
Security News
Input Validation Vulnerabilities Dominate MITRE's 2024 CWE Top 25 List
MITRE's 2024 CWE Top 25 highlights critical software vulnerabilities like XSS, SQL Injection, and CSRF, reflecting shifts due to a refined ranking methodology.
@a_kawashiro/jendeley
Advanced tools
`jendeley` is a JSON-based document organizing software. - `jendeley` is JSON-based. You can see and edit your database easily. - `jendeley` works locally. Your important database is owned only by you. Not cloud. - `jendeley` is browser based. You can run
jendeley is a JSON-based document organizing software.
jendeley is JSON-based. You can see and edit your database easily.jendeley works locally. Your important database is owned only by you. Not cloud.jendeley is browser based. You can run it anywhere node.js runs.npm install @a_kawashiro/jendeley -g
jendeley scan --papers_dir <YOUR PDFs DIR>
jendeley launch --db <YOUR PDFs DIR>/jendeley_db.json
Then you can see a screen like this!
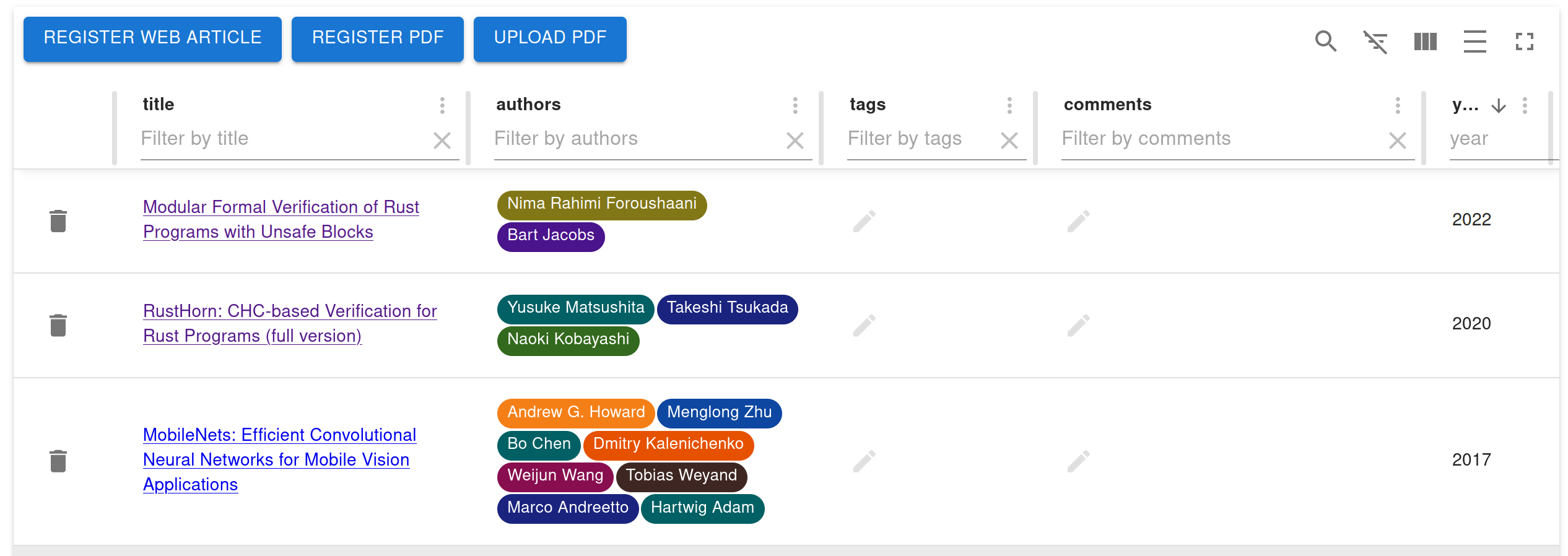
Please check user document for more details.
FAQs
`jendeley` is a JSON-based document organizing software. - `jendeley` is JSON-based. You can see and edit your database quickly. - `jendeley` works locally. Your important database is owned only by you. No cloud. - `jendeley` is browser-based. You can run
The npm package @a_kawashiro/jendeley receives a total of 6 weekly downloads. As such, @a_kawashiro/jendeley popularity was classified as not popular.
We found that @a_kawashiro/jendeley demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 0 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
MITRE's 2024 CWE Top 25 highlights critical software vulnerabilities like XSS, SQL Injection, and CSRF, reflecting shifts due to a refined ranking methodology.

Security News
In this segment of the Risky Business podcast, Feross Aboukhadijeh and Patrick Gray discuss the challenges of tracking malware discovered in open source softare.

Research
Security News
A threat actor's playbook for exploiting the npm ecosystem was exposed on the dark web, detailing how to build a blockchain-powered botnet.