supertokens-website
Advanced tools
supertokens-website - npm Package Compare versions
Comparing version 13.0.1 to 13.0.2
@@ -10,2 +10,9 @@ # Changelog | ||
| ## [13.0.2] - 2022-08-11 | ||
| ### Changes | ||
| - Updates README | ||
| - Updates dependencies to fix building in node 17 + match typescript version of auth-react | ||
| - Refactors the way the SDK exports the error class | ||
| ## [13.0.1] - 2022-06-27 | ||
@@ -12,0 +19,0 @@ - Fixes node dependency for integration tests |
| import { AxiosPromise, AxiosRequestConfig, AxiosResponse } from "axios"; | ||
| export declare function interceptorFunctionRequestFulfilled(config: AxiosRequestConfig): Promise<AxiosRequestConfig<any>>; | ||
| export declare function responseInterceptor(axiosInstance: any): (response: AxiosResponse<any, any>) => Promise<AxiosResponse<any, any>>; | ||
| export declare function responseInterceptor(axiosInstance: any): (response: AxiosResponse) => Promise<AxiosResponse<any, any>>; | ||
| export declare function responseErrorInterceptor(axiosInstance: any): (error: any) => Promise<AxiosResponse<any, any>>; | ||
@@ -16,3 +16,3 @@ /** | ||
| */ | ||
| static doRequest: (httpCall: (config: AxiosRequestConfig<any>) => AxiosPromise<any>, config: AxiosRequestConfig<any>, url?: string | undefined, prevResponse?: AxiosResponse<any, any> | undefined, prevError?: any, viaInterceptor?: boolean) => Promise<AxiosResponse<any, any>>; | ||
| static doRequest: (httpCall: (config: AxiosRequestConfig) => AxiosPromise<any>, config: AxiosRequestConfig, url?: string, prevResponse?: AxiosResponse, prevError?: any, viaInterceptor?: boolean) => Promise<AxiosResponse<any>>; | ||
| } |
@@ -148,2 +148,3 @@ "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.responseErrorInterceptor = exports.responseInterceptor = exports.interceptorFunctionRequestFulfilled = void 0; | ||
| var axiosError_1 = require("./axiosError"); | ||
@@ -175,3 +176,3 @@ var fetch_1 = require("./fetch"); | ||
| case 0: | ||
| logger_1.logDebugMessage("interceptorFunctionRequestFulfilled: started axios interception"); | ||
| (0, logger_1.logDebugMessage)("interceptorFunctionRequestFulfilled: started axios interception"); | ||
| url = getUrlFromConfig(config); | ||
@@ -182,3 +183,3 @@ doNotDoInterception = false; | ||
| typeof url === "string" && | ||
| !utils_1.shouldDoInterceptionBasedOnUrl( | ||
| !(0, utils_1.shouldDoInterceptionBasedOnUrl)( | ||
| url, | ||
@@ -190,7 +191,7 @@ fetch_1.default.config.apiDomain, | ||
| if (err.message === "Please provide a valid domain name") { | ||
| logger_1.logDebugMessage( | ||
| (0, logger_1.logDebugMessage)( | ||
| "interceptorFunctionRequestFulfilled: Trying shouldDoInterceptionBasedOnUrl with location.origin" | ||
| ); | ||
| // .origin gives the port as well.. | ||
| doNotDoInterception = !utils_1.shouldDoInterceptionBasedOnUrl( | ||
| doNotDoInterception = !(0, utils_1.shouldDoInterceptionBasedOnUrl)( | ||
| windowHandler_1.default.getReferenceOrThrow().windowHandler.location.getOrigin(), | ||
@@ -204,15 +205,16 @@ fetch_1.default.config.apiDomain, | ||
| } | ||
| logger_1.logDebugMessage( | ||
| "interceptorFunctionRequestFulfilled: Value of doNotDoInterception: " + doNotDoInterception | ||
| ); | ||
| (0, | ||
| logger_1.logDebugMessage)("interceptorFunctionRequestFulfilled: Value of doNotDoInterception: " + doNotDoInterception); | ||
| if (doNotDoInterception) { | ||
| logger_1.logDebugMessage("interceptorFunctionRequestFulfilled: Returning config unchanged"); | ||
| (0, logger_1.logDebugMessage)( | ||
| "interceptorFunctionRequestFulfilled: Returning config unchanged" | ||
| ); | ||
| // this check means that if you are using axios via inteceptor, then we only do the refresh steps if you are calling your APIs. | ||
| return [2 /*return*/, config]; | ||
| } | ||
| logger_1.logDebugMessage("interceptorFunctionRequestFulfilled: Modifying config"); | ||
| (0, logger_1.logDebugMessage)("interceptorFunctionRequestFulfilled: Modifying config"); | ||
| processState_1.ProcessState.getInstance().addState( | ||
| processState_1.PROCESS_STATE.CALLING_INTERCEPTION_REQUEST | ||
| ); | ||
| return [4 /*yield*/, fetch_1.getIdRefreshToken(true)]; | ||
| return [4 /*yield*/, (0, fetch_1.getIdRefreshToken)(true)]; | ||
| case 1: | ||
@@ -226,3 +228,3 @@ preRequestIdToken = _a.sent(); | ||
| if (antiCsrfToken !== undefined) { | ||
| logger_1.logDebugMessage( | ||
| (0, logger_1.logDebugMessage)( | ||
| "interceptorFunctionRequestFulfilled: Adding anti-csrf token to request" | ||
@@ -242,9 +244,10 @@ ); | ||
| if (fetch_1.default.config.autoAddCredentials && configWithAntiCsrf.withCredentials === undefined) { | ||
| logger_1.logDebugMessage("interceptorFunctionRequestFulfilled: Adding credentials include"); | ||
| (0, logger_1.logDebugMessage)( | ||
| "interceptorFunctionRequestFulfilled: Adding credentials include" | ||
| ); | ||
| configWithAntiCsrf = __assign(__assign({}, configWithAntiCsrf), { withCredentials: true }); | ||
| } | ||
| // adding rid for anti-csrf protection: Anti-csrf via custom header | ||
| logger_1.logDebugMessage( | ||
| "interceptorFunctionRequestFulfilled: Adding rid header: anti-csrf (it may be overriden by the user's provided rid)" | ||
| ); | ||
| (0, | ||
| logger_1.logDebugMessage)("interceptorFunctionRequestFulfilled: Adding rid header: anti-csrf (it may be overriden by the user's provided rid)"); | ||
| configWithAntiCsrf = __assign(__assign({}, configWithAntiCsrf), { | ||
@@ -258,3 +261,3 @@ headers: | ||
| }); | ||
| logger_1.logDebugMessage("interceptorFunctionRequestFulfilled: returning modified config"); | ||
| (0, logger_1.logDebugMessage)("interceptorFunctionRequestFulfilled: returning modified config"); | ||
| return [2 /*return*/, configWithAntiCsrf]; | ||
@@ -281,3 +284,3 @@ } | ||
| } | ||
