@axa-fr/react-oidc






@axa-fr/oidc-client the lightest and securest library to manage authentication with OpenID Connect (OIDC) and OAuth2 protocol. It is compatible with all OIDC providers.
@axa-fr/oidc-client is a pure javascript library. It works with any JavaScript framework or library.
We provide a wrapper @axa-fr/react-oidc for React (compatible next.js) and we expect soon to provide one for Vue, Angular and Svelte.
About
@axa-fr/react is:
- Secure :
- With Demonstrating Proof of Possession (DPoP), your access_token and refresh_token are not usable outside your browser context (big protection)
- With the use of Service Worker, your tokens (refresh_token and/or access_token) are not accessible to the JavaScript client code (if you follow good practices from
FAQ section) - OIDC using client side Code Credential Grant with pkce only
- Lightweight : Unpacked Size on npm is 274 kB
- Simple
- refresh_token and access_token are auto refreshed in background
- with the use of the Service Worker, you do not need to inject the access_token in every fetch, you have only to configure OidcTrustedDomains.js file
- Multiple Authentication :
- You can authenticate many times to the same provider with different scope (for example you can acquire a new 'payment' scope for a payment)
- You can authenticate to multiple different providers inside the same SPA (single page application) website
- Flexible :
- Work with Service Worker (more secure) and without for older browser (less secure).
- You can disable Service Worker if you want (but less secure) and just use SessionStorage or LocalStorage mode.

The service worker catch access_token and refresh_token that will never be accessible to the client.
Getting Started
npm install @axa-fr/react-oidc --save
node ./node_modules/@axa-fr/react-oidc/bin/copy-service-worker-files.mjs public
WARNING : If you use Service Worker mode, the OidcServiceWorker.js file should always be up to date with the version of the library. You may setup a postinstall script in your package.json file to update it at each npm install. For example :
"scripts": {
...
"postinstall": "node ./node_modules/@axa-fr/react-oidc/bin/copy-service-worker-files.mjs public"
},
If you need a very secure mode where refresh_token and access_token will be hide behind a service worker that will proxify requests.
The only file you should edit is "OidcTrustedDomains.js".
const trustedDomains = {
default: {
oidcDomains :["https://demo.duendesoftware.com"],
accessTokenDomains : ["https://www.myapi.com/users"]
},
};
trustedDomains.config_show_access_token = {
oidcDomains :["https://demo.duendesoftware.com"],
accessTokenDomains : ["https://www.myapi.com/users"],
showAccessToken: true,
};
trustedDomains.config_with_dpop = {
domains: ["https://demo.duendesoftware.com"],
demonstratingProofOfPossession: true,
demonstratingProofOfPossessionOnlyWhenDpopHeaderPresent: true,
};
Run The Demo
git clone https://github.com/AxaFrance/oidc-client.git
cd oidc-client
pnpm install
cd /examples/react-oidc-demo
pnpm install
pnpm start
Examples
Application startup
The library is router agnostic and use native History API.
The default routes used internally :
import React from "react";
import { render } from "react-dom";
import { BrowserRouter as Router } from "react-router-dom";
import { OidcProvider } from "@axa-fr/react-oidc";
import Header from "./Layout/Header";
import Routes from "./Router";
const configuration = {
client_id: "interactive.public.short",
redirect_uri: window.location.origin + "/authentication/callback",
silent_redirect_uri:
window.location.origin + "/authentication/silent-callback",
scope: "openid profile email api offline_access",
authority: "https://demo.duendesoftware.com",
service_worker_relative_url: "/OidcServiceWorker.js",
service_worker_only: false,
demonstrating_proof_of_possession: false,
};
const App = () => (
<OidcProvider configuration={configuration}>
<Router>
<Header />
<Routes />
</Router>
</OidcProvider>
);
render(<App />, document.getElementById("root"));
const configuration = {
loadingComponent: ReactComponent,
sessionLostComponent: ReactComponent,
