
Research
Security News
Malicious npm Package Targets Solana Developers and Hijacks Funds
A malicious npm package targets Solana developers, rerouting funds in 2% of transactions to a hardcoded address.
github.com/joxit/docker-registry-ui
This project aims to provide a simple and complete user interface for your private docker registry. You can customize the interface with various options. The major option is SINGLE_REGISTRY which allows you to disable the dynamic selection of docker registeries (same behavior as the old static tag).
You may need the migration guide from 1.x to 2.x or the 1.x readme
This web user interface uses Riot the react-like user interface micro-library and riot-mui components.
If you like my work and want to support it, don't hesitate to sponsor me.
latest: image with the latest release of Docker Registry UI based on nginx:alpinelatest-debian: image with the latest release of Docker Registry UI based on nginx:debianmain, master: image with the beta version of Docker Registry UI based on nginx:alpinemain-debian, master-debian: image with the beta version of Docker Registry UI based on nginx:debian2: image with the latest release of Docker Registry UI v2 (includes latest minor and patch version)2.x: image with the latest release of Docker Registry UI v2.x (includes latest patch version)2.x.y: image with the specific release of Docker Registry UI v2.x.y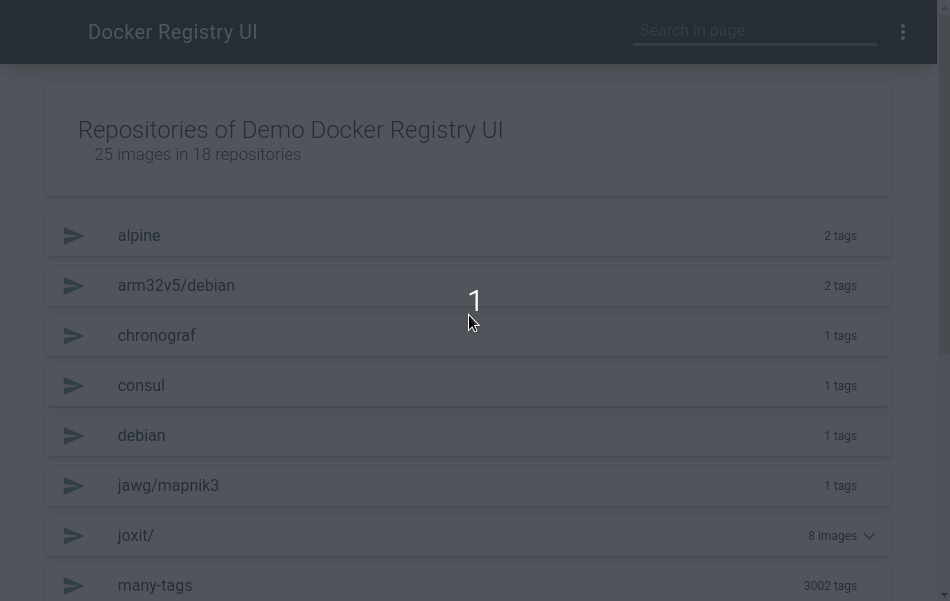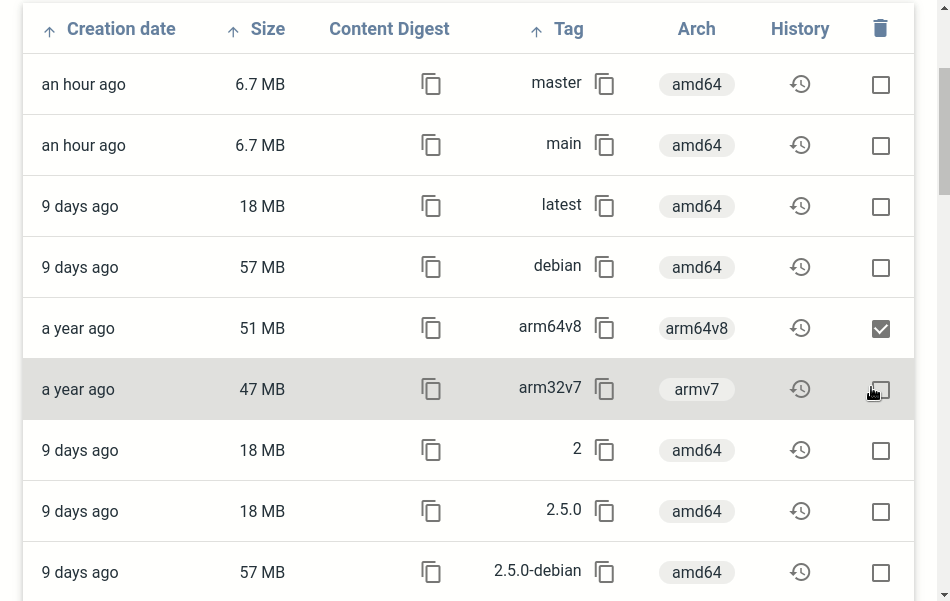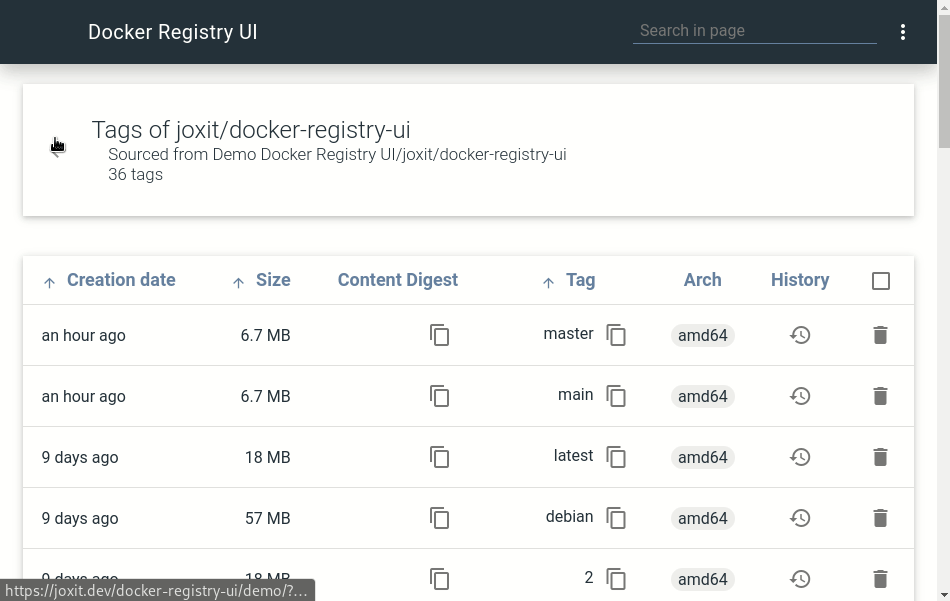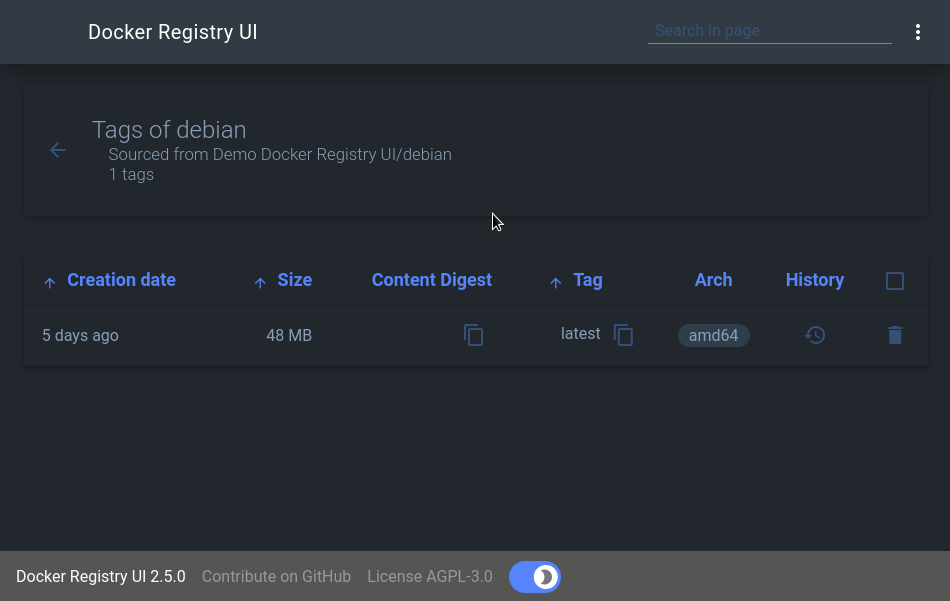
ALT + Click on the indeterminate checkbox (see #80 and #81). Since 1.2.1Shift + Click on the first tag then Shift + Click on the second tag (see #287). Since 2.4.0SINGLE_REGISTRY=false.
