
Security News
The Changelog Podcast: Practical Steps to Stay Safe on npm
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.


Sarah Gooding
June 13, 2024
Cyber extortion in the US and Canada has reached unprecedented levels in 2023, according to a recent analysis from Marsh, an insurance broker and risk management firm that handles over 1,800 cyber and technology claims annually. Ransomware attacks surged, with healthcare, communications, retail/wholesale, financial institutions, and education emerging as the top five most affected industry sectors.
One of the unfortunate realities of ransomware is that it often targets vulnerable industries, like healthcare and education, where many organizations are already operating in resource-constrained environments.
The latest high profile ransomware incident, an attack on the pathology firm Synnovis, which has been attributed to Qilin, a Russian group of cyber criminals, highlights this issue. The attack has caused a blood shortage at London hospitals, among other life-threatening disruptions. Marsh reports that the healthcare industry has consistently generated the most claims annually and breach response costs across all industries averaged $1 million between 2019 - 2023.
Although the number of Marsh clients reporting cyber extortion events reached their highest annual level to date, ransom attacks were under 20% of total reported cyber claims in 2022 and 2023.
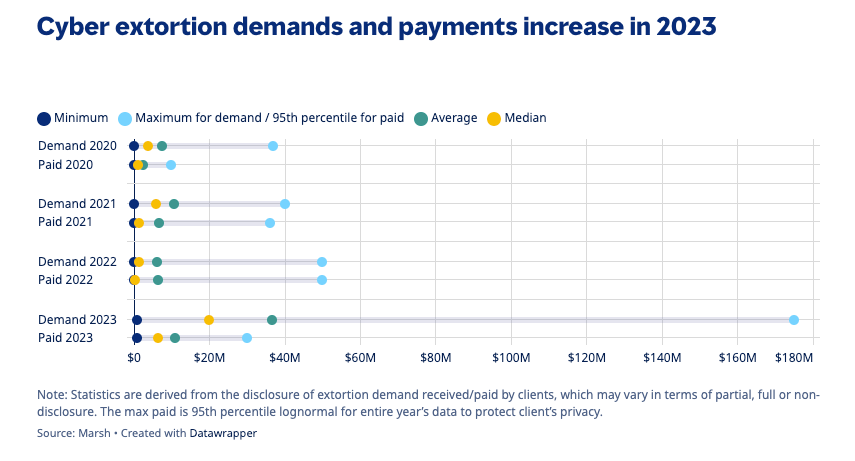
The most startling revelation from this report is the astronomical increase in both median extortion payments and demands:
The median extortion payment dropped from $822,000 in 2021 to $335,000 in 2022. However, this trend was reversed in 2023 as the median payment increased from $335,000 to $6.5 million and the median demand increased from $1.4 million to $20 million as cyber criminals grew bolder. While the decision to pay or not to pay is highly nuanced, organizations should be prepared to respond, including by “practicing” their response under a variety of scenarios.
This is an increase of approximately 1,840.30% on the median payment and 1,328.57% on the median demand in the span of one year.
Marsh did not attribute this increase to any single cause, but several notable ransomware incidents in 2023, where victims have been successfully extorted multiple times, reinforce this business model and potentially contribute to the rising demands.
In contrast to the extraordinarily high extortion demands and payments, Marsh reports that fewer companies are actually paying. Although extortion events are increasing, it appears companies are either getting priced out of paying ransoms or have decided to make a principled stand against paying cyber criminals.
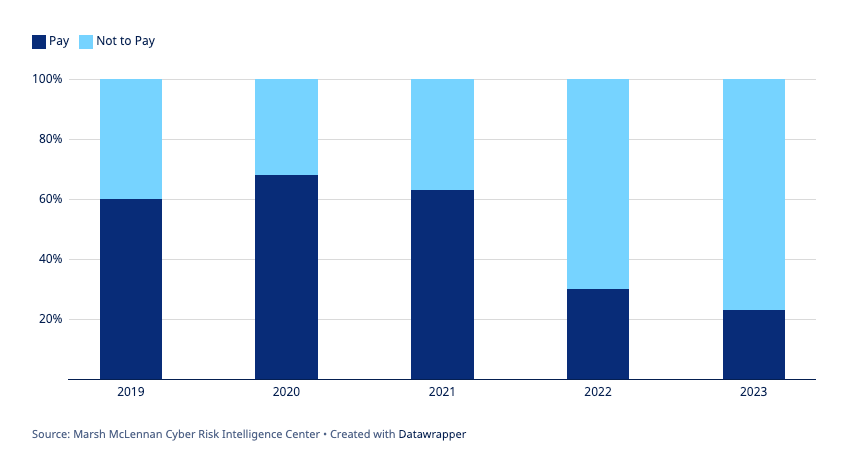
Organizations that choose to pay extortion demands, to reduce operational losses or recover sensitive data, often have cyber insurance that includes coverage for these incidents. With ransomware surging and demands becoming exorbitant, insurance companies have put more security requirements in place in order to mitigate their losses. It’s not surprising that ransomware groups are asking for higher demands in 2023, as fewer companies are paying out.
This shift is contributing to the global push to ban ransom payments, as more evidence suggests that such a ban is gaining momentum. In response to this trend, organizations that do not want to pay extortion demands should focus on enhancing their incident response plans, investing in advanced threat detection, and conducting regular security audits to mitigate vulnerabilities and minimize the potential impact of successful breaches.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.

Security News
Experts push back on new claims about AI-driven ransomware, warning that hype and sponsored research are distorting how the threat is understood.

Security News
Ruby's creator Matz assumes control of RubyGems and Bundler repositories while former maintainers agree to step back and transfer all rights to end the dispute.