
Security News
The Changelog Podcast: Practical Steps to Stay Safe on npm
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.


Sarah Gooding
July 26, 2024
Imagine a popular open-source project called cool-library that includes a dependency directly from a Git repository in its package.json:
{
"dependencies": {
"useful-library": "git+https://github.com/legit-developer/useful-library.git"
}
}Initially, the useful-library repository was maintained by a reputable developer, and everything seemed fine. Over time, the project gained traction and was widely adopted by developers around the world.
One day, the maintainer of useful-library decided to hand over the project to another developer due to personal commitments. The new maintainer, unfortunately, had malicious intentions. He subtly modified the useful-library codebase to include a backdoor that would exfiltrate sensitive data from any project using it. These changes were pushed to the Git repository without raising any alarms.
Since cool-library had a direct Git dependency, anyone installing or updating it would automatically fetch the latest version of useful-library with the embedded backdoor. Developers and organizations would unknowingly pull the compromised code into their projects, leading to data breaches and other security incidents.
A week after the malicious changes were made, a security researcher noticed unusual network traffic originating from applications using cool-library. Upon investigation, the backdoor in useful-library was discovered, and an advisory was issued. The open-source community quickly responded by removing the compromised dependency, but the damage had already been done. Sensitive information from numerous projects had been leaked, and the trust in cool-library was significantly eroded.
This hypothetical scenario illustrates the risks associated with using Git dependencies in open-source projects. Without thorough vetting and constant monitoring, a seemingly benign update can lead to severe security breaches.
Specific examples of Git dependency attacks in the wild are less commonly documented compared to other types of supply chain attacks. However, the concept remains important to understand due to the potential risks.
In 2018, the npm security team foiled a plot to steal cryptocurrency when the electron-native-notify npm package was compromised. An attacker gained access to the maintainer's GitHub account and injected malicious code into the electron-native-notify repository. The malicious code included a post-install script that collected and sent sensitive information to a remote server. The compromised version was published to npm, and projects depending on this package unknowingly included the malicious code.
This particular attack utilized a strategy where the maintainer published a legitimately useful package to npm (electron-native-notify) and then waited until it was in use by the intended target. Once the package was more widely adopted, it was updated to include a malicious payload.
Although this example does not directly reference a Git dependency in a package.json, it illustrates the risks associated with dependencies hosted on GitHub. If a project were to pull dependencies directly from a Git repository, there is always the risk of accounts getting compromised.
