In the wake of the backdoored XZ utils package, the world is once again acutely aware of the ever-present danger of supply chain attacks and how ill-equipped most organizations are to handle incidents where the threat actor has legitimate access to the codebase. The staggering impact of this breach cannot be overstated, as XZ utils is used in nearly every major Linux distribution, which could have given unauthorized individuals access to critical systems on a global scale.
The European Union Agency for Cybersecurity’s (ENISA) latest report ranks supply chain compromise of software dependencies as the top threat with the highest impact for the next half a decade. In the Foresight Cybersecurity Threats for 2030, a study with rigorous methodology that leverages insight from experts, ENISA has outlined a comprehensive analysis of emerging cybersecurity threats projected for the next six years.
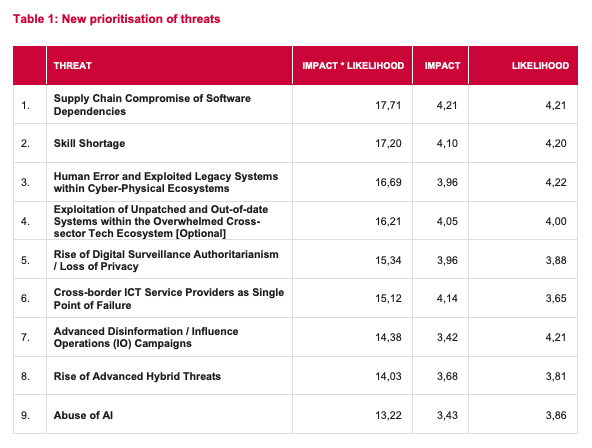
Combine the continued threat of software supply chain compromise with a cybersecurity skill shortage, the second ranked threat, and the ability to effectively mitigate cyberattacks becomes increasingly difficult. This has been the case for years in the open source ecosystem, where so much trust is placed in dependencies and their maintainers, who are often stretched thin across multiple projects and vulnerable to burnout. Ultimately, this forces maintainers to prioritize immediate fixes over long-term security improvements.
Getting “Unreasonably Lucky” Isn’t a Strategy for Securing Open Source Software#
The backdoored XZ utils incident makes it exceedingly clear that the industry is not prepared for the next big supply chain attack. All the stars had to align for Microsoft developer Andres Freund to notice what was happening here.

“There are more coincidences that are even less interesting,” Freund commented on Mastodon. “But even the above should make it clear how unlikely it was that I found this thing.
“Just to be clear: I didn't mean that I didn't do good - I did. I mean that we got unreasonably lucky here, and that we can't just bank on that going forward.”
The supply chain attack wasn’t discovered by CISA or the FBI or any kind of authority established to protect against such attacks. It was accidentally discovered by an engineer following up on sshd processes that appeared to be using a lot of CPU.
“This is the nearest of near-misses,” Google engineer and OpenSSH maintainer Damien Miller commented on the incident.
“Anyone who suggests this was any kind of success is a fool. No system caught this, it was luck and individual heroics. That's not acceptable when unauthorized access to ~every server on the internet is on the table. We need to find a way to do better.”
This particular attack was thwarted because it came across the wrong desk. The level of mastery required to identify these threats is often scarce. We can’t depend solely on humans to catch everything - we need better tools. Socket has been focused on solving this problem of securing dependencies that come from open source package registries and unfortunately these types of supply chain attacks are far more common than most people realize. They occur on a spectrum of sophistication from small scale targeting to more widespread disruption attempts.
The suspected state actor responsible for the backdoor in XZ utils may be more mindful in the next attack of how performance degradation can tip people off to the vulnerability. This attempt was foiled by sheer luck but it begs the question of how many more have gone unnoticed. The problem of overworked open source maintainers is nothing new and they remain high value targets.
“This won't be the last sophisticated and methodical OSS supply-chain attack,” Miller commented on Mastodon. “The actor(s) behind xz are probably already learning their lessons ahead of their next attempt. Indeed, xz might not be the only attack they had in progress.
“The next one is going to be more carefully operated and harder to spot. How are we going to stop it?”





