
Research
Security News
Malicious npm Package Typosquats react-login-page to Deploy Keylogger
Socket researchers unpack a typosquatting package with malicious code that logs keystrokes and exfiltrates sensitive data to a remote server.
pem
Advanced tools
Package description
The 'pem' npm package is a tool for creating and managing PEM (Privacy Enhanced Mail) files, which are commonly used for SSL/TLS certificates and keys. It provides a variety of functionalities for generating, reading, and managing these files.
Generate SSL Certificates
This feature allows you to generate self-signed SSL certificates. The code sample demonstrates how to create a certificate that is valid for one day.
const pem = require('pem');
pem.createCertificate({ days: 1, selfSigned: true }, function (err, keys) {
if (err) {
throw err;
}
console.log(keys);
});Read Certificate Information
This feature allows you to read and extract information from an existing certificate. The code sample shows how to read certificate information from a specified file path.
const pem = require('pem');
pem.readCertificateInfo('path/to/certificate.pem', function (err, info) {
if (err) {
throw err;
}
console.log(info);
});Create Certificate Signing Request (CSR)
This feature allows you to create a Certificate Signing Request (CSR), which is used to request a certificate from a Certificate Authority (CA). The code sample demonstrates how to create a CSR with a specified common name.
const pem = require('pem');
pem.createCSR({ commonName: 'example.com' }, function (err, csr) {
if (err) {
throw err;
}
console.log(csr);
});Create Private Key
This feature allows you to generate a private key. The code sample shows how to create a private key using the 'pem' package.
const pem = require('pem');
pem.createPrivateKey(function (err, key) {
if (err) {
throw err;
}
console.log(key);
});The 'node-forge' package is a comprehensive library for implementing various cryptographic functionalities in Node.js. It includes features for working with SSL/TLS, X.509 certificates, and more. Compared to 'pem', 'node-forge' offers a broader range of cryptographic tools but may require more in-depth knowledge to use effectively.
The 'openssl-wrapper' package is a Node.js wrapper for the OpenSSL command-line tool. It allows you to perform various cryptographic operations using OpenSSL commands. While 'openssl-wrapper' provides a wide range of functionalities similar to 'pem', it relies on having OpenSSL installed on the system and may be less user-friendly for those unfamiliar with OpenSSL commands.
The 'pkijs' package is a JavaScript library for Public Key Infrastructure (PKI) and X.509 certificates. It provides tools for creating, parsing, and validating certificates. Compared to 'pem', 'pkijs' is more focused on PKI and X.509 standards and offers more advanced features for working with certificates.
Changelog
27 April 2017
#121#120#119#113#111#110#106#98ca0b353cfbf14e805fa3aReadme
Create private keys and certificates with node.js
Install with npm
npm install pem
Here are some examples for creating an SSL key/cert on the fly, and running an HTTPS server on port 443. 443 is the standard HTTPS port, but requires root permissions on most systems. To get around this, you could use a higher port number, like 4300, and use https://localhost:4300 to access your server.
var https = require('https'),
pem = require('pem');
pem.createCertificate({days:1, selfSigned:true}, function(err, keys){
https.createServer({key: keys.serviceKey, cert: keys.certificate}, function(req, res){
res.end('o hai!')
}).listen(443);
});
var https = require('https'),
pem = require('pem'),
express = require('express');
pem.createCertificate({days:1, selfSigned:true}, function(err, keys){
var app = express();
app.get('/', function(req, res){
res.send('o hai!');
});
https.createServer({key: keys.serviceKey, cert: keys.certificate}, app).listen(443);
});
Use createDhparam for creating dhparam keys
pem.createDhparam(keyBitsize, callback)
Where
{dhparam}Use createPrivateKey for creating private keys
pem.createPrivateKey(keyBitsize, [options,] callback)
Where
{key}Use createCSR for creating certificate signing requests
pem.createCSR(options, callback)
Where
{csr, clientKey}Possible options are the following
clientKeyclientKey is undefined, bit size to use for generating a new key (defaults to 2048)md5, sha1 or sha256, defaults to sha256)localhost)Array) of subjectAltNames in the subjectAltName field (optional)Use createCertificate for creating private keys
pem.createCertificate(options, callback)
Where
{certificate, csr, clientKey, serviceKey}Possible options include all the options for createCSR - in case csr parameter is not defined and a new
CSR needs to be generated.