While there are some legitimate use cases for referencing Git dependencies, and not every package that does this is malicious, it’s important to understand the security risks associated with them:
Apart from the direct security risks, there are also a number of other stability, consistency, and compliance concerns that can result from using Git dependencies:
1. Lack of Version Control:
⠀2. Stability and Reliability Issues:
⠀3. Dependency Drift:
⠀4. Difficulty in Auditing:
There are legitimate reasons why a Git dependency might be found in an open source package, so it’s important to be aware of some of the most common ones. It’s often used as a way to give access to unreleased features or bug fixes, incorporate forks and custom modifications, test an experimental feature branch, host private or proprietary code, or include as part of a monorepo workflow.
While Git dependencies can introduce certain risks, such as the potential for supply chain attacks, there are many legitimate reasons for their use. Developers should be aware of the trade-offs and ensure they implement proper security measures to mitigate the risks.
Socket identifies Git dependencies as a high severity alert, because of the risks it introduces to supply chains.There are two related alerts: Git dependency and GitHub dependency, which is specific to that platform.
The Git/GitHub Dependency alerts are triggered when a package includes dependencies that are sourced directly from a Git repository or GitHub URL, rather than from a versioned package registry like npm, PyPI, or Maven Central. These dependencies are not immutable can be used to inject untrusted code or reduce the likelihood of a reproducible install.
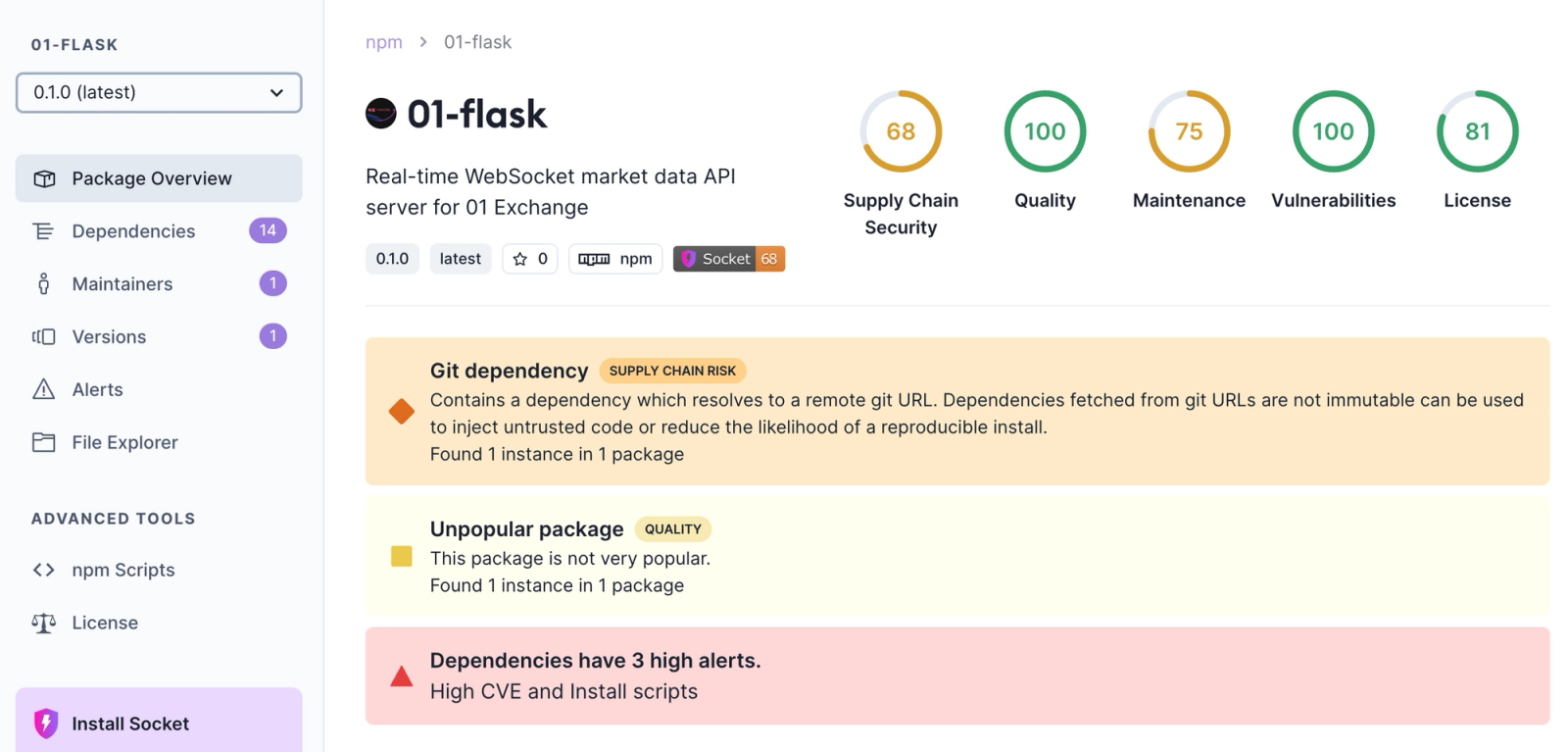
Clicking on the alert links to the package.json file where the GitHub repository is listed as a dependency:
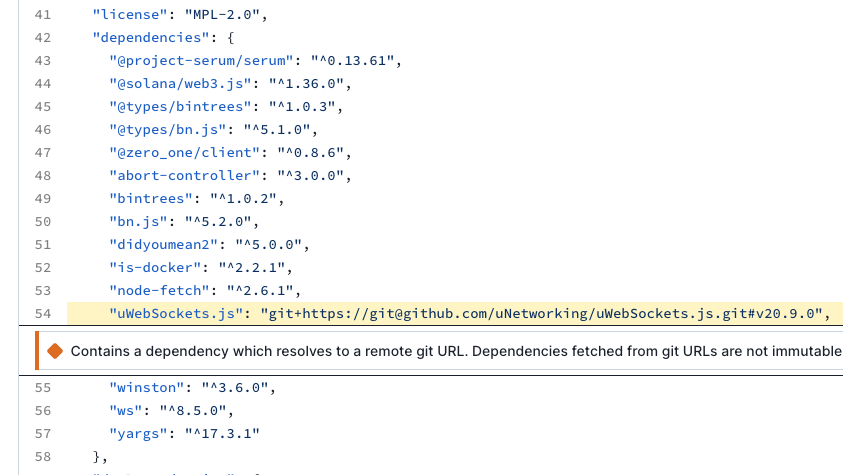
If you are using Socket and one of your packages triggers this alert or you see it on a dependency update, it’s a good idea to investigate further. In the most ideal world, you would be using only versioned packages.
Many Socket users elect to configure their Security Policies to Warn for the Git Dependency alert, but you can also make it more a more serious concern and Block these dependencies. By understanding and mitigating the risks associated with Git dependencies, you can better ensure the security and stability of your applications.
Socket’s alerts make it easier to monitor packages with Git dependencies. If you are not yet using Socket, you can install the GitHub app for free in two clicks. This will give you a complete overview of your usage of packages with Git dependencies and will scan for 70+ other supply chain risks.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.

Security News
Experts push back on new claims about AI-driven ransomware, warning that hype and sponsored research are distorting how the threat is understood.

Security News
Ruby's creator Matz assumes control of RubyGems and Bundler repositories while former maintainers agree to step back and transfer all rights to end the dispute.