
Security News
OWASP 2025 Top 10 Adds Software Supply Chain Failures, Ranked Top Community Concern
OWASP’s 2025 Top 10 introduces Software Supply Chain Failures as a new category, reflecting rising concern over dependency and build system risks.


Sarah Gooding
March 4, 2024
In a new effort to keep secrets out of public repositories, GitHub has enabled push protection by default for all user accounts. This feature prevents accidental leaks of API keys, tokens, and other secrets, a growing problem in open source development where such slips can lead to security vulnerabilities, unauthorized access, and potential data breaches.
GitHub has detected more than 1 million leaked secrets on public repos in the first eight weeks of 2024, more than a dozen every minute.
To give more context for the surprising extent of this problem, TruffleHog, an open source secrets scanning tool that detect secrets, passwords, and sensitive keys in code repositories, found that 74% of all leaked keys were still live/valid 31 days after being leaked. They tracked 10,000 live secrets within 9,399 unique public GitHub files across a 31 day research period and published the results in January 2024:
Trufflehog’s Forager tool, which monitors public commits on Github and package releases on npm, was used for this research. After determining that the keys remained live/valid in more than 50% of cases when exposed keys were removed from GitHub, Trufflehog concluded that developers fundamentally misunderstand the need to rotate the leaked key in order to remediate a leaked credential.
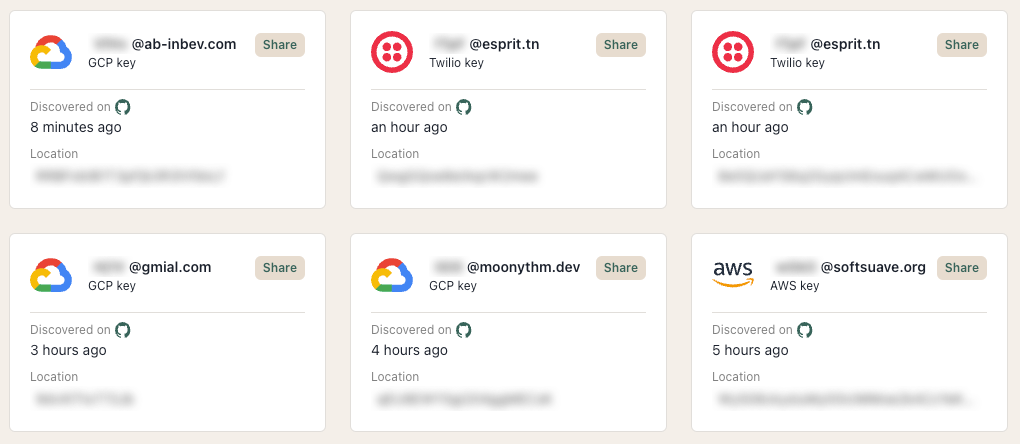
Beyond committing secrets to git repositories, Trufflehog also often detects live API credentials and passwords published in public GitHub comments on issues and pull requests. After sampling a small subset of GitHub’s public PRs and Issue comments, they discovered 721 live API keys and passwords.
Leaked secrets have been responsible for many high-profile breaches as they often provide direct access to private data, systems, and resources, making them a prime target for malicious actors. In 2022, Toyota had an incident where they accidentally exposed a credential allowing access to customer data in a public GitHub repo for nearly five years. More recently, Mercedes-Benz leaked a token in an employee’s GitHub repository, which could have allowed unfettered access to blueprints, cloud access keys, database connection strings, design documents, files, reports, source code, SSO passwords, and more sensitive data.
GitHub’s push protection was first introduced as an opt-in feature for use on a repository level, available to all public repositories in May 2023. Push protection was updated in August 2023 so that users could enable it in their own settings. It blocks commits that contain secrets, no matter where the user is committing code. GitHub also added the ability for organizations to get the number of total secrets intercepted by push protection, as well as the number of successful blocked secrets and the number of bypassed secrets.
Even with push protection turned on by default, users can still bypass it in rare cases where it may offer a false positive. It can also be disabled in settings but is not recommended.
GitHub said its secret scanning detects more than 200 token types and patterns from 180+ service providers. These include Azure, Discord, Google Cloud, AWS, New Relic, OpenAI, Stripe, and most other major providers. Enabling push protection by default is a major step forward towards reducing the overall number of leaked secrets available to threat actors.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
OWASP’s 2025 Top 10 introduces Software Supply Chain Failures as a new category, reflecting rising concern over dependency and build system risks.

Research
/Security News
Socket researchers discovered nine malicious NuGet packages that use time-delayed payloads to crash applications and corrupt industrial control systems.

Security News
Socket CTO Ahmad Nassri discusses why supply chain attacks now target developer machines and what AI means for the future of enterprise security.