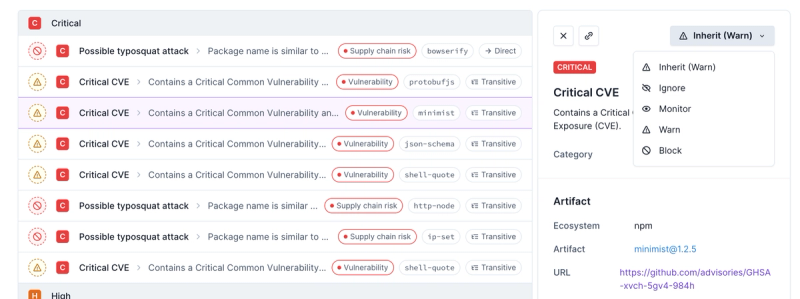
Product
Introducing Enhanced Alert Actions and Triage Functionality
Socket now supports four distinct alert actions instead of the previous two, and alert triaging allows users to override the actions taken for all individual alerts.
@aws-cdk/region-info
Advanced tools
Changelog
0.32.0 (2019-05-24)
@aws-cdk/aws-route53-targets package.IBucket.arnForObject method no longer
concatenates path fragments on your behalf. Pass the /-concatenated
key pattern instead.export methods from all AWS resources have been removed. CloudFormation Exports are now automatically created when attributes are referenced across stacks within the same app. To export resources manually, you can explicitly define a CfnOutput.kms.EncryptionKey renamed to kms.Keyec2.VpcNetwork renamed to ec2.Vpcec2.VpcSubnet renamed to ec2.Subnetcloudtrail.CloudTrail renamed to cloudtrail.Trail`XxxAttribute and XxxImportProps interfaces which were no longer in used after their corresponding export method was deleted and there was no use for them in imports.ecs.ClusterAttributes now accepts IVpc and ISecurityGroup instead of attributes. You can use their
corresponding fromXxx methods to import them as needed.servicediscovery.CnameInstance.instanceCname renamed to cname.glue.IDatabase.locationUrl is now only in glue.Database (not on the interface)ec2.TcpPortFromAttribute and UdpPortFromAttribute removed. Use TcpPort and UdpPort with new Token(x).toNumber instead.ec2.VpcNetwork.importFromContext renamed to ec2.Vpc.fromLookupiam.IRole.roleId has been removed from the interface, but Role.roleId is still available for owned resources.loadBalancer property in ServerDeploymentGroupProps has been changed.apigateway.ResourceBase.trackChild is now internal.cloudfront.S3OriginConfig.originAccessIdentity is now originAccessIdentityIdcodedeploy.LambdaDeploymentGroup.alarms is now cloudwatch.IAlarm[] (previously cloudwatch.Alarm[])codepipeline.crossRegionScaffoldingStacks renamed to crossRegionScaffoldingcodepipeline.CrossRegionScaffoldingStack renamed to codepipeline.CrossRegionScaffolding and cannot be instantiated (abstract)ec2.VpcSubnet.addDefaultRouteToNAT renamed to addDefaultNatRoute and made publicec2.VpcSubnet.addDefaultRouteToIGW renamed to addDefaultInternetRoute, made public and first argument is the gateway ID (string) and not the CFN L1 classecs.Ec2EventRuleTarget.taskDefinition is now ITaskDefinition (previously TaskDefinition)lambda.IEventSource.bind now accepts IFunction instead of FunctionBase. Use IFunction.addEventSourceMapping to add an event source mapping under the function.lambda.Layer.grantUsage renamed to lambda.layer.addPermission and returns voidstepfunctions.StateMachine.role is now iam.IRole (previously iam.Role)onXxx() CloudWatch Event methods now have the signature:
resource.onEvent('SomeId', {
target: new SomeTarget(...),
// options
});
onAlarm was renamed to addAlarmActiononOk was renamed to addOkActiononInsufficientData was renamed to addInsufficientDataActiononLifecycleTransition was renamed to addLifecycleHookonPreHook was renamed to addPreHookonPostHook was renamed to addPostHookonXxx were renamed to addXxxTriggeronImagePushed was renamed to onCloudTrailImagePushedonEvent was renamed to addEventNotificationonObjectCreated was renamed to addObjectCreatedNotificationonObjectRemoved was renamed to addObjectRemovedNotificationonPutObject was renamed to onCloudTrailPutObjectReadme
Some information used in CDK Applications differs from one AWS region to another, such as service principals used in IAM policies, S3 static website endpoints, ...
RegionInfo classThe library offers a simple interface to obtain region specific information in
the form of the RegionInfo class. This is the preferred way to interact with
the regional information database:
import { RegionInfo } from '@aws-cdk/region-info';
// Get the information for "eu-west-1":
const region = RegionInfo.get('eu-west-1');
// Access attributes:
region.s3StaticWebsiteEndpoint; // s3-website.eu-west-1.amazonaws.com
region.servicePrincipal('logs.amazonaws.com'); // logs.eu-west-1.amazonaws.com
The RegionInfo layer is built on top of the Low-Level API, which is described
below and can be used to register additional data, including user-defined facts
that are not available through the RegionInfo interface.
This library offers a primitive database of such information so that CDK
constructs can easily access regional information. The FactName class provides
a list of known fact names, which can then be used with the RegionInfo to
retrieve a particular value:
import regionInfo = require('@aws-cdk/region-info');
const codeDeployPrincipal = regionInfo.Fact.find('us-east-1', regionInfo.FactName.servicePrincipal('codedeploy.amazonaws.com'));
// => codedeploy.us-east-1.amazonaws.com
const staticWebsite = regionInfo.Fact.find('ap-northeast-1', regionInfo.FactName.s3StaticWebsiteEndpoint);
// => s3-website-ap-northeast-1.amazonaws.com
As new regions are released, it might happen that a particular fact you need is
missing from the library. In such cases, the Fact.register method can be used
to inject FactName into the database:
regionInfo.Fact.register({
region: 'bermuda-triangle-1',
name: regionInfo.FactName.servicePrincipal('s3.amazonaws.com'),
value: 's3-website.bermuda-triangle-1.nowhere.com',
});
In the event information provided by the library is incorrect, it can be
overridden using the same Fact.register method demonstrated above, simply
adding an extra boolean argument:
regionInfo.Fact.register({
region: 'us-east-1',
name: regionInfo.FactName.servicePrincipal('service.amazonaws.com'),
value: 'the-correct-principal.amazonaws.com',
}, true /* Allow overriding information */);
If you happen to have stumbled upon incorrect data built into this library, it is always a good idea to report your findings in a GitHub issue, so we can fix it for everyone else!
This module is part of the AWS Cloud Development Kit project.
FAQs
AWS region information, such as service principal names
We found that @aws-cdk/region-info demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 0 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Socket now supports four distinct alert actions instead of the previous two, and alert triaging allows users to override the actions taken for all individual alerts.
Security News
Polyfill.io has been serving malware for months via its CDN, after the project's open source maintainer sold the service to a company based in China.

Security News
OpenSSF is warning open source maintainers to stay vigilant against reputation farming on GitHub, where users artificially inflate their status by manipulating interactions on closed issues and PRs.