| logger_1.logDebugMessage("responseInterceptor: started"); | ||
| (0, logger_1.logDebugMessage)("responseInterceptor: started"); | ||
| url = getUrlFromConfig(response.config); | ||
@@ -287,3 +290,3 @@ try { | ||
| typeof url === "string" && | ||
| !utils_1.shouldDoInterceptionBasedOnUrl( | ||
| !(0, utils_1.shouldDoInterceptionBasedOnUrl)( | ||
| url, | ||
@@ -295,7 +298,7 @@ fetch_1.default.config.apiDomain, | ||
| if (err.message === "Please provide a valid domain name") { | ||
| logger_1.logDebugMessage( | ||
| (0, logger_1.logDebugMessage)( | ||
| "responseInterceptor: Trying shouldDoInterceptionBasedOnUrl with location.origin" | ||
| ); | ||
| // .origin gives the port as well.. | ||
| doNotDoInterception = !utils_1.shouldDoInterceptionBasedOnUrl( | ||
| doNotDoInterception = !(0, utils_1.shouldDoInterceptionBasedOnUrl)( | ||
| windowHandler_1.default.getReferenceOrThrow().windowHandler.location.getOrigin(), | ||
@@ -309,11 +312,10 @@ fetch_1.default.config.apiDomain, | ||
| } | ||
| logger_1.logDebugMessage( | ||
| "responseInterceptor: Value of doNotDoInterception: " + doNotDoInterception | ||
| ); | ||
| (0, | ||
| logger_1.logDebugMessage)("responseInterceptor: Value of doNotDoInterception: " + doNotDoInterception); | ||
| if (doNotDoInterception) { | ||
| logger_1.logDebugMessage("responseInterceptor: Returning without interception"); | ||
| (0, logger_1.logDebugMessage)("responseInterceptor: Returning without interception"); | ||
| // this check means that if you are using axios via inteceptor, then we only do the refresh steps if you are calling your APIs. | ||
| return [2 /*return*/, response]; | ||
| } | ||
| logger_1.logDebugMessage("responseInterceptor: Interception started"); | ||
| (0, logger_1.logDebugMessage)("responseInterceptor: Interception started"); | ||
| processState_1.ProcessState.getInstance().addState( | ||
@@ -324,4 +326,4 @@ processState_1.PROCESS_STATE.CALLING_INTERCEPTION_RESPONSE | ||
| if (!(idRefreshToken !== undefined)) return [3 /*break*/, 3]; | ||
| logger_1.logDebugMessage("responseInterceptor: Setting sIRTFrontend: " + idRefreshToken); | ||
| return [4 /*yield*/, fetch_1.setIdRefreshToken(idRefreshToken, response.status)]; | ||
| (0, logger_1.logDebugMessage)("responseInterceptor: Setting sIRTFrontend: " + idRefreshToken); | ||
| return [4 /*yield*/, (0, fetch_1.setIdRefreshToken)(idRefreshToken, response.status)]; | ||
| case 2: | ||
@@ -333,3 +335,3 @@ _b.sent(); | ||
| return [3 /*break*/, 4]; | ||
| logger_1.logDebugMessage("responseInterceptor: Status code is: " + response.status); | ||
| (0, logger_1.logDebugMessage)("responseInterceptor: Status code is: " + response.status); | ||
| config = response.config; | ||
@@ -354,7 +356,7 @@ return [ | ||
| if (!(antiCsrfToken !== undefined)) return [3 /*break*/, 7]; | ||
| return [4 /*yield*/, fetch_1.getIdRefreshToken(true)]; | ||
| return [4 /*yield*/, (0, fetch_1.getIdRefreshToken)(true)]; | ||
| case 5: | ||
| tok = _b.sent(); | ||
| if (!(tok.status === "EXISTS")) return [3 /*break*/, 7]; | ||
| logger_1.logDebugMessage("responseInterceptor: Setting anti-csrf token"); | ||
| (0, logger_1.logDebugMessage)("responseInterceptor: Setting anti-csrf token"); | ||
| return [4 /*yield*/, fetch_1.AntiCsrfToken.setItem(tok.token, antiCsrfToken)]; | ||
@@ -367,3 +369,3 @@ case 6: | ||
| if (!(frontToken !== undefined)) return [3 /*break*/, 9]; | ||
| logger_1.logDebugMessage("responseInterceptor: Setting sFrontToken: " + frontToken); | ||
| (0, logger_1.logDebugMessage)("responseInterceptor: Setting sFrontToken: " + frontToken); | ||
| return [4 /*yield*/, fetch_1.FrontToken.setItem(frontToken)]; | ||
@@ -380,3 +382,3 @@ case 8: | ||
| if (!_a) return [3 /*break*/, 13]; | ||
| return [4 /*yield*/, fetch_1.getIdRefreshToken(true)]; | ||
| return [4 /*yield*/, (0, fetch_1.getIdRefreshToken)(true)]; | ||
| case 12: | ||
@@ -389,5 +391,4 @@ // we do not call doesSessionExist here cause the user might override that | ||
| if (!_a) return [3 /*break*/, 16]; | ||
| logger_1.logDebugMessage( | ||
| "responseInterceptor: sIRTFrontend doesn't exist, so removing anti-csrf and sFrontToken" | ||
| ); | ||
| (0, | ||
| logger_1.logDebugMessage)("responseInterceptor: sIRTFrontend doesn't exist, so removing anti-csrf and sFrontToken"); | ||
| return [4 /*yield*/, fetch_1.AntiCsrfToken.removeToken()]; | ||
@@ -412,5 +413,5 @@ case 14: | ||
| return function(error) { | ||
| logger_1.logDebugMessage("responseErrorInterceptor: called"); | ||
| (0, logger_1.logDebugMessage)("responseErrorInterceptor: called"); | ||
| if (error.response !== undefined && error.response.status === fetch_1.default.config.sessionExpiredStatusCode) { | ||
| logger_1.logDebugMessage("responseErrorInterceptor: Status code is: " + error.response.status); | ||
| (0, logger_1.logDebugMessage)("responseErrorInterceptor: Status code is: " + error.response.status); | ||
| var config = error.config; | ||
@@ -442,2 +443,4 @@ return AuthHttpRequest.doRequest( | ||
| function AuthHttpRequest() {} | ||
| var _a; | ||
| _a = AuthHttpRequest; | ||
| /** | ||
@@ -462,6 +465,6 @@ * @description sends the actual http request and returns a response if successful/ | ||
| response, | ||
| _a, | ||
| _b, | ||
| idRefreshToken, | ||
| refreshResult, | ||
| _b, | ||
| _c, | ||
| antiCsrfToken, | ||
@@ -473,6 +476,6 @@ tok, | ||
| refreshResult, | ||
| _c, | ||
| _d, | ||
| postRequestIdToken; | ||
| return __generator(this, function(_d) { | ||
| switch (_d.label) { | ||
| return __generator(_a, function(_e) { | ||
| switch (_e.label) { | ||
| case 0: | ||
@@ -482,3 +485,3 @@ if (!fetch_1.default.initCalled) { | ||
| } | ||
| logger_1.logDebugMessage("doRequest: called"); | ||
| (0, logger_1.logDebugMessage)("doRequest: called"); | ||
| doNotDoInterception = false; | ||
