
Security News
Deno 2.2 Improves Dependency Management and Expands Node.js Compatibility
Deno 2.2 enhances Node.js compatibility, improves dependency management, adds OpenTelemetry support, and expands linting and task automation for developers.
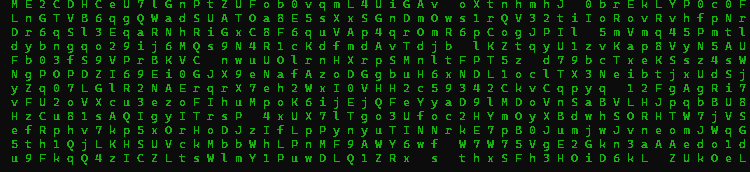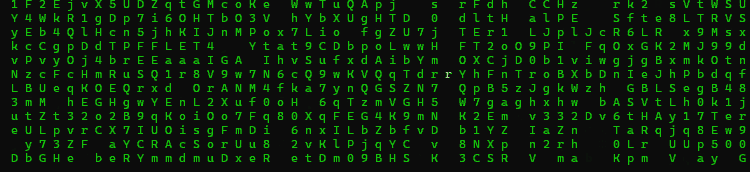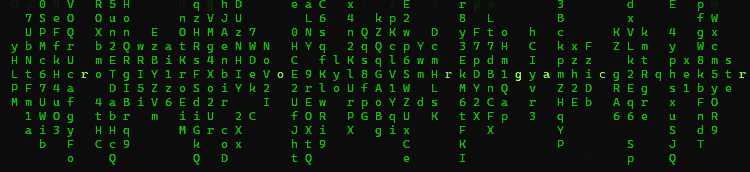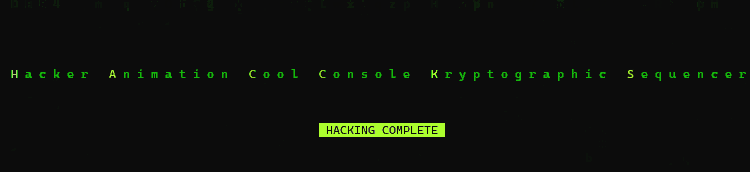
a digital rain code password decrypting effect library for Python, useful to visually represent character by-character secrets retrieval attacks. For example a binary search in a blind database injection.
inspired by the "cryptographic sequencer" from the Batman Arkham video games series and the phone number tracking effect from the Matrix movie intro
from haccks import Haccks
password = "T0psyKr33t!"
h = Haccks(len(password))
# guess 1 character by second
for i, c in enumerate(password):
h.setCharacter(i, c)
time.sleep(1)
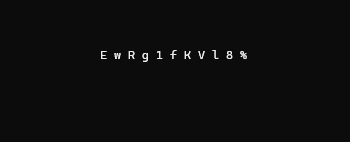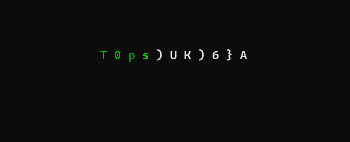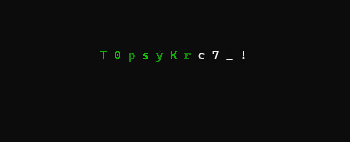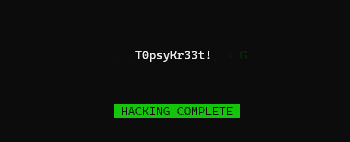
from haccks import Haccks
h = Haccks(24, refreshDelay=1,
primaryColor="purple", secondaryColor="fuchsia")
h.setCharacter(0, 'A')
h.setCharacter(23, 'Z')
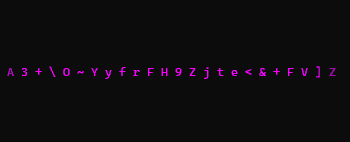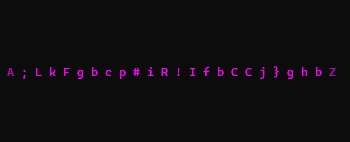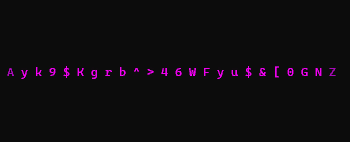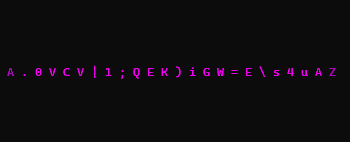
from haccks import Haccks
alphabet = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!"#$%&()*+<>?'
