react-native-keychain-manager
Advanced tools
react-native-keychain-manager - npm Package Compare versions
Comparing version 1.1.2 to 1.2.0
| { | ||
| "name": "react-native-keychain-manager", | ||
| "version": "1.1.2", | ||
| "version": "1.2.0", | ||
| "description": "Keychain Access for React Native", | ||
@@ -5,0 +5,0 @@ "main": "./lib/commonjs/index.js", |
@@ -458,3 +458,3 @@ <h1 align="center">react-native-keychain-manager</h1> | ||
| Encrypted data is stored in SharedPreferences. | ||
| Encrypted data is stored in DataStore Preferences. | ||
@@ -511,8 +511,6 @@ The `setInternetCredentials(server, username, password)` call will be resolved as call to `setGenericPassword(username, password, server)`. Use the `server` argument to distinguish between multiple entries. | ||
| On API levels that do not support Android keystore, Facebook Conceal is used to en/decrypt stored data. The encrypted data is then stored in SharedPreferences. Since Conceal itself stores its encryption key in SharedPreferences, it follows that if the device is rooted (or if an attacker can somehow access the filesystem), the key can be obtained and the stored data can be decrypted. Therefore, on such a device, the conceal encryption is only an obscurity. On API level 23+ the key is stored in the Android Keystore, which makes the key non-exportable and therefore makes the entire process more secure. Follow best practices and do not store user credentials on a device. Instead use tokens or other forms of authentication and re-ask for user credentials before performing sensitive operations. | ||
| On API levels that do not support Android keystore, Facebook Conceal is used to en/decrypt stored data. The encrypted data is then stored in DataStore Preferences. Since Conceal itself stores its encryption key in DataStore Preferences, it follows that if the device is rooted (or if an attacker can somehow access the filesystem), the key can be obtained and the stored data can be decrypted. Therefore, on such a device, the conceal encryption is only an obscurity. On API level 23+ the key is stored in the Android Keystore, which makes the key non-exportable and therefore makes the entire process more secure. Follow best practices and do not store user credentials on a device. Instead use tokens or other forms of authentication and re-ask for user credentials before performing sensitive operations. | ||
| 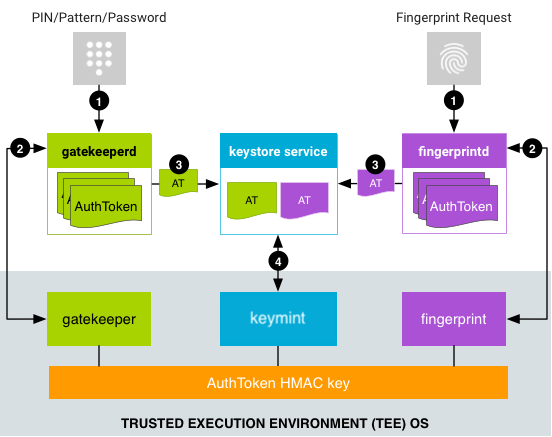 | ||
| - [Android authentication](https://source.android.com/security/authentication) | ||
| - [Android Cipher](https://developer.android.com/guide/topics/security/cryptography) | ||
| - [Android Protected Confirmation](https://developer.android.com/training/articles/security-android-protected-confirmation) |
Sorry, the diff of this file is not supported yet
Sorry, the diff of this file is not supported yet
Sorry, the diff of this file is not supported yet
Sorry, the diff of this file is not supported yet
New alerts
License Policy Violation
LicenseThis package is not allowed per your license policy. Review the package's license to ensure compliance.
Found 1 instance in 1 package
Fixed alerts
License Policy Violation
LicenseThis package is not allowed per your license policy. Review the package's license to ensure compliance.
Found 1 instance in 1 package
AI-detected possible typosquat
Supply chain riskAI has identified this package as a potential typosquat of a more popular package. This suggests that the package may be intentionally mimicking another package's name, description, or other metadata.
Found 1 instance in 1 package
Improved metrics
- Total package byte prevSize
- increased by0.74%
250731
- Number of package files
- increased by2.56%
40
- Lines of code
- increased by227.03%
3545
- Number of medium supply chain risk alerts
- decreased by-100%
0
Worsened metrics
- Number of lines in readme file
- decreased by-0.39%
515