@@ -488,3 +491,3 @@ try { | ||
| typeof url === "string" && | ||
| !utils_1.shouldDoInterceptionBasedOnUrl( | ||
| !(0, utils_1.shouldDoInterceptionBasedOnUrl)( | ||
| url, | ||
@@ -497,3 +500,3 @@ fetch_1.default.config.apiDomain, | ||
| if (err.message === "Please provide a valid domain name") { | ||
| logger_1.logDebugMessage( | ||
| (0, logger_1.logDebugMessage)( | ||
| "doRequest: Trying shouldDoInterceptionBasedOnUrl with location.origin" | ||
@@ -503,3 +506,3 @@ ); | ||
| doNotDoInterception = | ||
| !utils_1.shouldDoInterceptionBasedOnUrl( | ||
| !(0, utils_1.shouldDoInterceptionBasedOnUrl)( | ||
| windowHandler_1.default | ||
@@ -515,5 +518,6 @@ .getReferenceOrThrow() | ||
| } | ||
| logger_1.logDebugMessage("doRequest: Value of doNotDoInterception: " + doNotDoInterception); | ||
| (0, | ||
| logger_1.logDebugMessage)("doRequest: Value of doNotDoInterception: " + doNotDoInterception); | ||
| if (!doNotDoInterception) return [3 /*break*/, 2]; | ||
| logger_1.logDebugMessage("doRequest: Returning without interception"); | ||
| (0, logger_1.logDebugMessage)("doRequest: Returning without interception"); | ||
| if (prevError !== undefined) { | ||
@@ -526,15 +530,15 @@ throw prevError; | ||
| case 1: | ||
| return [2 /*return*/, _d.sent()]; | ||
| return [2 /*return*/, _e.sent()]; | ||
| case 2: | ||
| logger_1.logDebugMessage("doRequest: Interception started"); | ||
| _d.label = 3; | ||
| (0, logger_1.logDebugMessage)("doRequest: Interception started"); | ||
| _e.label = 3; | ||
| case 3: | ||
| _d.trys.push([3, , 41, 46]); | ||
| _e.trys.push([3, , 41, 46]); | ||
| returnObj = undefined; | ||
| _d.label = 4; | ||
| _e.label = 4; | ||
| case 4: | ||
| if (!true) return [3 /*break*/, 40]; | ||
| return [4 /*yield*/, fetch_1.getIdRefreshToken(true)]; | ||
| return [4 /*yield*/, (0, fetch_1.getIdRefreshToken)(true)]; | ||
| case 5: | ||
| preRequestIdToken = _d.sent(); | ||
| preRequestIdToken = _e.sent(); | ||
| configWithAntiCsrf = config; | ||
@@ -544,5 +548,5 @@ if (!(preRequestIdToken.status === "EXISTS")) return [3 /*break*/, 7]; | ||
| case 6: | ||
| antiCsrfToken = _d.sent(); | ||
| antiCsrfToken = _e.sent(); | ||
| if (antiCsrfToken !== undefined) { | ||
| logger_1.logDebugMessage("doRequest: Adding anti-csrf token to request"); | ||
| (0, logger_1.logDebugMessage)("doRequest: Adding anti-csrf token to request"); | ||
| configWithAntiCsrf = __assign(__assign({}, configWithAntiCsrf), { | ||
@@ -559,3 +563,3 @@ headers: | ||
| } | ||
| _d.label = 7; | ||
| _e.label = 7; | ||
| case 7: | ||
@@ -566,9 +570,8 @@ if ( | ||
| ) { | ||
| logger_1.logDebugMessage("doRequest: Adding credentials include"); | ||
| (0, logger_1.logDebugMessage)("doRequest: Adding credentials include"); | ||
| configWithAntiCsrf = __assign(__assign({}, configWithAntiCsrf), { withCredentials: true }); | ||
| } | ||
| // adding rid for anti-csrf protection: Anti-csrf via custom header | ||
| logger_1.logDebugMessage( | ||
| "doRequest: Adding rid header: anti-csrf (May get overriden by user's rid)" | ||
| ); | ||
| (0, | ||
| logger_1.logDebugMessage)("doRequest: Adding rid header: anti-csrf (May get overriden by user's rid)"); | ||
| configWithAntiCsrf = __assign(__assign({}, configWithAntiCsrf), { | ||
@@ -582,5 +585,5 @@ headers: | ||
| }); | ||
| _d.label = 8; | ||
| _e.label = 8; | ||
| case 8: | ||
| _d.trys.push([8, 27, , 39]); | ||
| _e.trys.push([8, 27, , 39]); | ||
| localPrevError = prevError; | ||
@@ -591,3 +594,3 @@ localPrevResponse = prevResponse; | ||
| if (localPrevError !== undefined) { | ||
| logger_1.logDebugMessage( | ||
| (0, logger_1.logDebugMessage)( | ||
| "doRequest: Not making call because localPrevError is not undefined" | ||
@@ -598,7 +601,7 @@ ); | ||
| if (localPrevResponse !== undefined) { | ||
| logger_1.logDebugMessage( | ||
| (0, logger_1.logDebugMessage)( | ||
| "doRequest: Not making call because localPrevResponse is not undefined" | ||
| ); | ||
| } else { | ||
| logger_1.logDebugMessage("doRequest: Making user's http call"); | ||
| (0, logger_1.logDebugMessage)("doRequest: Making user's http call"); | ||
| } | ||
@@ -608,43 +611,43 @@ if (!(localPrevResponse === undefined)) return [3 /*break*/, 10]; | ||
| case 9: | ||
| _a = _d.sent(); | ||
| _b = _e.sent(); | ||
| return [3 /*break*/, 11]; | ||
| case 10: | ||
| _a = localPrevResponse; | ||
| _d.label = 11; | ||
| _b = localPrevResponse; | ||
| _e.label = 11; | ||
| case 11: | ||
| response = _a; | ||
| logger_1.logDebugMessage("doRequest: User's http call ended"); | ||
| response = _b; | ||
| (0, logger_1.logDebugMessage)("doRequest: User's http call ended"); | ||
| idRefreshToken = response.headers["id-refresh-token"]; | ||
| if (!(idRefreshToken !== undefined)) return [3 /*break*/, 13]; | ||
| logger_1.logDebugMessage("doRequest: Setting sIRTFrontend: " + idRefreshToken); | ||
| return [4 /*yield*/, fetch_1.setIdRefreshToken(idRefreshToken, response.status)]; | ||
| (0, logger_1.logDebugMessage)("doRequest: Setting sIRTFrontend: " + idRefreshToken); | ||
| return [4 /*yield*/, (0, fetch_1.setIdRefreshToken)(idRefreshToken, response.status)]; | ||
| case 12: | ||
| _d.sent(); | ||
| _d.label = 13; | ||
| _e.sent(); | ||
| _e.label = 13; | ||
| case 13: | ||
| if (!(response.status === fetch_1.default.config.sessionExpiredStatusCode)) | ||
| return [3 /*break*/, 20]; | ||
| logger_1.logDebugMessage("doRequest: Status code is: " + response.status); | ||
| return [4 /*yield*/, fetch_1.onUnauthorisedResponse(preRequestIdToken)]; | ||
| (0, logger_1.logDebugMessage)("doRequest: Status code is: " + response.status); | ||
| return [4 /*yield*/, (0, fetch_1.onUnauthorisedResponse)(preRequestIdToken)]; | ||
| case 14: | ||
| refreshResult = _d.sent(); | ||
| refreshResult = _e.sent(); | ||
| if (!(refreshResult.result !== "RETRY")) return [3 /*break*/, 19]; | ||
