
Research
Security News
Malicious npm Packages Inject SSH Backdoors via Typosquatted Libraries
Socket’s threat research team has detected six malicious npm packages typosquatting popular libraries to insert SSH backdoors.
@a_kawashiro/jendeley
Advanced tools
`jendeley` is a JSON-based PDF paper organizing software. - `jendeley` is JSON-based. You can see and edit your database easily. - `jendeley` is working locally. Your important database is owned only by you. Not cloud. - `jendeley` is browser based. You c
jendeley is a JSON-based PDF paper organizing software.
jendeley is JSON-based. You can see and edit your database easily.jendeley is working locally. Your important database is owned only by you. Not cloud.jendeley is browser based. You can run it anywhere node.js runs.npm install @a_kawashiro/jendeley -g
jendeley scan --papers_dir <YOUR PDFs DIR>
jendeley launch --db <YOUR PDFs DIR>/jendeley_db.json
Then you can see a screen like this!
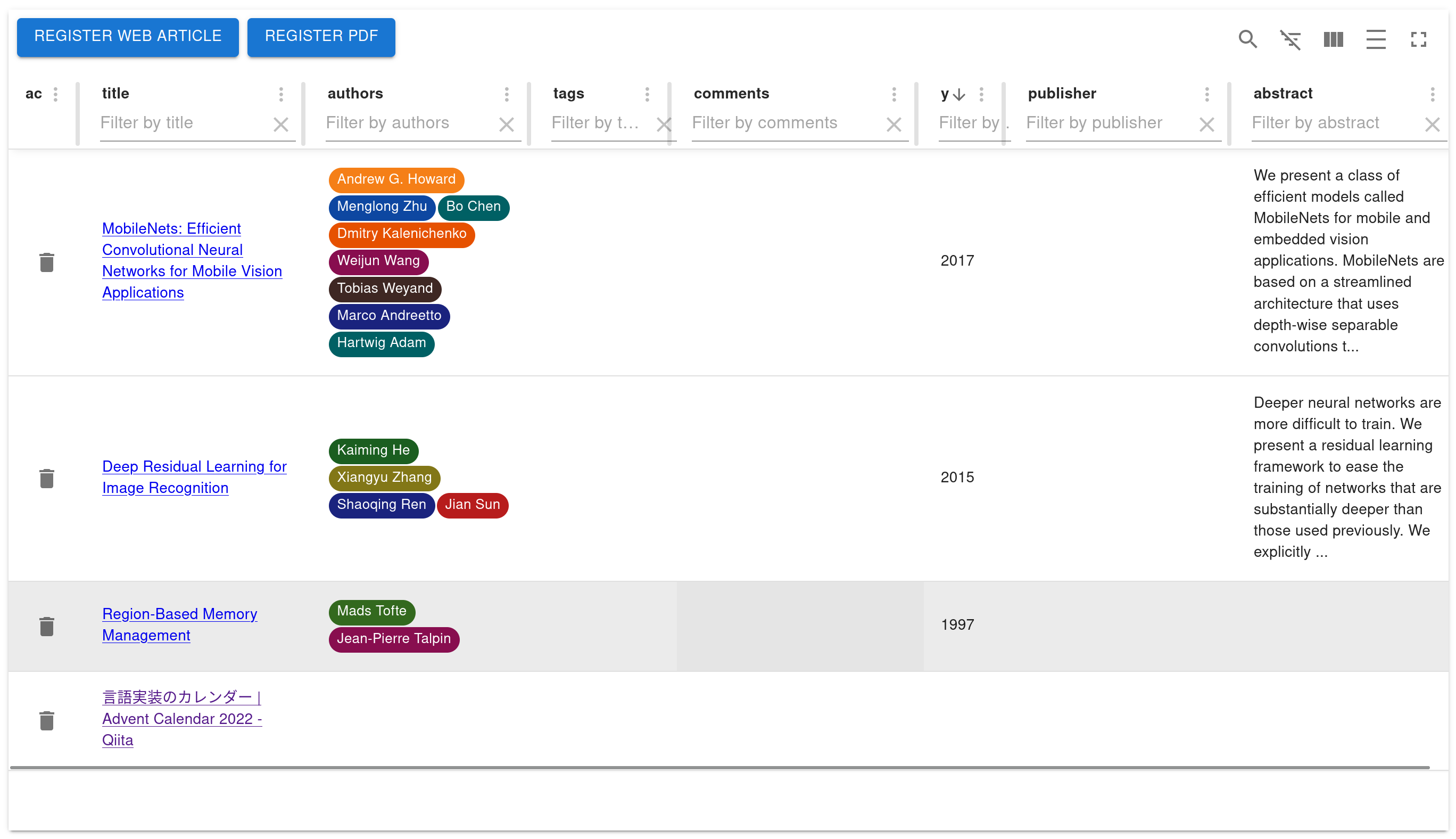
npm install @a_kawashiro/jendeley -g
This command emits the database to <YOUR PDFs DIR>/jendeley_db.json. When jendeley failed to scan some PDFs, it emit a shellscript edit_and_run.sh. Please read the next subsection and rename files using it.
