
Product
Introducing Ruby Support in Socket
Socket is launching Ruby support for all users. Enhance your Rails projects with AI-powered security scans for vulnerabilities and supply chain threats. Now in Beta!
gopkg.in/ammario/isokey.v1
Isokey allows you to make and verify self-contained API keys without a database via HMAC signatures.
isokey.Secret = []byte("super_secret_symmetric_key")
key := isokey.Key{
UserID: 1,
Expires: time.Now().Add(time.Hour * 24),
}
fmt.Printf("Your key is %v", key.Digest())
key, err = isokey.Validate(digest)
if err != nil {
return err
}
//Key secure here
fmt.Printf("%v", key.Made)
The SecretVersion is in included in each key to enable implementors to use multiple secrets.
Use a map
isokey.SecretMap = map[uint32][]byte{
1: []byte("sec1"),
2: []byte("sec2"),
}
Alternatively get full control with a function
isokey.GetSecret = function(key *Key)(secret []byte){
if key.SecretVersion == 1 {
return []byte("sec1")
}
return nil
}
Custom invalidation can be useful if you'd like to support cases where the client has been compromised.
You can invalidate keys like so
isokey.Invalidate = function(key *isokey.Key) bool {
if key.UserID == 10 && key.Made.Before(time.Date(2015, time.November, 10, 23, 0, 0, 0, time.UTC)) {
return true
}
//Make sure to handle expired keys when overriding
if key.Expires.Before(time.Now()) {
return true
}
return false
}
Remember when overriding Invalidate to handle expired keys
All binary values are big endian.
| Field | Type |
|---|---|
| Signature | [16]byte |
| Made Time (Unix epoch timestamp) | uint32 |
| Expire Time (Unix epoch timestamp) | uint32 |
| Secret Version | uint32 |
| User ID | uint32 |
| Flags | uint32 |
Digests are encoded with Bitcoin's base58 alphabet.
It may seem intuitive to put the signature at the end of the digest. It's located at the beginning as it makes eyeballing different keys more easy due to the avalanche effect.
FAQs
Unknown package
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Product
Socket is launching Ruby support for all users. Enhance your Rails projects with AI-powered security scans for vulnerabilities and supply chain threats. Now in Beta!
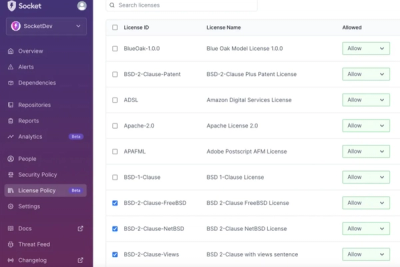
Product
Ensure open-source compliance with Socket’s License Enforcement Beta. Set up your License Policy and secure your software!
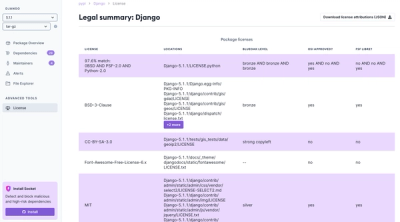
Product
We're launching a new set of license analysis and compliance features for analyzing, managing, and complying with licenses across a range of supported languages and ecosystems.