authenticating: ReactComponent,
authenticatingErrorComponent: ReactComponent,
callbackSuccessComponent: ReactComponent,
serviceWorkerNotSupportedComponent: ReactComponent,
onSessionLost: Function,
configuration: {
client_id: String.isRequired,
redirect_uri: String.isRequired,
silent_redirect_uri: String,
silent_login_uri: String,
silent_login_timeout: Number,
scope: String.isRequired,
authority: String.isRequired,
storage: Storage,
authority_configuration: {
authorization_endpoint: String,
token_endpoint: String,
userinfo_endpoint: String,
end_session_endpoint: String,
revocation_endpoint: String,
check_session_iframe: String,
issuer: String,
},
refresh_time_before_tokens_expiration_in_second: Number,
service_worker_relative_url: String,
service_worker_keep_alive_path: String,
service_worker_only: Boolean,
service_worker_activate: () => boolean,
service_worker_update_require_callback: (registration:any, stopKeepAlive:Function) => Promise<void>,
service_worker_register: (url: string) => Promise<ServiceWorkerRegistration>,
extras: StringMap | undefined,
token_request_extras: StringMap | undefined,
withCustomHistory: Function,
authority_time_cache_wellknowurl_in_second: 60 * 60,
authority_timeout_wellknowurl_in_millisecond: 10000,
monitor_session: Boolean,
onLogoutFromAnotherTab: Function,
onLogoutFromSameTab: Function,
token_renew_mode: String,
token_automatic_renew_mode: TokenAutomaticRenewMode.AutomaticOnlyWhenFetchExecuted,
logout_tokens_to_invalidate: Array<string>,
location: ILOidcLocation,
demonstrating_proof_of_possession: Boolean,
demonstrating_proof_of_possession_configuration: DemonstratingProofOfPossessionConfiguration
},
};
demonstrating_proof_of_possession_configuration: DemonstratingProofOfPossessionConfiguration
};
interface DemonstratingProofOfPossessionConfiguration {
generateKeyAlgorithm: RsaHashedKeyGenParams | EcKeyGenParams,
digestAlgorithm: AlgorithmIdentifier,
importKeyAlgorithm: AlgorithmIdentifier | RsaHashedImportParams | EcKeyImportParams | HmacImportParams | AesKeyAlgorithm,
signAlgorithm: AlgorithmIdentifier | RsaPssParams | EcdsaParams,
jwtHeaderAlgorithm: string
};
const defaultDemonstratingProofOfPossessionConfiguration: DemonstratingProofOfPossessionConfiguration ={
importKeyAlgorithm: {
name: 'ECDSA',
namedCurve: 'P-256',
hash: {name: 'ES256'}
},
signAlgorithm: {name: 'ECDSA', hash: {name: 'SHA-256'}},
generateKeyAlgorithm: {
name: 'ECDSA',
namedCurve: 'P-256'
},
digestAlgorithm: { name: 'SHA-256' },
jwtHeaderAlgorithm : 'ES256'
};
How to consume
"useOidc" returns all props from the Hook :
import React from "react";
import { useOidc } from "./oidc";
export const Home = () => {
const { login, logout, renewTokens, isAuthenticated } = useOidc();
return (
<div className="container-fluid mt-3">
<div className="card">
<div className="card-body">
<h5 className="card-title">Welcome !!!</h5>
<p className="card-text">
React Demo Application protected by OpenId Connect
</p>
{!isAuthenticated && (
<button
type="button"
className="btn btn-primary"
onClick={() => login("/profile")}
>
Login
</button>
)}
{isAuthenticated && (
<button
type="button"
className="btn btn-primary"
onClick={() => logout()}
>
logout
</button>
)}
{isAuthenticated && (
<button
type="button"
className="btn btn-primary"
onClick={() => renewTokens()}
>
renewTokens
</button>
)}
</div>
</div>
</div>
);
};
The Hook method exposes :
- isAuthenticated : if the user is logged in or not
- logout: logout function (return a promise)
- login: login function 'return a promise'
- renewTokens: renew tokens function 'return a promise'
How to secure a component
OidcSecure component trigger authentication in case user is not authenticated. So, the children of that component can be accessible only once you are connected.
import React from "react";
import { OidcSecure } from "@axa-fr/react-oidc";
const AdminSecure = () => (
<OidcSecure>
<h1>My sub component</h1>}
</OidcSecure>
);
export default AdminSecure;
How to secure a component : HOC method
"withOidcSecure" act the same as "OidcSecure" it also trigger authentication in case user is not authenticated.