url (e.g. https://joxit.dev/docker-registry-ui/demo?url=https://registry.example.com). If you need credentials on your private registry, you must set the Access-Control-Allow-Origin to https://joxit.dev.CRTL + F or F3. When the search bar is already focused, the shortcut will fallback to the default behavior (see #213). Since 2.1.0sha256:).Checkout all options in Available options section.
SINGLE_REGISTRY=false and SINGLE_REGISTRY=true options ?
SINGLE_REGISTRY is set to false, a menu appears on the interface allowing you to dynamically change docker registry URLs.docker images ?
Host is set to $http_host ?
NGINX_PROXY_PASS_URL or configure a nginx/apache/haproxy in front of your registry that returns 200 on each OPTIONS requests. (see #104, #204, #207, #214, #266).name and its manifest (it's a sha of the content). So when you delete a tag, this will delete all tags of this image with the same SHA/manifest.library/* images ?
pagination number invalid ?
REGISTRY_CATALOG_MAXENTRIES with your max value and check the issue #306.NGINX_PROXY_PASS_URL, my registry server has been recreated and the UI cannot connect with the message [error] 176#176: *2 connect() failed (111: Connection refused) while connecting to upstream, what can I do?
NGINX_RESOLVER and set to 127.0.0.11.Need more informations ? Try my examples or open an issue.
You can run the container with the unprivileged user nginx, see the discussion #224.
Some env options are available for use this interface for only one server (when SINGLE_REGISTRY=true).
REGISTRY_URL: The default url of your docker registry. You may need CORS configuration on your registry. This is usually the domain name or IP of your registry reachable by your computer (e.g http://registry.example.com). (default: derived from the hostname of your UI).REGISTRY_TITLE: Set a custom title for your user interface. (default: value derived from REGISTRY_URL) (see #28 and #32). Since 0.3.4PULL_URL: Set a custom url when you copy the docker pull command (see #71). (default: value derived from REGISTRY_URL). Since 1.1.0DELETE_IMAGES: Set if we can delete images from the UI. (default: false)SHOW_CONTENT_DIGEST: Show/Hide content digest in docker tag list (see #126 and #131). (default: false). Since 1.4.9CATALOG_ELEMENTS_LIMIT: Limit the number of elements in the catalog page (see #39, #127, #132) and #306. (default: 1000). Since 1.4.9SINGLE_REGISTRY: Remove the menu that show the dialogs to add, remove and change the endpoint of your docker registry. (default: false). Since 2.0.0NGINX_PROXY_PASS_URL: Update the default Nginx configuration and set the proxy_pass to your backend docker registry (this avoid CORS configuration). This is usually the name of your registry container in the form http://registry:5000. Since 2.0.0NGINX_PROXY_HEADER_*: Update the default Nginx configuration and set custom headers for your backend docker registry via environment variable and file (/etc/nginx/.env). Only when NGINX_PROXY_PASS_URL is used (see #89). Since 1.2.3NGINX_PROXY_PASS_HEADER_*: Update the default Nginx configuration and forward custom headers to your backend docker registry via environment variable and file (/etc/nginx/.env). Only when NGINX_PROXY_PASS_URL is used (see #206). Since 2.1.0NGINX_LISTEN_PORT: Listen on a port other than 80, you can also change the default user and set to nginx --user nginx (see #224 and #234). (default: 80 when the user is root, 8080 otherwise). Since 2.2.0NGINX_RESOLVER: Add resolver directive to the nginx configuration for dynamic dns resolving. The value when you are using a docker network is 127.0.0.11, you can set a custom DNS server too with a valid time. This