| logger_1.logDebugMessage("doRequest: Not retrying original request"); | ||
| (0, logger_1.logDebugMessage)("doRequest: Not retrying original request"); | ||
| if (!refreshResult.error) return [3 /*break*/, 16]; | ||
| return [4 /*yield*/, axiosError_1.createAxiosErrorFromFetchResp(refreshResult.error)]; | ||
| return [4 /*yield*/, (0, axiosError_1.createAxiosErrorFromFetchResp)(refreshResult.error)]; | ||
| case 15: | ||
| _b = _d.sent(); | ||
| _c = _e.sent(); | ||
| return [3 /*break*/, 18]; | ||
| case 16: | ||
| return [4 /*yield*/, axiosError_1.createAxiosErrorFromAxiosResp(response)]; | ||
| return [4 /*yield*/, (0, axiosError_1.createAxiosErrorFromAxiosResp)(response)]; | ||
| case 17: | ||
| _b = _d.sent(); | ||
| _d.label = 18; | ||
| _c = _e.sent(); | ||
| _e.label = 18; | ||
| case 18: | ||
| // Returning refreshResult.error as an Axios Error if we attempted a refresh | ||
| // Returning the response to the original response as an error if we did not attempt refreshing | ||
| returnObj = _b; | ||
| returnObj = _c; | ||
| return [3 /*break*/, 40]; | ||
| case 19: | ||
| logger_1.logDebugMessage("doRequest: Retrying original request"); | ||
| (0, logger_1.logDebugMessage)("doRequest: Retrying original request"); | ||
| return [3 /*break*/, 26]; | ||
@@ -654,19 +657,19 @@ case 20: | ||
| if (!(antiCsrfToken !== undefined)) return [3 /*break*/, 23]; | ||
| return [4 /*yield*/, fetch_1.getIdRefreshToken(true)]; | ||
| return [4 /*yield*/, (0, fetch_1.getIdRefreshToken)(true)]; | ||
| case 21: | ||
| tok = _d.sent(); | ||
| tok = _e.sent(); | ||
| if (!(tok.status === "EXISTS")) return [3 /*break*/, 23]; | ||
| logger_1.logDebugMessage("doRequest: Setting anti-csrf token"); | ||
| (0, logger_1.logDebugMessage)("doRequest: Setting anti-csrf token"); | ||
| return [4 /*yield*/, fetch_1.AntiCsrfToken.setItem(tok.token, antiCsrfToken)]; | ||
| case 22: | ||
| _d.sent(); | ||
| _d.label = 23; | ||
| _e.sent(); | ||
| _e.label = 23; | ||
| case 23: | ||
| frontToken = response.headers["front-token"]; | ||
| if (!(frontToken !== undefined)) return [3 /*break*/, 25]; | ||
| logger_1.logDebugMessage("doRequest: Setting sFrontToken: " + frontToken); | ||
| (0, logger_1.logDebugMessage)("doRequest: Setting sFrontToken: " + frontToken); | ||
| return [4 /*yield*/, fetch_1.FrontToken.setItem(frontToken)]; | ||
| case 24: | ||
| _d.sent(); | ||
| _d.label = 25; | ||
| _e.sent(); | ||
| _e.label = 25; | ||
| case 25: | ||
@@ -677,35 +680,35 @@ return [2 /*return*/, response]; | ||
| case 27: | ||
| err_1 = _d.sent(); | ||
| err_1 = _e.sent(); | ||
| if (!(err_1.response !== undefined)) return [3 /*break*/, 37]; | ||
| idRefreshToken = err_1.response.headers["id-refresh-token"]; | ||
| if (!(idRefreshToken !== undefined)) return [3 /*break*/, 29]; | ||
| logger_1.logDebugMessage("doRequest: Setting sIRTFrontend: " + idRefreshToken); | ||
| return [4 /*yield*/, fetch_1.setIdRefreshToken(idRefreshToken, err_1.response.status)]; | ||
| (0, logger_1.logDebugMessage)("doRequest: Setting sIRTFrontend: " + idRefreshToken); | ||
| return [4 /*yield*/, (0, fetch_1.setIdRefreshToken)(idRefreshToken, err_1.response.status)]; | ||
| case 28: | ||
| _d.sent(); | ||
| _d.label = 29; | ||
| _e.sent(); | ||
| _e.label = 29; | ||
| case 29: | ||
| if (!(err_1.response.status === fetch_1.default.config.sessionExpiredStatusCode)) | ||
| return [3 /*break*/, 35]; | ||
| logger_1.logDebugMessage("doRequest: Status code is: " + err_1.response.status); | ||
| return [4 /*yield*/, fetch_1.onUnauthorisedResponse(preRequestIdToken)]; | ||
| (0, logger_1.logDebugMessage)("doRequest: Status code is: " + err_1.response.status); | ||
| return [4 /*yield*/, (0, fetch_1.onUnauthorisedResponse)(preRequestIdToken)]; | ||
| case 30: | ||
| refreshResult = _d.sent(); | ||
| refreshResult = _e.sent(); | ||
| if (!(refreshResult.result !== "RETRY")) return [3 /*break*/, 34]; | ||
| logger_1.logDebugMessage("doRequest: Not retrying original request"); | ||
| (0, logger_1.logDebugMessage)("doRequest: Not retrying original request"); | ||
| if (!(refreshResult.error !== undefined)) return [3 /*break*/, 32]; | ||
| return [4 /*yield*/, axiosError_1.createAxiosErrorFromFetchResp(refreshResult.error)]; | ||
| return [4 /*yield*/, (0, axiosError_1.createAxiosErrorFromFetchResp)(refreshResult.error)]; | ||
| case 31: | ||
| _c = _d.sent(); | ||
| _d = _e.sent(); | ||
| return [3 /*break*/, 33]; | ||
| case 32: | ||
| _c = err_1; | ||
| _d.label = 33; | ||
| _d = err_1; | ||
| _e.label = 33; | ||
| case 33: | ||
| // Returning refreshResult.error as an Axios Error if we attempted a refresh | ||
| // Returning the original error if we did not attempt refreshing | ||
| returnObj = _c; | ||
| returnObj = _d; | ||
| return [3 /*break*/, 40]; | ||
| case 34: | ||
| logger_1.logDebugMessage("doRequest: Retrying original request"); | ||
| (0, logger_1.logDebugMessage)("doRequest: Retrying original request"); | ||
| return [3 /*break*/, 36]; | ||
@@ -727,16 +730,15 @@ case 35: | ||
| case 41: | ||
| return [4 /*yield*/, fetch_1.getIdRefreshToken(false)]; | ||
| return [4 /*yield*/, (0, fetch_1.getIdRefreshToken)(false)]; | ||
| case 42: | ||
| postRequestIdToken = _d.sent(); | ||
| postRequestIdToken = _e.sent(); | ||
| if (!(postRequestIdToken.status === "NOT_EXISTS")) return [3 /*break*/, 45]; | ||
| logger_1.logDebugMessage( | ||
| "doRequest: sIRTFrontend doesn't exist, so removing anti-csrf and sFrontToken" | ||
| ); | ||
| (0, | ||
| logger_1.logDebugMessage)("doRequest: sIRTFrontend doesn't exist, so removing anti-csrf and sFrontToken"); | ||
| return [4 /*yield*/, fetch_1.AntiCsrfToken.removeToken()]; | ||
| case 43: | ||
| _d.sent(); | ||
| _e.sent(); | ||
| return [4 /*yield*/, fetch_1.FrontToken.removeToken()]; | ||