import React from "react";
import { Switch, Route } from "react-router-dom";
import { withOidcSecure } from "@axa-fr/react-oidc";
import Home from "../Pages/Home";
import Dashboard from "../Pages/Dashboard";
import Admin from "../Pages/Admin";
const Routes = () => (
<Switch>
<Route exact path="/" component={Home} />
<Route path="/dashboard" component={withOidcSecure(Dashboard)} />
<Route path="/admin" component={Admin} />
<Route path="/home" component={Home} />
</Switch>
);
export default Routes;
How to get "Access Token" : Hook method
import { useOidcAccessToken } from "@axa-fr/react-oidc";
const DisplayAccessToken = () => {
const { accessToken, accessTokenPayload } = useOidcAccessToken();
if (!accessToken) {
return <p>you are not authentified</p>;
}
return (
<div className="card text-white bg-info mb-3">
<div className="card-body">
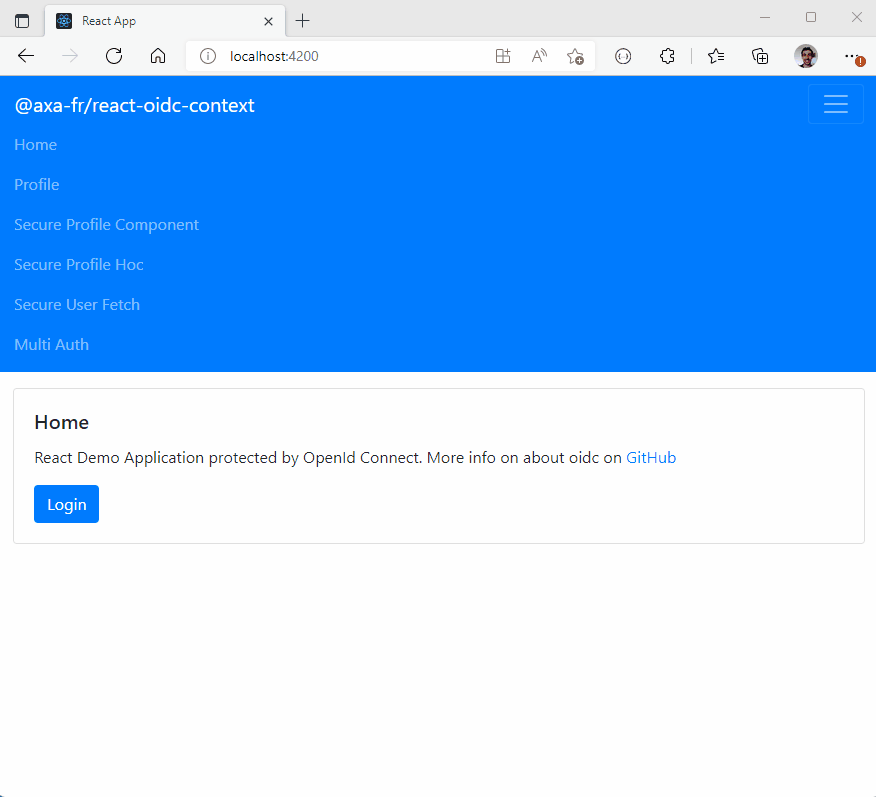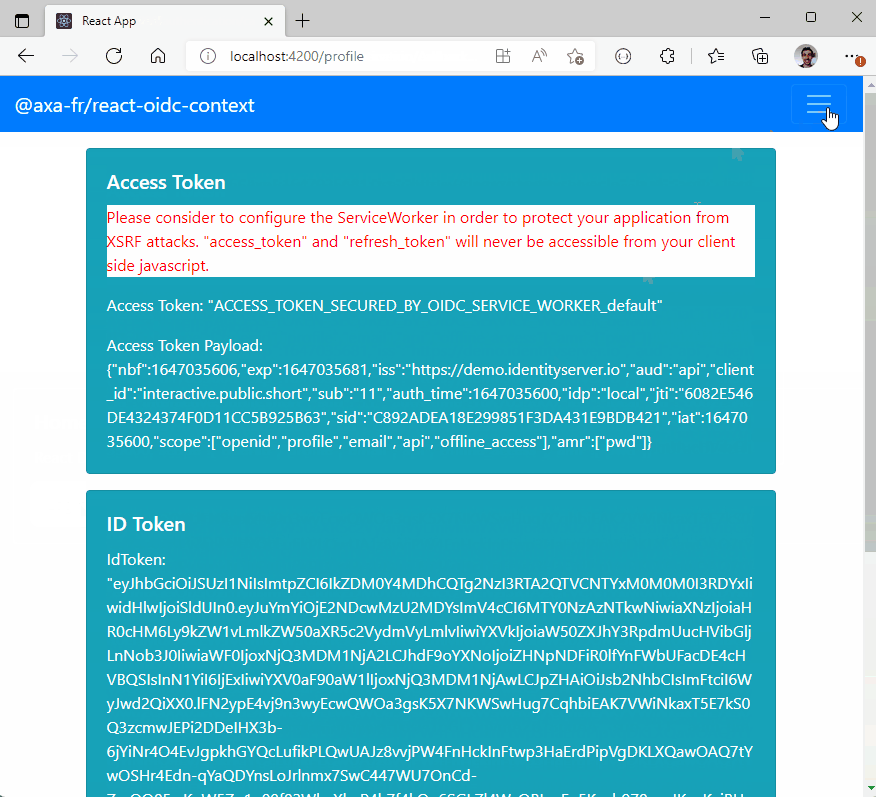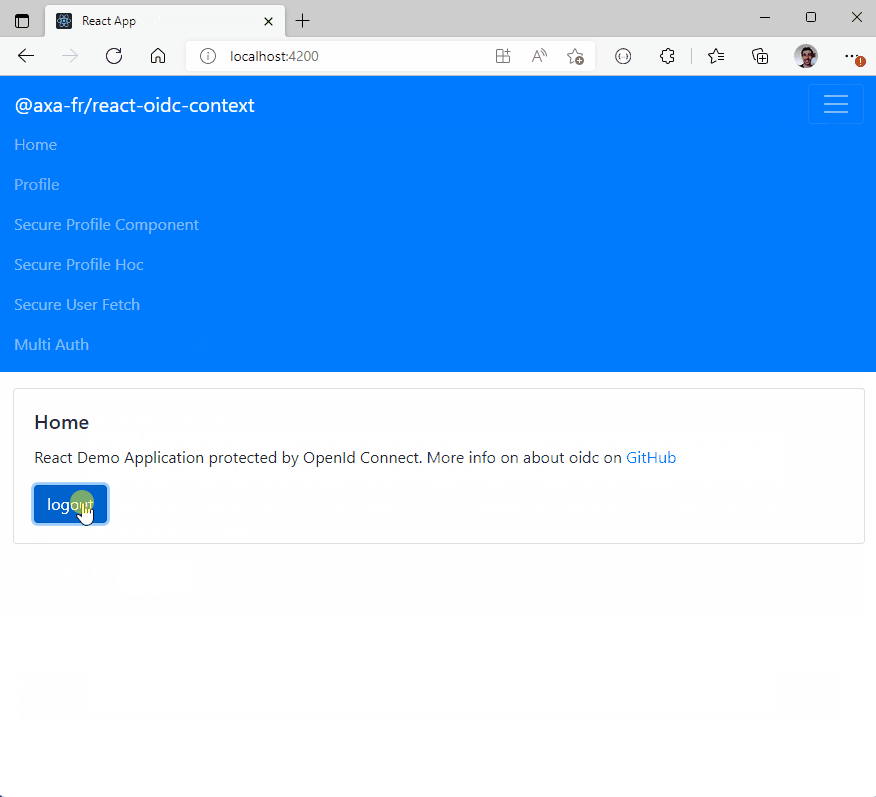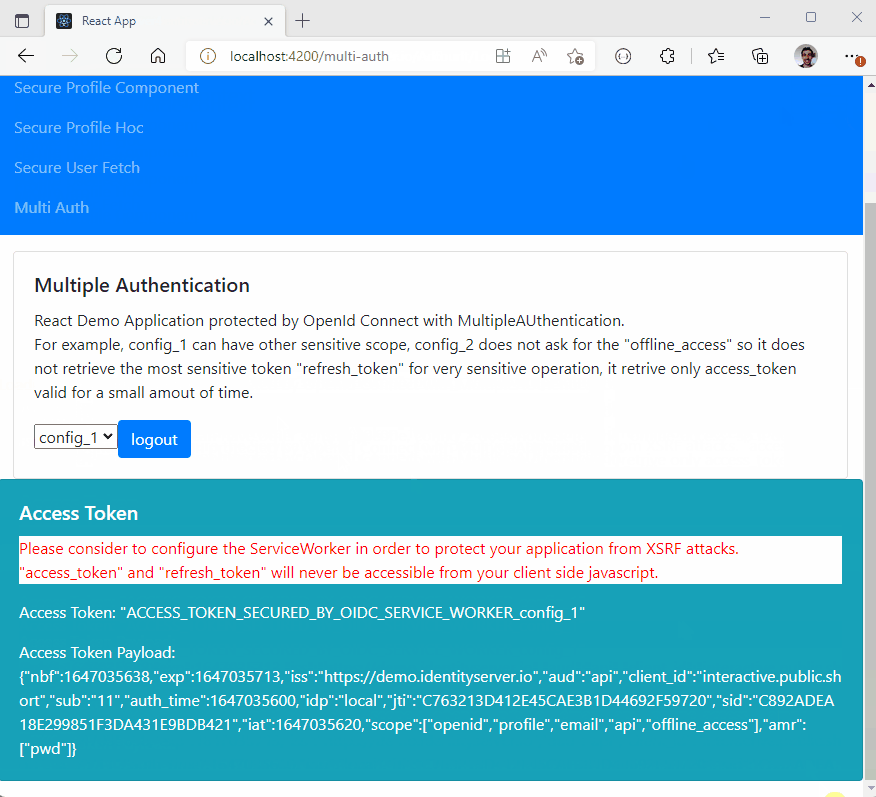
<h5 className="card-title">Access Token</h5>
<p style={{ color: "red", backgroundColor: "white" }}>
Please consider to configure the ServiceWorker in order to protect
your application from XSRF attacks. ""access_token" and
"refresh_token" will never be accessible from your client side
javascript.
