
Security News
New Python Packaging Proposal Aims to Solve Phantom Dependency Problem with SBOMs
PEP 770 proposes adding SBOM support to Python packages to improve transparency and catch hidden non-Python dependencies that security tools often miss.
daedalus-fugazi-webclient
Advanced tools
web based terminal application for executing local and remote commands
A web based terminal application for executing local and remote commands.
The latest version of the terminal can be found here: http://fugazi.io.
Here's a short introduction video:
Documentation can be found here: https://fugazi-io.github.io.
You can contact us here: https://gitter.im/fugazi-io/Lobby.
Fugazi isn't a regular terminal, it won't execute the commands which you are used to.
In order to execute commands you need to load modules into the client, these modules will define the
commands which can be executed.
The client comes with a some built-in commands, and here's a short example of what you can do with it:
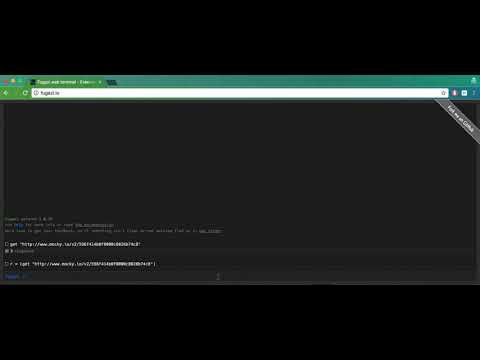
In the fugazi terminal try to execute:
get "https://jsonplaceholder.typicode.com/posts/1"
This command will make an http GET request to that url and output the response.
(you can use other urls of course, as long as they support CORS).
If you only want to get the data from the response you can do so like this:
r = (get "https://jsonplaceholder.typicode.com/posts/1")
extract data from $r
Here we used a variable to hold the response and then extracted the data part from it, but you can do it in one line using nested commands:
extract data from (get "https://jsonplaceholder.typicode.com/posts/1")
The only problem left though is that the return value is a string and not a map.
This happens because the response doesn't have json content type.
It's easy to go around it though:
r = (get "https://jsonplaceholder.typicode.com/posts/1")
d = (extract data from $r)
json parse $d
Or, in one line:
json parse (extract data from (get "https://jsonplaceholder.typicode.com/posts/1"))
The client requires no servers, other than hosting the static files (scripts, styles, etc).
To run locally install the npm package:
npm install @fugazi/webclient
Then build the scripts:
npm run transpile
After the compilation ended, serve the files:
npm run serve
That's it, you have fugazi locally served, open http://localhost:3330/index.hml in your browser.
If you want to develop with/for fugazi then you better clone this repo.
Here's how to run it locally:
$ npm install$ npm run dev (read the dev npm script in package.json for more information)TAB to open the suggestions boxESC to close the suggestion boxTAB can be used to switch to selection mode and back to input modeENTER to select a suggestionCTRL + R then start typing and ENTER to select, ESC to close)There's a new documentation site here: https://fugazi-io.github.io, this is the old version:
Use the issues for any bug, request, question.
Or you can find us in our gitter
We're looking for more help, if you're interested find us in this gmail.com address: terminal.fugazi.io
FAQs
web based terminal application for executing local and remote commands
The npm package daedalus-fugazi-webclient receives a total of 8 weekly downloads. As such, daedalus-fugazi-webclient popularity was classified as not popular.
We found that daedalus-fugazi-webclient demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
PEP 770 proposes adding SBOM support to Python packages to improve transparency and catch hidden non-Python dependencies that security tools often miss.

Security News
Socket CEO Feross Aboukhadijeh discusses open source security challenges, including zero-day attacks and supply chain risks, on the Cyber Security Council podcast.

Security News
Research
Socket researchers uncover how threat actors weaponize Out-of-Band Application Security Testing (OAST) techniques across the npm, PyPI, and RubyGems ecosystems to exfiltrate sensitive data.