e = Haccks(40, alphabet, refreshDelay=0.01,
primaryColor="yellow2", secondaryColor="aqua")
# cool animation: guess one random potential character by millisecond
lal = [random.sample(list(alphabet), len(alphabet)) for _ in range(40)]
while True:
r = random.randint(0, len(lal)-1)
if len(lal[r]) > 1:
e.removeCharsFromAlphabet(r, lal[r].pop())
time.sleep(0.001)
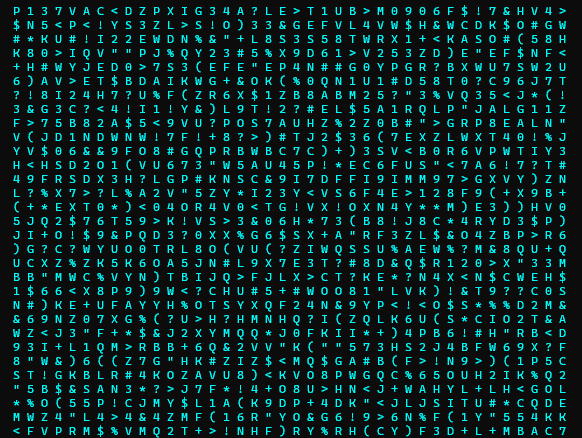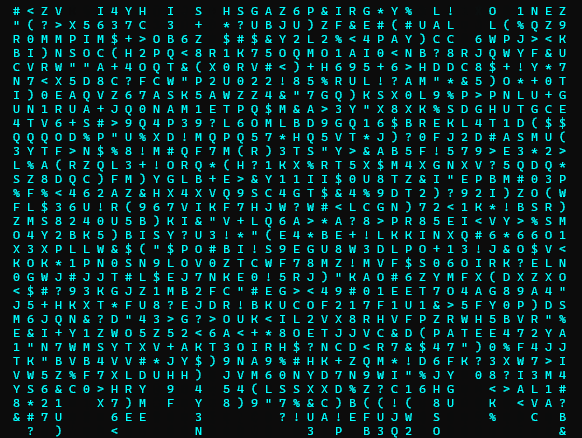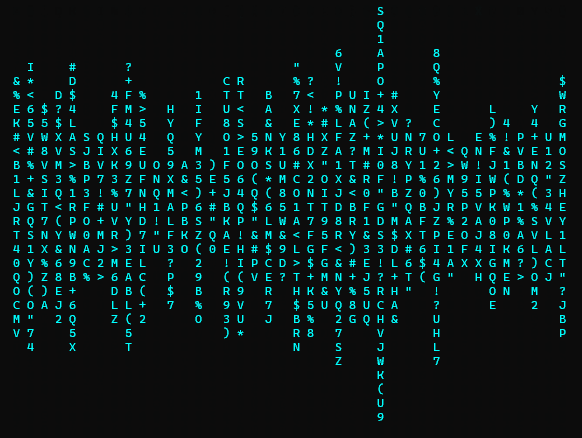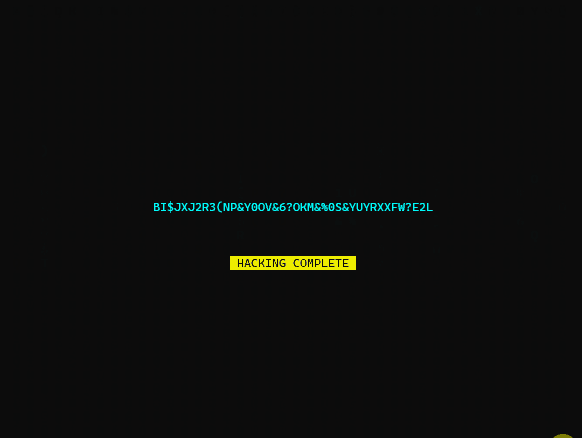
from haccks import Haccks
from blessed import Terminal
def myCustomEnding(term: Terminal):
paddH = term.height // 2 - 2
print(term.clear)
print(term.move_yx(paddH, 0) + term.chocolate1 +
term.center("It’s now safe to turn off"))
print(term.move_yx(paddH+1, 0) + term.chocolate1 +
term.center("your computer"))
time.sleep(5)
h = Haccks(12, customEndingMethod=myCustomEnding)
...
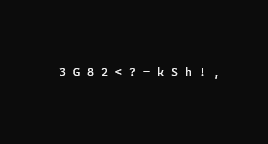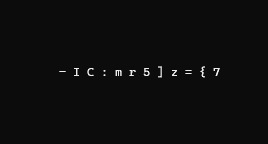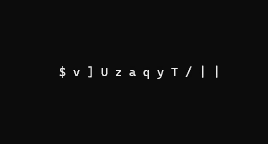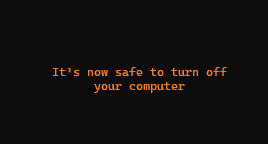
Please tell me if it's not clear
(it makes sense in my mind, but that's because i'm a genius :P)
# constructor of effect. immediatly displays fullscreen on terminal.
# ex: you know you have a 7 chars long secret to guess that can only be hexadecimal chars:
# Haccks(7, '0123456789abcdef')
h = Haccks(
numChars: int, # number of "cracking" characters to display
alphabet: str = "", # possible chars shown.
refreshDelay: float = 0.01, # sleep time between each refresh of the effect
# check blessed.readthedocs.io/en/latest/colors.html for available colors
primaryColor: str = "green", # color of the found characters
secondaryColor: str = "normal", # color of all other characters
customEndingMethod: Callable[[blessed.Terminal], None] = None # custom method called at end
)
# set a character as "decoded", won't change and will appear in PrimaryColor
# ex: you found with a certitude that the second char of your secret is 'c':
# h.setCharacter(1, 'c')
h.setCharacter(
position: int # index of the character
character: str: # char to set
)
# remove possible characters from the alphabet of an index
# ex: you know that the third char of your secret cannot b 'Z':
# h.removeCharsFromAlphabet(2, 'Z')
h.removeCharsFromAlphabet(
position: int, # index of the character
characters: str # chars to exclude from alphabet
)
some errors and automatic managements
blazingly fast (printing characters one by one? nobody would try that...)
multiplatform (thanks to the blessed library)
customisable (colors, custom ending)
stoppable (type q to quit)
window resize aware
multiprocessing instead of threading ? (very small performance gain)FAQs
Hacker Animation Cool Console Kryptographic Sequencer (haccks)
We found that haccks demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Deno 2.2 enhances Node.js compatibility, improves dependency management, adds OpenTelemetry support, and expands linting and task automation for developers.

Security News
React's CRA deprecation announcement sparked community criticism over framework recommendations, leading to quick updates acknowledging build tools like Vite as valid alternatives.

Security News
Ransomware payment rates hit an all-time low in 2024 as law enforcement crackdowns, stronger defenses, and shifting policies make attacks riskier and less profitable.