SecretsManager and use the Secret.fromSecretArn
or Secret.fromSecretAttributes method to make it available in your CDK Application:
const secret = secretsmanager.Secret.fromSecretAttributes(scope, 'ImportedSecret', {
secretArn: 'arn:aws:secretsmanager:<region>:<account-id-number>:secret:<secret-name>-<random-6-characters>',
// If the secret is encrypted using a KMS-hosted CMK, either import or reference that key:
encryptionKey,
});
SecretsManager secret values can only be used in select set of properties. For the list of properties, see the CloudFormation Dynamic References documentation.
A secret can set RemovalPolicy. If it set to RETAIN, that removing a secret will fail.
You must grant permission to a resource for that resource to be allowed to
use a secret. This can be achieved with the Secret.grantRead and/or Secret.grantUpdate
method, depending on your need:
const role = new iam.Role(stack, 'SomeRole', { assumedBy: new iam.AccountRootPrincipal() });
const secret = new secretsmanager.Secret(stack, 'Secret');
secret.grantRead(role);
secret.grantWrite(role);
If, as in the following example, your secret was created with a KMS key:
const key = new kms.Key(stack, 'KMS');
const secret = new secretsmanager.Secret(stack, 'Secret', { encryptionKey: key });
secret.grantRead(role);
secret.grantWrite(role);
then Secret.grantRead and Secret.grantWrite will also grant the role the
relevant encrypt and decrypt permissions to the KMS key through the
SecretsManager service principal.
A rotation schedule can be added to a Secret using a custom Lambda function:
const fn = new lambda.Function(...);
const secret = new secretsmanager.Secret(this, 'Secret');
secret.addRotationSchedule('RotationSchedule', {
rotationLambda: fn,
automaticallyAfter: Duration.days(15)
});
See Overview of the Lambda Rotation Function on how to implement a Lambda Rotation Function.
Define a SecretRotation to rotate database credentials:
new secretsmanager.SecretRotation(this, 'SecretRotation', {
application: secretsmanager.SecretRotationApplication.MYSQL_ROTATION_SINGLE_USER, // MySQL single user scheme
secret: mySecret,
target: myDatabase, // a Connectable
vpc: myVpc, // The VPC where the secret rotation application will be deployed
excludeCharacters: ' %+:;{}', // characters to never use when generating new passwords;
// by default, no characters are excluded,
// which might cause problems with some services, like DMS
});
The secret must be a JSON string with the following format:
{
"engine": "<required: database engine>",
"host": "<required: instance host name>",
"username": "<required: username>",
"password": "<required: password>",
"dbname": "<optional: database name>",
"port": "<optional: if not specified, default port will be used>",
"masterarn": "<required for multi user rotation: the arn of the master secret which will be used to create users/change passwords>"
}
For the multi user scheme, a masterSecret must be specified:
new secretsmanager.SecretRotation(stack, 'SecretRotation', {
application: secretsmanager.SecretRotationApplication.MYSQL_ROTATION_MULTI_USER,
secret: myUserSecret, // The secret that will be rotated
masterSecret: myMasterSecret, // The secret used for the rotation
target: myDatabase,
vpc: myVpc,
});
See also aws-rds where credentials generation and rotation is integrated.
Existing secrets can be imported by ARN, name, and other attributes (including the KMS key used to encrypt the secret). Secrets imported by name can used the short-form of the name (without the SecretsManager-provided suffx); the secret name must exist in the same account and region as the stack. Importing by name makes it easier to reference secrets created in different regions, each with their own suffix and ARN.
import * as kms from '@aws-cdk/aws-kms';
const secretArn = 'arn:aws:secretsmanager:eu-west-1:111111111111:secret:MySecret-f3gDy9';
const encryptionKey = kms.Key.fromKeyArn(stack, 'MyEncKey', 'arn:aws:kms:eu-west-1:111111111111:key/21c4b39b-fde2-4273-9ac0-d9bb5c0d0030');
const mySecretFromArn = secretsmanager.Secret.fromSecretArn(stack, 'SecretFromArn', secretArn);
const mySecretFromName = secretsmanager.Secret.fromSecretName(stack, 'SecretFromName', 'MySecret') // Note: the -f3gDy9 suffix is optional
const mySecretFromAttrs = secretsmanager.Secret.fromSecretAttributes(stack, 'SecretFromAttributes', {
secretArn,
encryptionKey,
secretName: 'MySecret', // Optional, will be calculated from the ARN
});
FAQs
The CDK Construct Library for AWS::SecretsManager
We found that @aws-cdk/aws-secretsmanager demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 4 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Socket now supports four distinct alert actions instead of the previous two, and alert triaging allows users to override the actions taken for all individual alerts.
Security News
Polyfill.io has been serving malware for months via its CDN, after the project's open source maintainer sold the service to a company based in China.

Security News
OpenSSF is warning open source maintainers to stay vigilant against reputation farming on GitHub, where users artificially inflate their status by manipulating interactions on closed issues and PRs.