| case 44: | ||
| _d.sent(); | ||
| _d.label = 45; | ||
| _e.sent(); | ||
| _e.label = 45; | ||
| case 45: | ||
@@ -743,0 +745,0 @@ return [7 /*endfinally*/]; |
@@ -134,2 +134,3 @@ "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.createAxiosErrorFromAxiosResp = exports.createAxiosErrorFromFetchResp = void 0; | ||
| /** | ||
@@ -136,0 +137,0 @@ * From axios package |
| "use strict"; | ||
| function __export(m) { | ||
| for (var p in m) if (!exports.hasOwnProperty(p)) exports[p] = m[p]; | ||
| } | ||
| var __createBinding = | ||
| (this && this.__createBinding) || | ||
| (Object.create | ||
| ? function(o, m, k, k2) { | ||
| if (k2 === undefined) k2 = k; | ||
| var desc = Object.getOwnPropertyDescriptor(m, k); | ||
| if (!desc || ("get" in desc ? !m.__esModule : desc.writable || desc.configurable)) { | ||
| desc = { | ||
| enumerable: true, | ||
| get: function() { | ||
| return m[k]; | ||
| } | ||
| }; | ||
| } | ||
| Object.defineProperty(o, k2, desc); | ||
| } | ||
| : function(o, m, k, k2) { | ||
| if (k2 === undefined) k2 = k; | ||
| o[k2] = m[k]; | ||
| }); | ||
| var __exportStar = | ||
| (this && this.__exportStar) || | ||
| function(m, exports) { | ||
| for (var p in m) | ||
| if (p !== "default" && !Object.prototype.hasOwnProperty.call(exports, p)) __createBinding(exports, m, p); | ||
| }; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
@@ -20,2 +43,2 @@ /* Copyright (c) 2020, VRAI Labs and/or its affiliates. All rights reserved. | ||
| */ | ||
| __export(require(".")); | ||
| __exportStar(require("."), exports); |
@@ -27,3 +27,3 @@ "use strict"; | ||
| function(d, b) { | ||
| for (var p in b) if (b.hasOwnProperty(p)) d[p] = b[p]; | ||
| for (var p in b) if (Object.prototype.hasOwnProperty.call(b, p)) d[p] = b[p]; | ||
| }; | ||
@@ -33,2 +33,4 @@ return extendStatics(d, b); | ||
| return function(d, b) { | ||
| if (typeof b !== "function" && b !== null) | ||
| throw new TypeError("Class extends value " + String(b) + " is not a constructor or null"); | ||
| extendStatics(d, b); | ||
@@ -42,2 +44,3 @@ function __() { | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.STGeneralError = void 0; | ||
| /** | ||
@@ -44,0 +47,0 @@ * This error usually indicates that the API exposed by the backend SDKs responded |
@@ -33,3 +33,3 @@ import { RecipeInterface, NormalisedInputType } from "./types"; | ||
| static init(config: NormalisedInputType, recipeImpl: RecipeInterface): void; | ||
| static doRequest: (httpCall: (config?: RequestInit | undefined) => Promise<Response>, config?: RequestInit | undefined, url?: any) => Promise<Response>; | ||
| static doRequest: (httpCall: (config?: RequestInit) => Promise<Response>, config?: RequestInit, url?: any) => Promise<Response>; | ||
| static attemptRefreshingSession: () => Promise<boolean>; | ||
@@ -36,0 +36,0 @@ } |
@@ -14,7 +14,7 @@ import { InputType, RecipeInterface } from "./types"; | ||
| userContext?: any; | ||
| } | undefined) => Promise<boolean>; | ||
| }) => Promise<boolean>; | ||
| static addAxiosInterceptors: (axiosInstance: any, userContext?: any) => void; | ||
| static signOut: (input?: { | ||
| userContext?: any; | ||
| } | undefined) => Promise<void>; | ||
| }) => Promise<void>; | ||
| } | ||
@@ -27,7 +27,7 @@ export declare let init: typeof AuthHttpRequest.init; | ||
| userContext?: any; | ||
| } | undefined) => Promise<boolean>; | ||
| }) => Promise<boolean>; | ||
| export declare let addAxiosInterceptors: (axiosInstance: any, userContext?: any) => void; | ||
| export declare let signOut: (input?: { | ||
| userContext?: any; | ||
| } | undefined) => Promise<void>; | ||
| }) => Promise<void>; | ||
| export { RecipeInterface, InputType }; |
@@ -148,2 +148,3 @@ "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.signOut = exports.addAxiosInterceptors = exports.doesSessionExist = exports.attemptRefreshingSession = exports.getAccessTokenPayloadSecurely = exports.getUserId = exports.init = void 0; | ||
| var fetch_1 = require("./fetch"); | ||
@@ -160,5 +161,5 @@ var recipeImplementation_1 = require("./recipeImplementation"); | ||
| windowHandler_1.default.init(options.windowHandler); | ||
| var config = utils_1.validateAndNormaliseInputOrThrowError(options); | ||
| var config = (0, utils_1.validateAndNormaliseInputOrThrowError)(options); | ||
| var recipeImpl = new supertokens_js_override_1.default( | ||
| recipeImplementation_1.default({ | ||
| (0, recipeImplementation_1.default)({ | ||
| onHandleEvent: config.onHandleEvent, | ||
@@ -180,3 +181,3 @@ preAPIHook: config.preAPIHook, | ||
| return fetch_1.default.recipeImpl.getUserId({ | ||
| userContext: utils_1.getNormalisedUserContext(input === undefined ? undefined : input.userContext) | ||
| userContext: (0, utils_1.getNormalisedUserContext)(input === undefined ? undefined : input.userContext) | ||
| }); | ||
@@ -186,7 +187,7 @@ }; | ||
| return __awaiter(this, void 0, void 0, function() { | ||
| return __generator(this, function(_a) { | ||
| return __generator(this, function(_b) { | ||
| return [ | ||
| 2 /*return*/, | ||
| fetch_1.default.recipeImpl.getAccessTokenPayloadSecurely({ | ||
| userContext: utils_1.getNormalisedUserContext( | ||
| userContext: (0, utils_1.getNormalisedUserContext)( | ||
| input === undefined ? undefined : input.userContext | ||
@@ -199,6 +200,8 @@ ) | ||
| }; | ||
| var _a; | ||
| _a = AuthHttpRequest; | ||
| AuthHttpRequest.axiosInterceptorQueue = []; | ||
| AuthHttpRequest.attemptRefreshingSession = function() { | ||
| return __awaiter(void 0, void 0, void 0, function() { | ||
| return __generator(this, function(_a) { | ||
| return __generator(_a, function(_b) { | ||
| return [2 /*return*/, fetch_1.default.attemptRefreshingSession()]; | ||
@@ -210,3 +213,3 @@ }); | ||
| return fetch_1.default.recipeImpl.doesSessionExist({ | ||
