Shell access
Severity
Medium
Short Description
This module accesses the system shell. Accessing the system shell increases the risk of executing arbitrary code.
Suggestion
Packages should avoid accessing the shell which can reduce portability, and make it easier for malicious shell access to be introduced.
Information
The Shell Access alert in Socket monitors your project's dependencies for any interactions with the system shell.
Shell access refers to the capability of a program or dependency to interact directly with the system's command-line interface (shell). This allows the execution of shell commands and operations on the operating system, enabling tasks like file manipulation, process control, and system configuration. While shell access can provide powerful functionality, it also increases the risk of executing arbitrary or malicious code, potentially compromising the security and stability of the system.
Recommended actions
If one of your dependencies is flagged with the Shell Access alert, here are a few steps you can take to ensure the package is safe to use:
- Review Functionality: Check if the shell access is essential for the dependency's functionality by consulting its documentation.
- Remove Unnecessary Access: If the shell access isn't required, consider removing or replacing the dependency.
- Update Dependencies: Ensure all dependencies are updated to their latest versions, which may have reduced or secured shell access.
- Review Shell Commands: Examine the shell commands being executed to ensure they are legitimate and secure.
- Validate Permissions: Ensure that the dependencies have the minimum necessary permissions to perform their tasks, adhering to the principle of least privilege.
Examples
Here's an example where Socket has flagged a package for Shell Access due to the use of the child_process module:
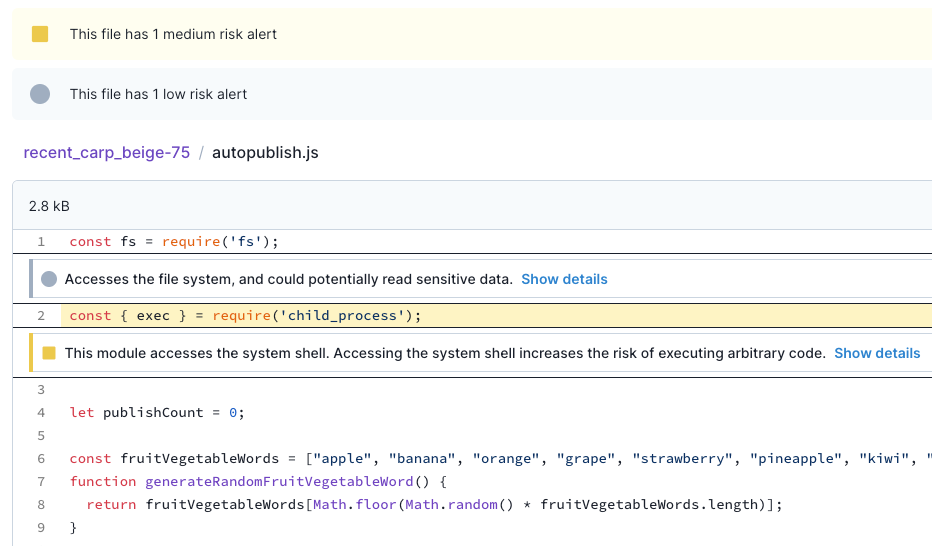
Detection Method
Socket detects shell access by scanning a dependency’s code for the use of modules or functions that enable interaction with the system shell, such as the child_process module in Node.js. By identifying imports or invocations of these shell-related APIs (e.g., exec, spawn), Socket flags packages that have the capability to execute shell commands, thereby increasing the risk of arbitrary or malicious code execution.
Additional resources
Node.js Child Processes: Everything you need to know - FreeCodeCamp
OWASP - The Principle of Least Privilege: Outlines the principle of least privilege and how it applies to limiting access and capabilities in applications.
MITRE ATT&CK: A globally-accessible knowledge base of adversary tactics and techniques based on real-world observations.
The subprocess Module: Wrapping Programs With Python - Guide to the Python subprocess module