is not needed when you are using kubernetes. (see #333 and #339). (default: ``). Since 2.5.5DEFAULT_REGISTRIES: List of comma separated registry URLs (e.g http://registry.example.com,http://registry:5000), available only when SINGLE_REGISTRY=false (see #219). (default: ). Since 2.1.0READ_ONLY_REGISTRIES: Deactivate dialog for remove and add new registries, available only when SINGLE_REGISTRY=false (see #219). (default: false). Since 2.1.0SHOW_CATALOG_NB_TAGS: Show number of tags per images on catalog page and hide images with 0 tags. This will produce + nb images requests, not recommended on large registries (see #161 and #239). (default: false). Since 2.2.0HISTORY_CUSTOM_LABELS: Expose custom labels in history page, custom labels will be processed like maintainer label (see #160 and #240). Since 2.2.0USE_CONTROL_CACHE_HEADER: Use Control-Cache header and set to no-store, no-cache. This will avoid some issues on multi-arch images (see #260 and #265). This option requires registry configuration: Access-Control-Allow-Headers with Cache-Control. (default: false). Since 2.3.0THEME: Chose your default theme, could be dark, light or auto (see #283). When auto is selected, you will have a switch to manually change from light to dark and vice-versa (see #291). (default: auto). Since 2.4.0THEME_*: See table in Theme options section (see #283). Since 2.4.0TAGLIST_ORDER: Set the default order for the taglist page, could be num-asc;alpha-asc, num-desc;alpha-asc, num-asc;alpha-desc, num-desc;alpha-desc, alpha-asc;num-asc, alpha-asc;num-desc, alpha-desc;num-asc or alpha-desc;num-desc (see #307). (default: alpha-asc;num-desc). Since 2.5.0CATALOG_DEFAULT_EXPANDED: Expand by default all repositories in catalog (see #302). (default: false). Since 2.5.0CATALOG_MIN_BRANCHES: Set the minimum repository/namespace to expand (e.g. joxit/docker-registry-ui joxit/ is the repository/namespace). Can be 0 to disable branching. (see #319). (default: 1). Since 2.5.0CATALOG_MAX_BRANCHES: Set the maximum repository/namespace to expand (e.g. joxit/docker-registry-ui joxit/ is the repository/namespace). Can be 0 to disable branching. (see #319). (default: 1). Since 2.5.0TAGLIST_PAGE_SIZE: Set the number of tags to display in one page. (default: 100). Since 2.5.0REGISTRY_SECURED: By default, the UI will check on every requests if your registry is secured or not (you will see 401 responses in your console). Set to true if your registry uses Basic Authentication and divide by two the number of call to your registry. (default false). Since 2.5.0SHOW_TAG_HISTORY: Whether to show the tag history feature or not. Allows to simplify the user interface by hiding it form the tag list if set to false. (default: true).
There are some examples with docker-compose and docker-registry-ui as proxy here or docker-registry-ui as standalone here.This featureswas added to version 2.4.0. See more about this in #283.
| Environment variable | light theme value | dark theme value |
|---|---|---|
THEME_PRIMARY_TEXT | #25313b | #98a8bd |
THEME_NEUTRAL_TEXT | #777777 | #6d7fab |
THEME_BACKGROUND | #ffffff | #22272e |
THEME_HOVER_BACKGROUND | #eeeeee | #343a4b |
THEME_ACCENT_TEXT | #5f7796 | #5c88ff |
THEME_HEADER_TEXT | #ffffff | #ffffff |
THEME_HEADER_ACCENT_TEXT | #7b9ac2 | #7ea1ff |
THEME_HEADER_BACKGROUND | #25313b | #333a45 |
THEME_FOOTER_TEXT | #ffffff | #ffffff |
THEME_FOOTER_NEUTRAL_TEXT | #adbacd | #98afcf |
THEME_FOOTER_BACKGROUND | #344251 | #344251 |
Here is a simple usage of Docker Registry UI with Docker Registry Server using docker-compose. This example should work for most of your use case and your UI will be on the same domain as you registry.