| userContext: utils_1.getNormalisedUserContext(input === undefined ? undefined : input.userContext) | ||
| userContext: (0, utils_1.getNormalisedUserContext)(input === undefined ? undefined : input.userContext) | ||
| }); | ||
@@ -222,3 +225,3 @@ }; | ||
| axiosInstance: axiosInstance, | ||
| userContext: utils_1.getNormalisedUserContext(userContext) | ||
| userContext: (0, utils_1.getNormalisedUserContext)(userContext) | ||
| }); | ||
@@ -229,3 +232,3 @@ }); | ||
| axiosInstance: axiosInstance, | ||
| userContext: utils_1.getNormalisedUserContext(userContext) | ||
| userContext: (0, utils_1.getNormalisedUserContext)(userContext) | ||
| }); | ||
@@ -236,3 +239,3 @@ } | ||
| return fetch_1.default.recipeImpl.signOut({ | ||
| userContext: utils_1.getNormalisedUserContext(input === undefined ? undefined : input.userContext) | ||
| userContext: (0, utils_1.getNormalisedUserContext)(input === undefined ? undefined : input.userContext) | ||
| }); | ||
@@ -239,0 +242,0 @@ }; |
@@ -17,2 +17,3 @@ "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.logDebugMessage = exports.disableLogging = exports.enableLogging = void 0; | ||
| var version_1 = require("./version"); | ||
@@ -32,10 +33,7 @@ var SUPERTOKENS_DEBUG_NAMESPACE = "com.supertokens"; | ||
| console.log( | ||
| SUPERTOKENS_DEBUG_NAMESPACE + | ||
| ' {t: "' + | ||
| new Date().toISOString() + | ||
| '", message: "' + | ||
| message + | ||
| '", supertokens-website-ver: "' + | ||
| version_1.package_version + | ||
| '"}' | ||
| "" | ||
| .concat(SUPERTOKENS_DEBUG_NAMESPACE, ' {t: "') | ||
| .concat(new Date().toISOString(), '", message: "') | ||
| .concat(message, '", supertokens-website-ver: "') | ||
| .concat(version_1.package_version, '"}') | ||
| ); | ||
@@ -42,0 +40,0 @@ } |
@@ -17,2 +17,3 @@ "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.isAnIpAddress = void 0; | ||
| function isAnIpAddress(ipaddress) { | ||
@@ -19,0 +20,0 @@ return /^(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)$/.test( |
@@ -148,2 +148,3 @@ "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.ProcessState = exports.PROCESS_STATE = void 0; | ||
| var PROCESS_STATE; | ||
@@ -150,0 +151,0 @@ (function(PROCESS_STATE) { |
@@ -156,3 +156,3 @@ "use strict"; | ||
| addFetchInterceptorsAndReturnModifiedFetch: function(input) { | ||
| logger_1.logDebugMessage("addFetchInterceptorsAndReturnModifiedFetch: called"); | ||
| (0, logger_1.logDebugMessage)("addFetchInterceptorsAndReturnModifiedFetch: called"); | ||
| return function(url, config) { | ||
@@ -184,3 +184,3 @@ return __awaiter(this, void 0, void 0, function() { | ||
| addAxiosInterceptors: function(input) { | ||
| logger_1.logDebugMessage("addAxiosInterceptors: called"); | ||
| (0, logger_1.logDebugMessage)("addAxiosInterceptors: called"); | ||
| // we first check if this axiosInstance already has our interceptors. | ||
@@ -190,3 +190,5 @@ var requestInterceptors = input.axiosInstance.interceptors.request; | ||
| if (requestInterceptors.handlers[i].fulfilled === axios_1.interceptorFunctionRequestFulfilled) { | ||
| logger_1.logDebugMessage("addAxiosInterceptors: not adding because already added on this instance"); | ||
| (0, logger_1.logDebugMessage)( | ||
| "addAxiosInterceptors: not adding because already added on this instance" | ||
| ); | ||
| return; | ||
@@ -205,4 +207,4 @@ } | ||
| input.axiosInstance.interceptors.response.use( | ||
| axios_1.responseInterceptor(input.axiosInstance), | ||
| axios_1.responseErrorInterceptor(input.axiosInstance) | ||
| (0, axios_1.responseInterceptor)(input.axiosInstance), | ||
| (0, axios_1.responseErrorInterceptor)(input.axiosInstance) | ||
| ); | ||
@@ -216,3 +218,3 @@ }, | ||
| case 0: | ||
| logger_1.logDebugMessage("getUserId: called"); | ||
| (0, logger_1.logDebugMessage)("getUserId: called"); | ||
| return [4 /*yield*/, fetch_1.FrontToken.getTokenInfo()]; | ||
@@ -224,3 +226,3 @@ case 1: | ||
| } | ||
| logger_1.logDebugMessage("getUserId: returning: " + tokenInfo.uid); | ||
| (0, logger_1.logDebugMessage)("getUserId: returning: " + tokenInfo.uid); | ||
| return [2 /*return*/, tokenInfo.uid]; | ||
@@ -237,3 +239,3 @@ } | ||
| case 0: | ||
| logger_1.logDebugMessage("getAccessTokenPayloadSecurely: called"); | ||
| (0, logger_1.logDebugMessage)("getAccessTokenPayloadSecurely: called"); | ||
| return [4 /*yield*/, fetch_1.FrontToken.getTokenInfo()]; | ||
@@ -246,5 +248,4 @@ case 1: | ||
| if (!(tokenInfo.ate < Date.now())) return [3 /*break*/, 5]; | ||
| logger_1.logDebugMessage( | ||
| "getAccessTokenPayloadSecurely: access token expired. Refreshing session" | ||
| ); | ||
| (0, | ||
| logger_1.logDebugMessage)("getAccessTokenPayloadSecurely: access token expired. Refreshing session"); | ||
| return [4 /*yield*/, fetch_1.default.attemptRefreshingSession()]; | ||
@@ -265,5 +266,4 @@ case 2: | ||
| case 5: | ||
| logger_1.logDebugMessage( | ||
| "getAccessTokenPayloadSecurely: returning: " + JSON.stringify(tokenInfo.up) | ||
| ); | ||
| (0, | ||
| logger_1.logDebugMessage)("getAccessTokenPayloadSecurely: returning: " + JSON.stringify(tokenInfo.up)); | ||
| return [2 /*return*/, tokenInfo.up]; | ||
@@ -279,4 +279,4 @@ } | ||
| case 0: | ||
| logger_1.logDebugMessage("doesSessionExist: called"); | ||
| return [4 /*yield*/, fetch_1.getIdRefreshToken(true)]; | ||
| (0, logger_1.logDebugMessage)("doesSessionExist: called"); | ||
| return [4 /*yield*/, (0, fetch_1.getIdRefreshToken)(true)]; | ||
| case 1: | ||
@@ -294,8 +294,8 @@ return [2 /*return*/, _a.sent().status === "EXISTS"]; | ||
| case 0: | ||
| logger_1.logDebugMessage("signOut: called"); | ||
| (0, logger_1.logDebugMessage)("signOut: called"); | ||
| return [4 /*yield*/, this.doesSessionExist(input)]; | ||
| case 1: | ||
| if (!_a.sent()) { | ||
| logger_1.logDebugMessage("signOut: existing early because session does not exist"); | ||