jendeley scan --papers_dir <YOUR PDFs DIR>
jendeley use filename also to find the document ID (e.g. DOI or ISBN)). jendeley recognizes the filename other than surrounded by [ and ] as the title of the file. So I recommend you to name file such way. For example,
Register Allocation and Optimal Spill Code Scheduling in Software Pipelined Loops Using 0-1 Integer Linear Programming Formulation.pdf
RustHorn CHC-based Verification for Rust Programs [matushita].pdf
[ and ].jendeley is heavily dependent on DOI or ISBN to find title, authors and published year of PDFs. So jendeley try to find DOI of given PDFs in many ways. But sometimes all of them fails to find DOI. In that case, you can specify DOI of PDF manually using filename.
[jendeley doi <DOI replaced all delimiters with underscore>]. For example, cyclone [jendeley doi 10_1145_512529_512563].pdf.[jendeley isbn <ISBN>]. For example, hoge [jendeley isbn 9781467330763].pdf.jendeley launch --db <YOUR PDFs DIR>/jendeley_db.json
You can use --port option to change the default port.
jendeley automaticallyWhen you are using Linux, you can launch jendeley automatically using systemd. Please make ~/.config/systemd/user/jendeley.service with the following contents, run systemctl --user enable jendeley && systemctl --user start jendeley and access http://localhost:5000. You can check log with journalctl --user -f -u jendeley.service.
[Unit]
Description=jendeley JSON based document organization software
[Service]
ExecStart=jendeley launch --db <FILL PATH TO THE YOUR DATABASE JSON FILE> --no_browser
[Install]
WantedBy=default.target
Because jendeley is fully JSON-based, you can check the contents of the
database easily. For example, you can use jq command to list up all titles in
your database with the following command.
> cat jendeley_db.json | jq '.' | head
{
"jendeley_meta": {
"idType": "meta",
"version": "0.0.17"
},
"doi_10.1145/1122445.1122456": {
"path": "/A Comprehensive Survey of Neural Architecture Search.pdf",
"idType": "doi",
"tags": [],
"comments": "",
FAQs
`jendeley` is a JSON-based document organizing software. - `jendeley` is JSON-based. You can see and edit your database quickly. - `jendeley` works locally. Your important database is owned only by you. No cloud. - `jendeley` is browser-based. You can run
The npm package @a_kawashiro/jendeley receives a total of 6 weekly downloads. As such, @a_kawashiro/jendeley popularity was classified as not popular.
We found that @a_kawashiro/jendeley demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 0 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Security News
Socket’s threat research team has detected six malicious npm packages typosquatting popular libraries to insert SSH backdoors.

Security News
MITRE's 2024 CWE Top 25 highlights critical software vulnerabilities like XSS, SQL Injection, and CSRF, reflecting shifts due to a refined ranking methodology.

Security News
In this segment of the Risky Business podcast, Feross Aboukhadijeh and Patrick Gray discuss the challenges of tracking malware discovered in open source softare.