version: '3.8'
services:
registry-ui:
image: joxit/docker-registry-ui:main
restart: always
ports:
- 80:80
environment:
- SINGLE_REGISTRY=true
- REGISTRY_TITLE=Docker Registry UI
- DELETE_IMAGES=true
- SHOW_CONTENT_DIGEST=true
- NGINX_PROXY_PASS_URL=http://registry-server:5000
- SHOW_CATALOG_NB_TAGS=true
- CATALOG_MIN_BRANCHES=1
- CATALOG_MAX_BRANCHES=1
- TAGLIST_PAGE_SIZE=100
- REGISTRY_SECURED=false
- CATALOG_ELEMENTS_LIMIT=1000
container_name: registry-ui
registry-server:
image: registry:2.8.2
restart: always
environment:
REGISTRY_HTTP_HEADERS_Access-Control-Allow-Origin: '[http://registry.example.com]'
REGISTRY_HTTP_HEADERS_Access-Control-Allow-Methods: '[HEAD,GET,OPTIONS,DELETE]'
REGISTRY_HTTP_HEADERS_Access-Control-Allow-Credentials: '[true]'
REGISTRY_HTTP_HEADERS_Access-Control-Allow-Headers: '[Authorization,Accept,Cache-Control]'
REGISTRY_HTTP_HEADERS_Access-Control-Expose-Headers: '[Docker-Content-Digest]'
REGISTRY_STORAGE_DELETE_ENABLED: 'true'
volumes:
- ./registry/data:/var/lib/registry
container_name: registry-server
Your server should be configured to accept CORS.
If your docker registry does not need credentials, you will need to send this HEADER:
Access-Control-Allow-Origin: ['*']
If your docker registry need credentials, you will need to send these HEADERS (you must add the protocol http/https and the port when not default 80/443):
http:
headers:
Access-Control-Allow-Origin: ['http://registry.example.com']
Access-Control-Allow-Credentials: [true]
Access-Control-Allow-Headers: ['Authorization', 'Accept', 'Cache-Control']
Access-Control-Allow-Methods: ['HEAD', 'GET', 'OPTIONS'] # Optional
An alternative for CORS issues is a plugin on your browser, more info here (thank you xmontero).
:warning: If you are using credential and still having issues, please read the the line about preflight requests and the bug in docker registry server in the FAQ before posting any issues.
For deleting images, you need to activate the delete feature in the UI with DELETE_IMAGES=true and in your registry:
storage:
delete:
enabled: true
And you need to add these HEADERS:
http:
headers:
Access-Control-Allow-Methods: ['HEAD', 'GET', 'OPTIONS', 'DELETE']
Access-Control-Allow-Headers: ['Authorization', 'Accept', 'Cache-Control']
Access-Control-Expose-Headers: ['Docker-Content-Digest']
Example of docker registry configuration file:
version: 0.1
log:
fields:
service: registry
storage:
delete:
enabled: true
cache:
blobdescriptor: inmemory
filesystem:
rootdirectory: /var/lib/registry
http:
addr: :5000
headers:
X-Content-Type-Options: [nosniff]
Access-Control-Allow-Origin: ['http://127.0.0.1:8000']
Access-Control-Allow-Methods: ['HEAD', 'GET', 'OPTIONS', 'DELETE']
Access-Control-Allow-Headers: ['Authorization', 'Accept', 'Cache-Control']
Access-Control-Max-Age: [1728000]
Access-Control-Allow-Credentials: [true]
Access-Control-Expose-Headers: ['Docker-Content-Digest']
auth:
htpasswd:
realm: basic-realm
path: /etc/docker/registry/htpasswd
If you do not want to install the docker-registry-ui on your server, you may check out the Electron standalone application (not updated).
FAQs
Unknown package
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Security News
A malicious npm package targets Solana developers, rerouting funds in 2% of transactions to a hardcoded address.

Security News
Research
Socket researchers have discovered malicious npm packages targeting crypto developers, stealing credentials and wallet data using spyware delivered through typosquats of popular cryptographic libraries.

Security News
Socket's package search now displays weekly downloads for npm packages, helping developers quickly assess popularity and make more informed decisions.