| logger_1.logDebugMessage("signOut: firing SIGN_OUT event"); | ||
| (0, logger_1.logDebugMessage)("signOut: existing early because session does not exist"); | ||
| (0, logger_1.logDebugMessage)("signOut: firing SIGN_OUT event"); | ||
| recipeImplInput.onHandleEvent({ | ||
@@ -307,3 +307,3 @@ action: "SIGN_OUT", | ||
| } | ||
| logger_1.logDebugMessage("signOut: Calling refresh pre API hook"); | ||
| (0, logger_1.logDebugMessage)("signOut: Calling refresh pre API hook"); | ||
| return [ | ||
@@ -326,8 +326,8 @@ 4 /*yield*/, | ||
| preAPIResult = _a.sent(); | ||
| logger_1.logDebugMessage("signOut: Calling API"); | ||
| (0, logger_1.logDebugMessage)("signOut: Calling API"); | ||
| return [4 /*yield*/, fetch(preAPIResult.url, preAPIResult.requestInit)]; | ||
| case 3: | ||
| resp = _a.sent(); | ||
| logger_1.logDebugMessage("signOut: API ended"); | ||
| logger_1.logDebugMessage("signOut: API responded with status code: " + resp.status); | ||
| (0, logger_1.logDebugMessage)("signOut: API ended"); | ||
| (0, logger_1.logDebugMessage)("signOut: API responded with status code: " + resp.status); | ||
| if (resp.status === recipeImplInput.sessionExpiredStatusCode) { | ||
@@ -356,3 +356,3 @@ // refresh must have already sent session expiry event | ||
| if (responseJson.status === "GENERAL_ERROR") { | ||
| logger_1.logDebugMessage("doRequest: Throwing general error"); | ||
| (0, logger_1.logDebugMessage)("doRequest: Throwing general error"); | ||
| message = | ||
@@ -359,0 +359,0 @@ responseJson.message === undefined |
@@ -134,2 +134,3 @@ "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.defaultCookieHandlerImplementation = void 0; | ||
| function getWindowOrThrow() { | ||
@@ -136,0 +137,0 @@ if (typeof window === "undefined") { |
| "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.CookieHandlerReference = void 0; | ||
| /* Copyright (c) 2022, VRAI Labs and/or its affiliates. All rights reserved. | ||
@@ -4,0 +5,0 @@ * |
@@ -162,2 +162,3 @@ "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.getNormalisedUserContext = exports.shouldDoInterceptionBasedOnUrl = exports.validateAndNormaliseInputOrThrowError = exports.normaliseSessionScopeOrThrowError = exports.normaliseURLPathOrThrowError = exports.normaliseURLDomainOrThrowError = void 0; | ||
| var normalisedURLDomain_1 = require("../normalisedURLDomain"); | ||
@@ -199,3 +200,3 @@ var normalisedURLPath_1 = require("../normalisedURLPath"); | ||
| var noDotNormalised = helper(sessionScope); | ||
| if (noDotNormalised === "localhost" || normalisedURLDomain_1.isAnIpAddress(noDotNormalised)) { | ||
| if (noDotNormalised === "localhost" || (0, normalisedURLDomain_1.isAnIpAddress)(noDotNormalised)) { | ||
| return noDotNormalised; | ||
@@ -270,3 +271,3 @@ } | ||
| if (options.enableDebugLogs !== undefined && options.enableDebugLogs) { | ||
| logger_1.enableLogging(); | ||
| (0, logger_1.enableLogging)(); | ||
| } | ||
@@ -289,3 +290,3 @@ return { | ||
| function shouldDoInterceptionBasedOnUrl(toCheckUrl, apiDomain, cookieDomain) { | ||
| logger_1.logDebugMessage( | ||
| (0, logger_1.logDebugMessage)( | ||
| "shouldDoInterceptionBasedOnUrl: toCheckUrl: " + | ||
@@ -292,0 +293,0 @@ toCheckUrl + |
@@ -134,2 +134,3 @@ "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.defaultWindowHandlerImplementation = void 0; | ||
| function getWindowOrThrow() { | ||
@@ -136,0 +137,0 @@ if (typeof window === "undefined") { |
| "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.WindowHandlerReference = void 0; | ||
| /* Copyright (c) 2022, VRAI Labs and/or its affiliates. All rights reserved. | ||
@@ -4,0 +5,0 @@ * |
@@ -1,2 +0,2 @@ | ||
| export declare const package_version = "13.0.1"; | ||
| export declare const package_version = "13.0.2"; | ||
| export declare const supported_fdi: string[]; |
| "use strict"; | ||
| Object.defineProperty(exports, "__esModule", { value: true }); | ||
| exports.supported_fdi = exports.package_version = void 0; | ||
| /* Copyright (c) 2020, VRAI Labs and/or its affiliates. All rights reserved. | ||
@@ -17,3 +18,3 @@ * | ||
| */ | ||
| exports.package_version = "13.0.1"; | ||
| exports.package_version = "13.0.2"; | ||
| exports.supported_fdi = ["1.8", "1.9", "1.10", "1.11", "1.12", "1.13", "1.14"]; |
| { | ||
| "name": "supertokens-website", | ||
| "version": "13.0.1", | ||
| "version": "13.0.2", | ||
| "description": "frontend sdk for website to be used for auth solution.", | ||
@@ -27,7 +27,7 @@ "main": "index.js", | ||
| "size-limit": "^6.0.3", | ||
| "typedoc": "^0.22.5", | ||
| "typescript": "3.8.3", | ||
| "webpack": "4.35.0", | ||
| "webpack-cli": "3.3.5", | ||
| "webpack-dev-server": "3.7.2" | ||
| "typedoc": "^0.22.17", | ||
| "typescript": "^4.7.3", | ||
| "webpack": "^5.74.0", | ||
| "webpack-cli": "^4.10.0", | ||
| "webpack-dev-server": "^4.9.3" | ||
| }, | ||
@@ -38,3 +38,3 @@ "scripts": { | ||
| "build-check": "cd lib && npx tsc -p tsconfig.json --noEmit && cd ../test/ && npx tsc -p tsconfig.json --noEmit", | ||
| "build": "cd lib && rm -rf build && npx tsc -p tsconfig.json && cd ../ && webpack -p && cd test && npx tsc -p tsconfig.json", | ||
| "build": "cd lib && rm -rf build && npx tsc -p tsconfig.json && cd ../ && npm run pack && cd test && npx tsc -p tsconfig.json", | ||
| "pretty": "cd lib && npx prettier --write --config .prettierrc \"ts/**/*.ts\" \"build/**/*.js\" \"../test/**/*.js\"", | ||
@@ -44,3 +44,3 @@ "build-pretty": "npm run build && npm run pretty", | ||
| "set-up-hooks": "cp hooks/pre-commit.sh .git/hooks/pre-commit && chmod +x .git/hooks/pre-commit", | ||
| "pack": "webpack -p", | ||
| "pack": "webpack --mode=production", | ||
| "build-docs": "rm -rf ./docs && npx typedoc --out ./docs --tsconfig ./lib/tsconfig.json ./lib/ts/index.ts", | ||