</p>
{<p className="card-text">{JSON.stringify(accessToken)}</p>}
{accessTokenPayload != null && (
<p className="card-text">{JSON.stringify(accessTokenPayload)}</p>
)}
</div>
</div>
);
};
How to get IDToken : Hook method
import { useOidcIdToken } from "@axa-fr/react-oidc";
const DisplayIdToken = () => {
const { idToken, idTokenPayload } = useOidcIdToken();
if (!idToken) {
return <p>you are not authentified</p>;
}
return (
<div className="card text-white bg-info mb-3">
<div className="card-body">
<h5 className="card-title">ID Token</h5>
{<p className="card-text">{JSON.stringify(idToken)}</p>}
{idTokenPayload != null && (
<p className="card-text">{JSON.stringify(idTokenPayload)}</p>
)}
</div>
</div>
);
};
How to get User Information : Hook method
import { useOidcUser, UserStatus } from "@axa-fr/react-oidc";
const DisplayUserInfo = () => {
const { oidcUser, oidcUserLoadingState } = useOidcUser();
switch (oidcUserLoadingState) {
case UserStatus.Loading:
return <p>User Information are loading</p>;
case UserStatus.Unauthenticated:
return <p>you are not authenticated</p>;
case UserStatus.LoadingError:
return <p>Fail to load user information</p>;
default:
return (
<div className="card text-white bg-success mb-3">
<div className="card-body">
<h5 className="card-title">User information</h5>
<p className="card-text">{JSON.stringify(oidcUser)}</p>
</div>
</div>
);
}
};
How to get a fetch that inject Access_Token : Hook method
If your are not using the service worker. Fetch function need to send AccessToken.
This Hook give you a wrapped fetch that add the access token for you.
import React, { useEffect, useState } from "react";
import { useOidcFetch, OidcSecure } from "@axa-fr/react-oidc";
const DisplayUserInfo = ({ fetch }) => {
const [oidcUser, setOidcUser] = useState(null);
const [isLoading, setLoading] = useState(true);
useEffect(() => {
const fetchUserInfoAsync = async () => {
const res = await fetch(
"https://demo.duendesoftware.com/connect/userinfo",
);
if (res.status != 200) {
return null;
}
return res.json();
};
let isMounted = true;
fetchUserInfoAsync().then((userInfo) => {
if (isMounted) {
setLoading(false);
setOidcUser(userInfo);
}
});
return () => {
isMounted = false;
};
}, []);
if (isLoading) {
return <>Loading</>;
}
return (
<div className="container mt-3">
<div className="card text-white bg-success mb-3">
<div className="card-body">
<h5 className="card-title">User information</h5>
{oidcUser != null && (
<p className="card-text">{JSON.stringify(oidcUser)}</p>
)}
</div>
</div>
</div>
);
};
export const FetchUserHook = () => {
const { fetch } = useOidcFetch();
return (
<OidcSecure>
<DisplayUserInfo fetch={fetch} />
</OidcSecure>
);
};
How to get a fetch that inject Access_Token : HOC method
If your are not using the service worker. Fetch function need to send AccessToken.
