
Security News
OWASP 2025 Top 10 Adds Software Supply Chain Failures, Ranked Top Community Concern
OWASP’s 2025 Top 10 introduces Software Supply Chain Failures as a new category, reflecting rising concern over dependency and build system risks.
wait-for-message
Advanced tools
A simple client server utility that blocks until a message is received on a TCP/IP socket connection
A simple client server utility that blocks until a message is received on a TCP/IP socket connection; useful for synchronizing interdependent networked jobs.
pip install wait-for-message
w4m Usageusage: w4m [-h] {send,wait} ...
A simple client server utility that blocks until a message is received on a TCP/IP socket connection
positional arguments:
{send,wait}
send send message to tcp/ip connection until acknowledged or maximum attempts
wait wait for message on tcp/ip connection until received or timeout
optional arguments:
-h, --help show this help message and exit
w4m sendsend message to tcp/ip connection until acknowledged or maximum attempts
usage: w4m send [-h] --ip-address IP_ADDRESS --port-number PORT_NUMBER --message MESSAGE_TO_SEND [--delay DELAY] [--attempts MAX_ATTEMPTS]
optional arguments:
-h, --help show this help message and exit
--ip-address IP_ADDRESS
the ip address of the server
--port-number PORT_NUMBER
the port number the server is listening on
--message MESSAGE_TO_SEND
the message to send
--delay DELAY number of seconds to delay between retries; default 10
--attempts MAX_ATTEMPTS
maximum retry attempts; default 6
w4m waitwait for message on tcp/ip connection until received or timeout - if message received and if it contains a body print it to stdout
usage: w4m wait [-h] [--ip-address IP_ADDRESS] --port-number PORT_NUMBER --message MESSAGE_TO_WAIT_FOR [--timeout TIMEOUT]
optional arguments:
-h, --help show this help message and exit
--ip-address IP_ADDRESS
the ip address to bind to; default 0.0.0.0
--port-number PORT_NUMBER