@@ -47,0 +47,0 @@ "size": "size-limit" |
148
README.md
@@ -0,147 +1,3 @@ | ||
| To use SuperTokens with your own custom UI refer to our plain Javascript SDK [supertokens-web-js](https://github.com/supertokens/supertokens-web-js) | ||
|  | ||
| # SuperTokens Javascript Frontend SDK | ||
| <a href="https://supertokens.io/discord"> | ||
| <img src="https://img.shields.io/discord/603466164219281420.svg?logo=discord" | ||
| alt="chat on Discord"></a> | ||
| SuperTokens adds **secure login and session management** to your apps. This is the Javascript Frontend SDK for SuperTokens. [More SDKs are available](https://github.com/supertokens) for frontend and backend e.g. Node.js, Go, Python, React.js, React Native, Vanilla JS, etc. | ||
| 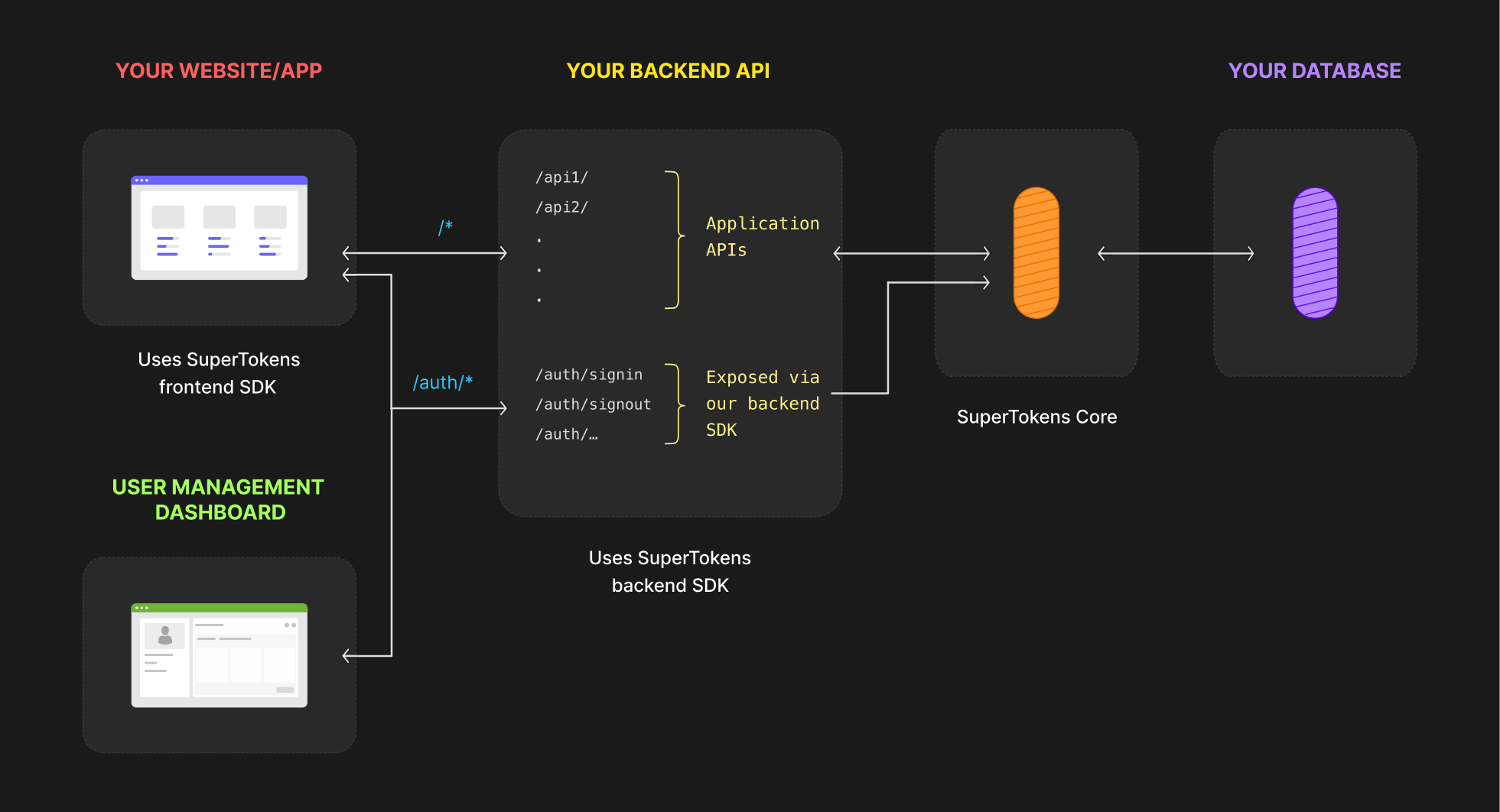 | ||
| SuperTokens architecture is optimized to add secure authentication for your users without compromising on user and developer experience | ||
| Learn more at [supertokens.com](https://supertokens.com) | ||
| ## How to install | ||
| Using npm | ||
| ``` | ||
| npm i -s supertokens-website | ||
| ``` | ||
| OR simply add the following script tag to your HTML pages | ||
| ```html | ||
| <script src="https://cdn.jsdelivr.net/gh/supertokens/supertokens-website/bundle/bundle.js"></script> | ||
| ``` | ||
| ## How to use | ||
| 1. Initialize SuperTokens in your frontend | ||
| ```js | ||
| supertokens.init({ | ||
| apiDomain: "<URL to your auth backend>" | ||
| }); | ||
| // To be called at least once before any http request is made to any of your APIs that require authentication. | ||
| // Now your app will maintain secure SuperTokens sessions for your users | ||
| ``` | ||
| 2. Make sure your backend has the needed auth functionalities | ||
| > You can use one of the SuperTokens backend SDKs for this. | ||
| > Backend SDKs are available for | ||
| > * [Node.js backend](https://github.com/supertokens/supertokens-node) | ||
| > * [Golang backend](https://github.com/supertokens/supertokens-golang) | ||
| > * [Python backend](https://github.com/supertokens/supertokens-python) | ||
| Now that's the basic setup. But you might want to do some of the following things | ||
| ### Checking if a session exists | ||
| ```js | ||
| await supertokens.doesSessionExist(); | ||
| ``` | ||
| ### Reading the userId | ||
| ```js | ||
| let userId = await supertokens.getUserId(); | ||
| ``` | ||
| ### Reading the access token payload | ||
| ```js | ||
| let payload = await supertokens.getAccessTokenPayloadSecurely(); | ||
| ``` | ||
| ### Sign out | ||
| The signOut method simply revokes the session on the frontend and backend. | ||
| ```js | ||
| await supertokens.signOut(); | ||
| ``` | ||
| ### Sending requests with `fetch` | ||
| The `init` function call automatically adds interceptors to fetch. So there is nothing else that needs to be done. | ||
| ```js | ||
| supertokens.init({ | ||
| apiDomain: "https://api.example.com" | ||
| }); | ||
| async function doAPICalls() { | ||
| try { | ||
| // make API call as usual | ||
| let fetchConfig = { ... }; | ||
| let response = await fetch("/someAPI", fetchConfig); | ||
| // handle response | ||
| if (response.status !== 200) { | ||
| throw response; | ||
| } | ||
| let data = await response.json(); | ||
| let someField = data.someField; | ||
| // ... | ||
| } catch (err) { | ||
| if (err.status === 401) { | ||
| // redirect user to login | ||
| } else { | ||
| // handle error | ||
| } | ||
| } | ||
| } | ||
| ``` | ||
| ### Sending requests with axios | ||
| ```js | ||
| supertokens.addAxiosInterceptors(axios); // To be called on each axios instances being imported | ||
| supertokens.init({ | ||
| apiDomain: "https://api.example.com" | ||
| }); | ||
| async function doAPICalls() { | ||
| try { | ||
| let postData = { ... }; | ||
| let response = await axios({url: "someAPI", method: "post", data: postData }); | ||
| let data = await response.data; | ||
| let someField = data.someField; | ||
| } catch (err) { | ||
| if (err.response !== undefined && err.response.status === 401) { | ||
| // redirect user to login | ||
| } else { | ||
| // handle error | ||
| } | ||
| } | ||
| } | ||
| ``` | ||
| ## Documentation | ||
| To see documentation, please click [here](https://supertokens.com/docs/community/introduction). | ||
| ## Contributing | ||
| Please refer to the [CONTRIBUTING.md](https://github.com/supertokens/supertokens-website/blob/master/CONTRIBUTING.md) file in this repo. | ||
| ## Contact us | ||
| For any queries, or support requests, please email us at team@supertokens.com, or join our [Discord](supertokens.com/discord) server. | ||
| ## Authors | ||
| Created with :heart: by the folks at SuperTokens.com | ||
| For any queries, or support requests, please email us at team@supertokens.com, or join our [Discord](https://supertokens.com/discord) server. |
@@ -20,2 +20,12 @@ /* Copyright (c) 2020, VRAI Labs and/or its affiliates. All rights reserved. | ||
| exports.__esModule = true; | ||
| __export(require("../../lib/build/error")); | ||
| let d = require("../../lib/build/error"); | ||
| if (d.default !== undefined) { | ||
| __export(d); | ||
| } else { | ||
| __export({ | ||
| default: d, | ||
| ...d, | ||
| }); | ||
| } |
Sorry, the diff of this file is too big to display
New alerts
License Policy Violation
LicenseThis package is not allowed per your license policy. Review the package's license to ensure compliance.
Found 1 instance in 1 package
Fixed alerts
License Policy Violation
LicenseThis package is not allowed per your license policy. Review the package's license to ensure compliance.
Found 1 instance in 1 package
Improved metrics
- Lines of code
- increased by0.1%
5018
Worsened metrics
- Total package byte prevSize
- decreased by-0.8%
256570
- Number of lines in readme file
- decreased by-97.3%
4