This HOC give you a wrapped fetch that add the access token for you.
import React, { useEffect, useState } from "react";
import { useOidcFetch, OidcSecure } from "@axa-fr/react-oidc";
const DisplayUserInfo = ({ fetch }) => {
const [oidcUser, setOidcUser] = useState(null);
const [isLoading, setLoading] = useState(true);
useEffect(() => {
const fetchUserInfoAsync = async () => {
const res = await fetch(
"https://demo.duendesoftware.com/connect/userinfo",
);
if (res.status != 200) {
return null;
}
return res.json();
};
let isMounted = true;
fetchUserInfoAsync().then((userInfo) => {
if (isMounted) {
setLoading(false);
setOidcUser(userInfo);
}
});
return () => {
isMounted = false;
};
}, []);
if (isLoading) {
return <>Loading</>;
}
return (
<div className="container mt-3">
<div className="card text-white bg-success mb-3">
<div className="card-body">
<h5 className="card-title">User information</h5>
{oidcUser != null && (
<p className="card-text">{JSON.stringify(oidcUser)}</p>
)}
</div>
</div>
</div>
);
};
const UserInfoWithFetchHoc = withOidcFetch(fetch)(DisplayUserInfo);
export const FetchUserHoc = () => (
<OidcSecure>
<UserInfoWithFetchHoc />
</OidcSecure>
);
Components override
You can inject your own components.
All components definition receive props configurationName. Please checkout the demo for more complete example.
import React from "react";
import { render } from "react-dom";
import { BrowserRouter as Router } from "react-router-dom";
import { OidcProvider } from "@axa-fr/react-oidc";
import Header from "./Layout/Header";
import Routes from "./Router";
const configuration = {
client_id: "interactive.public.short",
redirect_uri: "http://localhost:4200/authentication/callback",
silent_redirect_uri: "http://localhost:4200/authentication/silent-callback",
scope: "openid profile email api offline_access",
authority: "https://demo.identityserver.io",
service_worker_relative_url: "/OidcServiceWorker.js",
service_worker_only: false,
};
const Loading = () => <p>Loading</p>;
const AuthenticatingError = () => <p>Authenticating error</p>;
const Authenticating = () => <p>Authenticating</p>;
const SessionLost = () => <p>Session Lost</p>;
const ServiceWorkerNotSupported = () => <p>Not supported</p>;
const CallBackSuccess = () => <p>Success</p>;
const App = () => (
<OidcProvider
configuration={configuration}
loadingComponent={Loading}
authenticatingErrorComponent={AuthenticatingError}
authenticatingComponent={Authenticating}
sessionLostComponent={SessionLost}
//onSessionLost={onSessionLost} // If set "sessionLostComponent" is not displayed and onSessionLost callback is called instead
serviceWorkerNotSupportedComponent={ServiceWorkerNotSupported}
callbackSuccessComponent={CallBackSuccess}
>
{/* isSessionLost && <SessionLost />*/}
<Router>
<Header />
<Routes />
</Router>
</OidcProvider>
);
render(<App />, document.getElementById("root"));
How It Works
These components encapsulate the use of "@axa-fr/vanilla-oidc" in order to hide workflow complexity.
Internally, native History API is used to be router library agnostic.
More information about OIDC
NextJS
To work with NextJS you need to inject your own history surcharge like the sample below.
component/layout.js
import { OidcProvider } from "@axa-fr/react-oidc";
import { useRouter } from "next/router";
const configuration = {
client_id: "interactive.public.short",
redirect_uri: "http://localhost:3001/#authentication/callback",
silent_redirect_uri: "http://localhost:3001/#authentication/silent-callback",
scope: "openid profile email api offline_access",
authority: "https://demo.duendesoftware.com",
};
const onEvent = (configurationName, eventName, data) => {
console.log(`oidc:${configurationName}:${eventName}`, data);
};
export default function Layout({ children }) {
const router = useRouter();
const withCustomHistory = () => {
return {
replaceState: (url) => {
router
.replace({
pathname: url,
})
.then(() => {
window.dispatchEvent(new Event("popstate"));
});
},
};
};
return (
<>
<OidcProvider
configuration={configuration}
onEvent={onEvent}
withCustomHistory={withCustomHistory}
>
<main>{children}</main>
</OidcProvider>
</>
);
}
For more information checkout the NextJS React OIDC demo
Hash route
react-oidc work also with hash router.
export const configurationIdentityServerWithHash = {
client_id: "interactive.public.short",
redirect_uri: window.location.origin + "#authentication-callback",
silent_redirect_uri:
window.location.origin + "#authentication-silent-callback",
scope: "openid profile email api offline_access",
authority: "https://demo.duendesoftware.com",
refresh_time_before_tokens_expiration_in_second: 70,
service_worker_relative_url: "/OidcServiceWorker.js",
service_worker_only: false,
};