In addition, possible options are the following
serviceKeyserviceCertificate is definedserviceKey is not defined, use clientKey for signing-extensions v3_req-extensions v3_reqUse getPublicKey for exporting a public key from a private key, CSR or certificate
pem.getPublicKey(certificate, callback)
Where
{publicKey}Use readCertificateInfo for reading subject data from a certificate or a CSR
pem.readCertificateInfo(certificate, callback)
Where
{serial, country, state, locality, organization, organizationUnit, commonName, emailAddress, validity{start, end}, san{dns, ip}?, issuer{country, state, locality, organization, organizationUnit}, signatureAlgorithm, publicKeyAlgorithm, publicKeySize }? san is only present if the CSR or certificate has SAN entries.
signatureAlgorithm, publicKeyAlgorithm and publicKeySize only available if supportet and can parsed form openssl output
Use getFingerprint to get the default SHA1 fingerprint for a certificate
pem.getFingerprint(certificate, [hash,] callback)
Where
md5, sha1 or sha256, defaults to sha1){fingerprint}Use getModulus to get the modulus for a certificate, a CSR or a private key. Modulus can be useful to check that a Private Key Matches a Certificate
pem.getModulus(certificate, [password,] callback)
Where
{modulus}Use getDhparamInfo to get the size and prime of DH parameters.
pem.getDhparamInfo(dhparam, callback)
Where
{size, prime}Use createPkcs12 to export a certificate, the private key and optionally any signing or intermediate CA certificates to a PKCS12 keystore.
pem.createPkcs12(clientKey, certificate, p12Password, [options], callback)
Where
cipher, (one of "aes128", "aes192", "aes256", "camellia128", "camellia192", "camellia256", "des", "des3" or "idea"), clientKeyPassword and certFiles (an array of additional certificates to include - e.g. CA certificates){pkcs12} (binary)Use readPkcs12 to read a certificate, private key and CA certificates from a PKCS12 keystore.
pem.readPkcs12(bufferOrPath, [options], callback)
Where
clientKeyPassword which will be used to encrypt the stored key and p12Password which will be used to open the keystore{key: String, cert: String, ca: Array}### Verify a certificate signing chain
Use verifySigningChain to assert that a given certificate has a valid signing chain.
pem.verifySigningChain(certificate, ca, callback)
Where
### Custom extensions config file
You can specify custom OpenSSL extensions using the config or extFile options for createCertificate (or using csrConfigFile with createCSR).
extFile and csrConfigFile should be paths to the extension files. While config will generate a temporary file from the supplied file contents.
If you specify config then the v3_req section of your config file will be used.
The following would be an example of a Certificate Authority extensions file:
[req]
req_extensions = v3_req
distinguished_name = req_distinguished_name
[req_distinguished_name]
commonName = Common Name
commonName_max = 64
[v3_req]
basicConstraints = critical,CA:TRUE
While the following would specify subjectAltNames in the resulting certificate:
[req]
req_extensions = v3_req
[ v3_req ]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = host1.example.com
DNS.2 = host2.example.com
DNS.3 = host3.example.com
Note that createCertificate and createCSR supports the altNames option which would be easier to use in most cases.
Warning: If you specify altNames the custom extensions file will not be passed to OpenSSL.
In some systems the openssl executable might not be available by the default name or it is not included in $PATH. In this case you can define the location of the executable yourself as a one time action after you have loaded the pem module:
var pem = require('pem');
pem.config({
pathOpenSSL: '/usr/local/bin/openssl'
});
...
// do something with the pem module
MIT
FAQs
Unknown package
The npm package pem receives a total of 195,682 weekly downloads. As such, pem popularity was classified as popular.
We found that pem demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 2 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Security News
Socket researchers unpack a typosquatting package with malicious code that logs keystrokes and exfiltrates sensitive data to a remote server.
Security News
The JavaScript community has launched the e18e initiative to improve ecosystem performance by cleaning up dependency trees, speeding up critical parts of the ecosystem, and documenting lighter alternatives to established tools.
Product
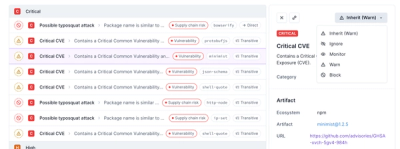
Socket now supports four distinct alert actions instead of the previous two, and alert triaging allows users to override the actions taken for all individual alerts.