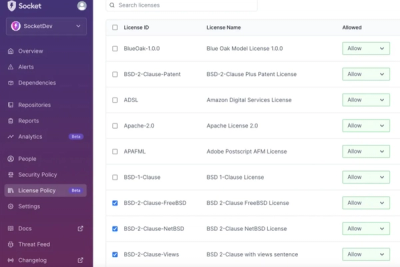
Product
Introducing License Enforcement in Socket
Ensure open-source compliance with Socket’s License Enforcement Beta. Set up your License Policy and secure your software!
ad2openldap is a lighweight Active Directory to Openldap replicator that helps replacing an IAM solution such as Centrify
ad2openldap is a lightweight replicator for user, group and netgroup information from Microsoft Active Directory into an OpenLDAP server to serve as Unix IDMAP solution. The original version was developed at Fred Hutch in 2010 to overcome frustrations with slow and unreliable Linux LDAP connectivity to Active Directory and to isolate badly behaving HPC scripts ("fork bombs") from critical AD infrastructure.
In 2017 we observed that newer solutions have grown in complexity (SSSD, Centrify) but have not been able to match ad2openldap in performance and reliability (SSSD). As we are migrating more services to cloud we continue to benefit from LDAP caches/replicas that provide low latency ldap services and ad2openldap continues to be a critical piece of infrastructure on more than 2000 servers/compute nodes on premise and in AWS and Google cloud. We decided to port the tool to Python3, add an easy installer via pip3 and test it on newer OS. We hope it will be as useful to others as it is to us.
Ubuntu ^^^^^^
On Ubuntu you will be prompted for an new LDAP Administrator password. please remember this password.
::
sudo apt install -y python3-pip slapd
sudo pip3 install ad2openldap
RHEL/CentOS 6 (untested in 2018) ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
::
sudo yum -y install epel-release
sudo yum -y install python34 python34-setuptools python34-devel gcc slapd
sudo easy_install-3.4 pip
sudo pip3 install ad2openldap
RHEL/CentOS 7 (untested in 2018) ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
::
sudo yum -y install python??
sudo pip3 install ad2openldap
/etc/ad2openldap/ad2openldap.conf requires these minimum settings:
::
# openldap adimistrator password (you set this during installation)
bind_dn_password: ChangeThisLocalAdminPassword12345
# AD service account (userPrincipalName aka UPN)
ad_account: ldap@example.com
# password for AD service account
ad_account_password: ChangeThisPassword
# AD LDAP URL of one of your domain controllers
ad_url: ldap://dc.example.com
# The base DN to use from Active Directory, under which objects are retrieved.
ad_base_dn: dc=example,dc=com
execute the setup script and enter items when prompted
::
ad2openlap3 setup
then create a cronjob in file /etc/cron.d/ad2openldap that runs ca. every 15 min
::
SHELL=/bin/bash
MAILTO=alertemail@institute.org
*/15 * * * * root /usr/local/bin/ad2openldap3 deltasync
--dont-blame-ad2openldap -v >>/var/log/ad2openldap/ad2openldap.log 2>&1 ;
/usr/local/bin/ad2openldap3 healthcheck -N username
It is strongly recommended to up the default open files limit for slapd to at least 8192
::
echo “ulimit -n 8192” >> /etc/default/slapd (or /etc/defaults/slapd depending on distribution)
Use the --verbose flag to log to STDOUT/STDERR.
The AD dumps and diffs are in /tmp by default:
::
ad_export.ldif - current dump
ad_export.ldif.0 - last dump
ad_export_delta.diff - computed differences between these files
Possible failure modes are:
LDAP server failure - needs restart, possibly followed by forced full update if corrupt or incomplete
Firewall block still improperly active - look at update script for removal syntax (this failure is very unlikely given the current process)
Bad or conflicting AD entities - a forced full update should remedy this
In the event that an incremental update is not possible or bypassed using the command line parameter '--fullsync', a full update will instead occur.
A full update:
FAQs
ad2openldap is a lighweight Active Directory to Openldap replicator that helps replacing an IAM solution such as Centrify
We found that ad2openldap demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Ensure open-source compliance with Socket’s License Enforcement Beta. Set up your License Policy and secure your software!
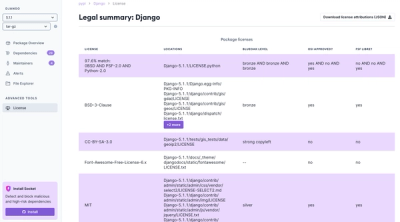
Product
We're launching a new set of license analysis and compliance features for analyzing, managing, and complying with licenses across a range of supported languages and ecosystems.
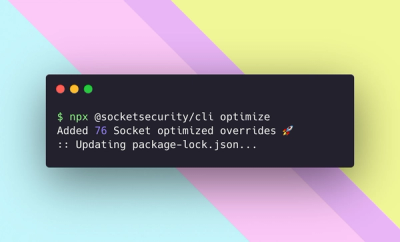
Product
We're excited to introduce Socket Optimize, a powerful CLI command to secure open source dependencies with tested, optimized package overrides.