the port number to listen on
--message MESSAGE_TO_WAIT_FOR
the message to wait for
--timeout TIMEOUT number of seconds to wait for message; default 900 (i.e. 15 minutes)
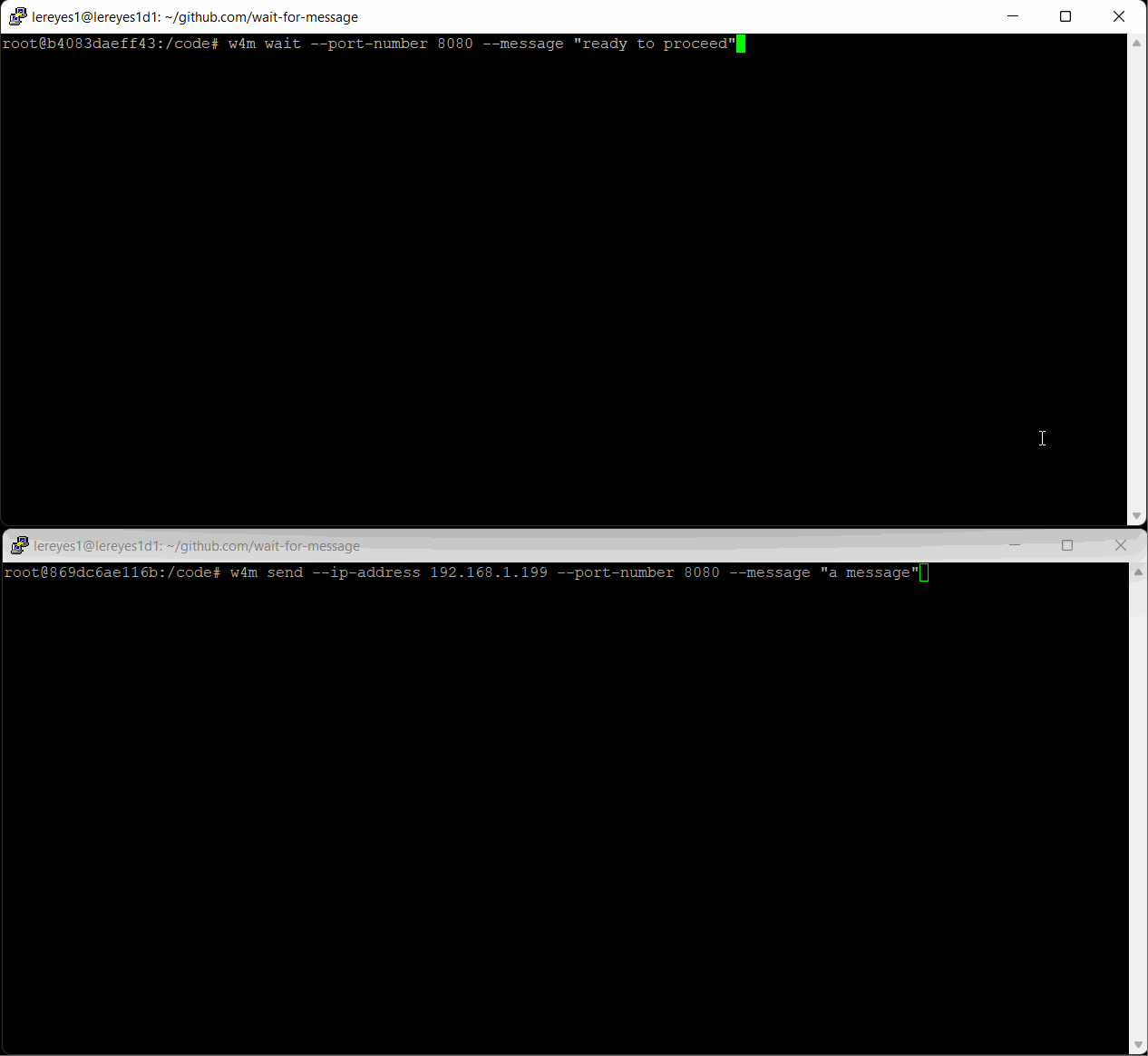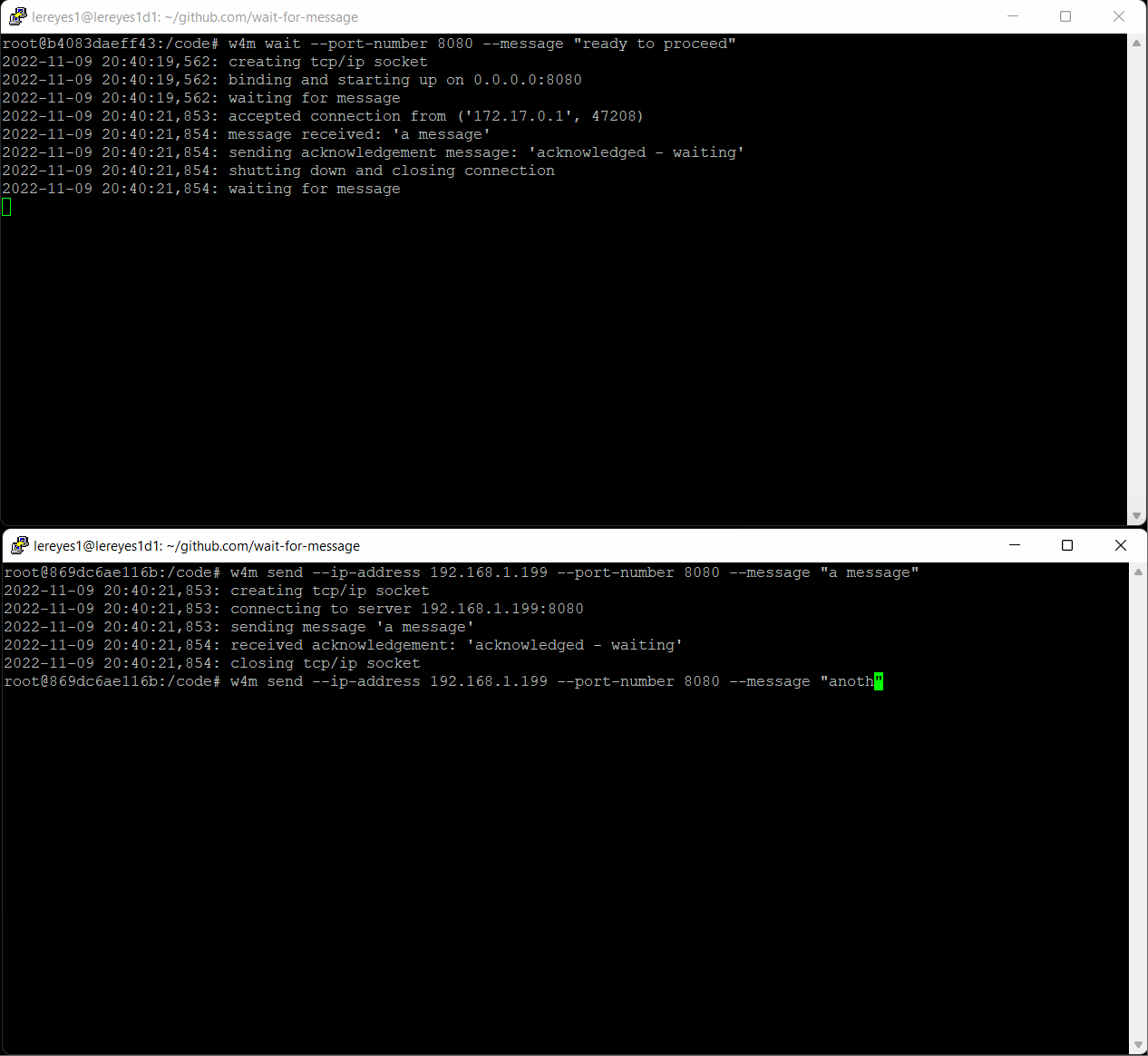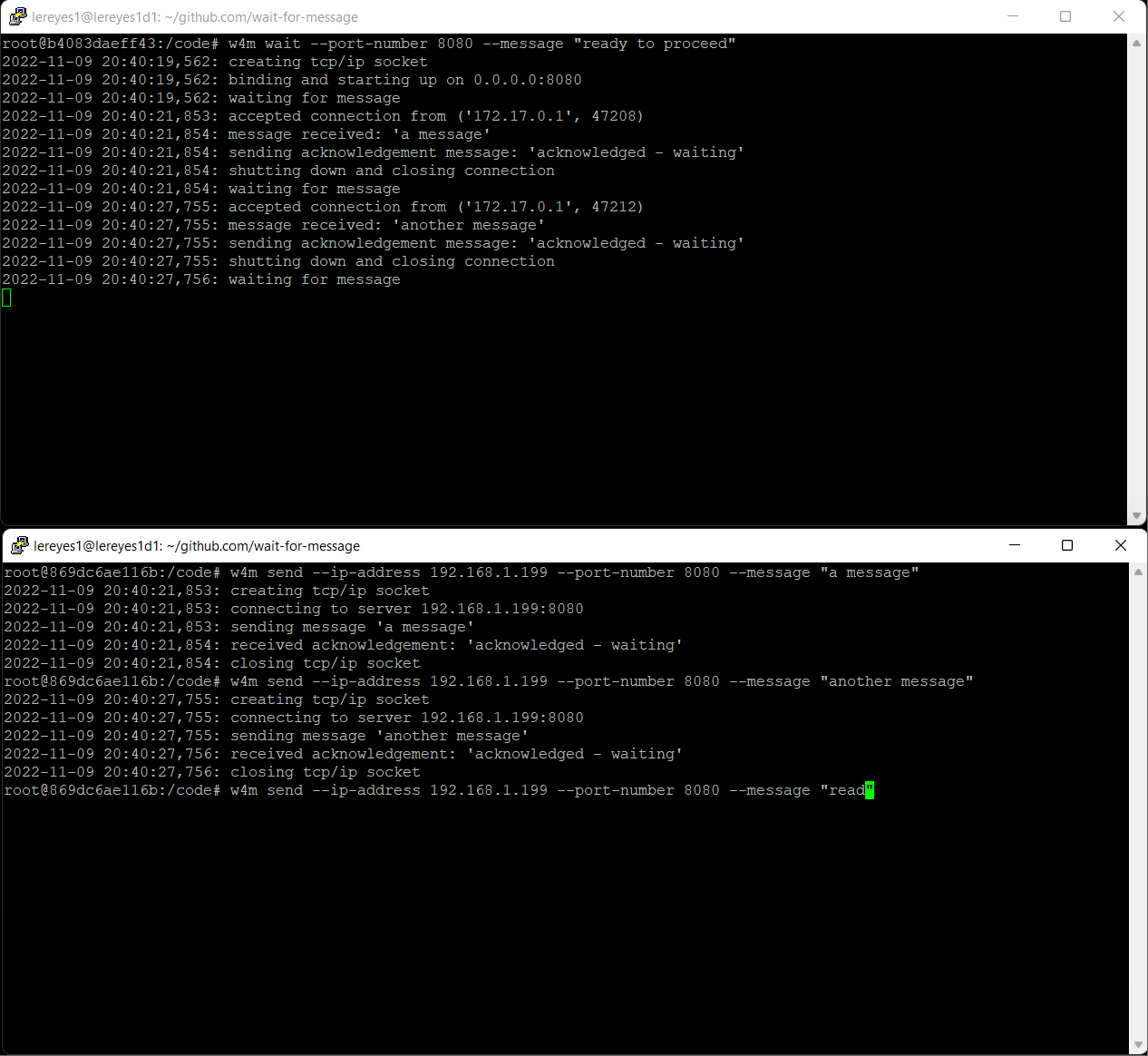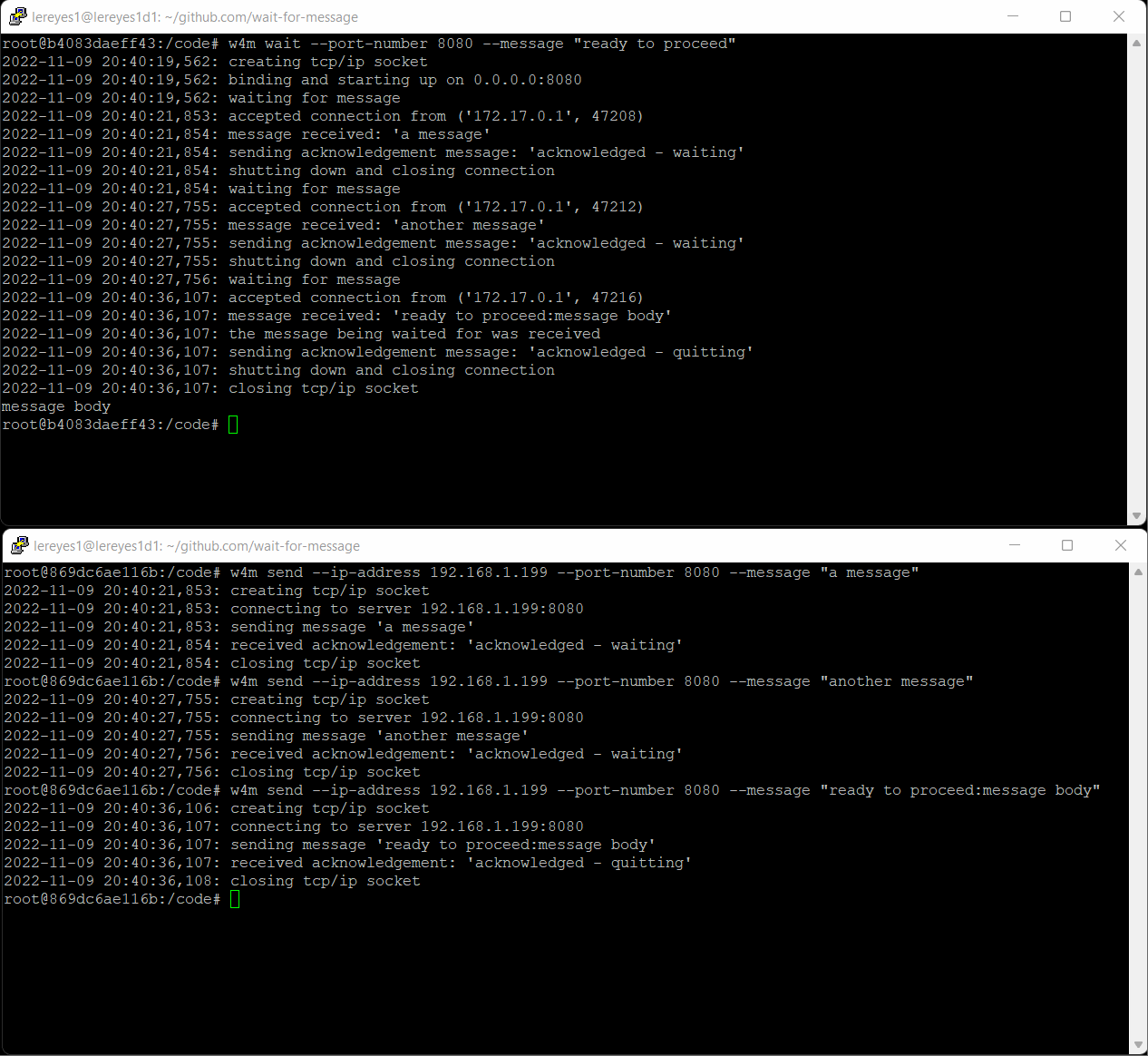
On a Linux machine, start tcp/ip socket listening on port 8080 and wait for message. Note the script blocks until the expected message is received. If the message is not received a timeout error will be thrown. If the message received contains a body it is printed to stdout.
w4m wait --port-number 8080 --message "ready to proceed"
On an other machine (this example we used a Windows machine), connect tcip/ip socket to the ip:port for the server and send several messages. Send will resend message until an acknowledgement is received. If no acknowledgement is received after max attempts a MaxAttemptsError is thrown.
w4m send --ip-address 192.168.1.199 --port-number 8080 --message "a message"
w4m send --ip-address 192.168.1.199 --port-number 8080 --message "another message"
w4m send --ip-address 192.168.1.199 --port-number 8080 --message "ready to proceed:message body"
Build the Docker image:
docker image build \
-t w4m:latest .
Run the Docker container:
docker container run \
--rm \
-it \
-v $PWD:/code \
-p:8080:8080 \
w4m:latest \
bash
FAQs
A simple client server utility that blocks until a message is received on a TCP/IP socket connection
We found that wait-for-message demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
OWASP’s 2025 Top 10 introduces Software Supply Chain Failures as a new category, reflecting rising concern over dependency and build system risks.

Research
/Security News
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.

Security News
Socket CTO Ahmad Nassri discusses why supply chain attacks now target developer machines and what AI means for the future of enterprise security.