Product
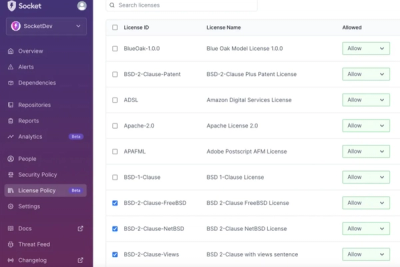
Introducing License Enforcement in Socket
Ensure open-source compliance with Socket’s License Enforcement Beta. Set up your License Policy and secure your software!
go.opentelemetry.io/collector/config/confighttp
HTTP exposes a variety of settings. Several of these settings are available for configuration within individual receivers or exporters.
Exporters leverage client configuration.
Note that client configuration supports TLS configuration, the
configuration parameters are also defined under tls like server
configuration. For more information, see configtls
README.
endpoint: address:porttlsheaders: name/value pairs added to the HTTP request headers
Host header is automatically derived from endpoint value. However, this automatic assignment can be overridden by explicitly setting the Host field in the headers field.Host header is provided then it overrides Host field in Request which results as an override of Host header value.read_buffer_sizetimeoutwrite_buffer_sizecompression: Compression type to use among gzip, zstd, snappy, zlib, and deflate.
none will be treated as uncompressed, and any other inputs will cause an error.max_idle_connsmax_idle_conns_per_hostmax_conns_per_hostidle_conn_timeoutauthdisable_keep_aliveshttp2_read_idle_timeouthttp2_ping_timeoutcookies
enabled] if enabled, the client will store cookies from server responses and reuse them in subsequent requests.Example:
exporter:
otlphttp:
endpoint: otelcol2:55690
auth:
authenticator: some-authenticator-extension
tls:
ca_file: ca.pem
cert_file: cert.pem
key_file: key.pem
headers:
test1: "value1"
"test 2": "value 2"
compression: zstd
cookies:
enabled: true
Receivers leverage server configuration.
cors: Configure CORS,
allowing the receiver to accept traces from web browsers, even if the receiver
is hosted at a different origin. If left blank or set to null, CORS
will not be enabled.
allowed_origins: A list of origins allowed to send requests to
the receiver. An origin may contain a wildcard (*) to replace 0 or more
characters (e.g., https://*.example.com). Do not use a plain wildcard
["*"], as our CORS response includes Access-Control-Allow-Credentials: true, which makes browsers to disallow a plain wildcard (this is a security standard). To allow any origin, you can specify at least the protocol, for example ["https://*", "http://*"]. If no origins are listed, CORS will not be enabled.allowed_headers: Allow CORS requests to include headers outside the
default safelist. By default, safelist headers and
X-Requested-With will be allowed. To allow any request header, set to
["*"].max_age: Sets the value of the Access-Control-Max-Age
header, allowing clients to cache the response to CORS preflight requests. If
not set, browsers use a default of 5 seconds.endpoint: Valid value syntax available heremax_request_body_size: configures the maximum allowed body size in bytes for a single request. Default: 20971520 (20MiB)compression_algorithms: configures the list of compression algorithms the server can accept. Default: ["", "gzip", "zstd", "zlib", "snappy", "deflate"]tlsauth
request_params: a list of query parameter names to add to the auth context, along with the HTTP headersYou can enable attribute processor to append any http header to span's attribute using custom key. You also need to enable the "include_metadata"
Example:
receivers:
otlp:
protocols:
http:
include_metadata: true
auth:
request_params:
- token
authenticator: some-authenticator-extension
cors:
allowed_origins:
- https://foo.bar.com
- https://*.test.com
allowed_headers:
- Example-Header
max_age: 7200
endpoint: 0.0.0.0:55690
compression_algorithms: ["", "gzip"]
processors:
attributes:
actions:
- key: http.client_ip
from_context: X-Forwarded-For
action: upsert
FAQs
Unknown package
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Ensure open-source compliance with Socket’s License Enforcement Beta. Set up your License Policy and secure your software!
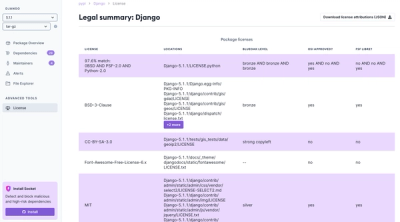
Product
We're launching a new set of license analysis and compliance features for analyzing, managing, and complying with licenses across a range of supported languages and ecosystems.
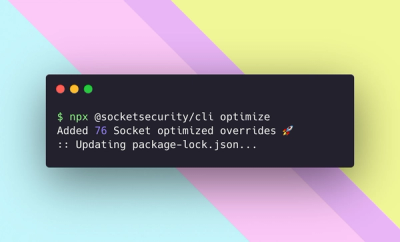
Product
We're excited to introduce Socket Optimize, a powerful CLI command to secure open source dependencies with tested, optimized package overrides.