
Research
Security News
Malicious npm Packages Inject SSH Backdoors via Typosquatted Libraries
Socket’s threat research team has detected six malicious npm packages typosquatting popular libraries to insert SSH backdoors.
discord-verify
Advanced tools
A library for verifying the authenticity of requests coming from the Discord Interactions API
This package is used to efficiently verify Discord HTTP interactions.
The following graphs show the real world metrics of Truth or Dare running discord-interactions version 3.2.0 on the left and discord-verify version 1.0.0 on the right. At the time, Truth or Dare was in 640,000 servers and running on a machine with an Intel Xeon E5-2630 CPU and 16GB of RAM. It averaged 55% CPU usage and 450ms event loop lag. After switching to discord-verify, the CPU usage dropped to 5% and the event loop lag dropped to 10ms.
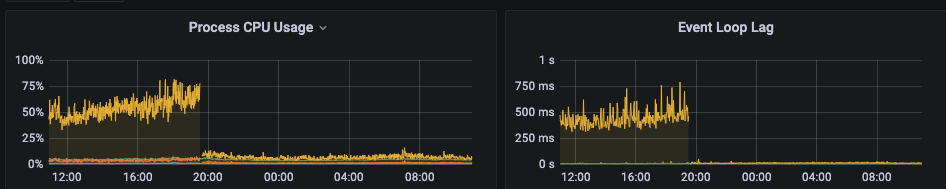
By using native WebCrypto instead of tweetnacl discord-verify achieves significantly better performance compared to discord-interactions.
npm install discord-verify
import { isValidRequest } from "discord-verify";
const isValid = await isValidRequest(request, publicKey);
import { isValidRequest } from "discord-verify/node";
const isValid = await isValidRequest(request, publicKey);
If you want to verify requests from frameworks such as Express or Fastify that have their own request classes, you can import the verify function and pass raw values to it.
import { verify } from "discord-verify/node";
async function handleRequest(
req: FastifyRequest<{
Body: APIInteraction;
Headers: {
"x-signature-ed25519": string;
"x-signature-timestamp": string;
};
}>,
res: FastifyReply
) {
const signature = req.headers["x-signature-ed25519"];
const timestamp = req.headers["x-signature-timestamp"];
const rawBody = JSON.stringify(req.body);
const isValid = await verify(
rawBody,
signature,
timestamp,
this.client.publicKey,
crypto.webcrypto.subtle
);
if (!isValid) {
return res.code(401).send("Invalid signature");
}
}
If you are using Node 17 or lower, you need to make some changes:
+ import { verify, PlatformAlgorithm } from "discord-verify/node";
async function handleRequest(
req: FastifyRequest<{
Body: APIInteraction;
Headers: {
"x-signature-ed25519": string;
"x-signature-timestamp": string;
};
}>,
res: FastifyReply
) {
const signature = req.headers["x-signature-ed25519"];
const timestamp = req.headers["x-signature-timestamp"];
const rawBody = JSON.stringify(req.body);
const isValid = await verify(
rawBody,
signature,
timestamp,
this.client.publicKey,
crypto.webcrypto.subtle,
+ PlatformAlgorithm.OldNode
);
if (!isValid) {
return res.code(401).send("Invalid signature");
}
}
If you see a runtime DOMException about the the name, applying these changes should fix it.
isValidRequest takes an optional third argument to specify the algorithm to use. This can be a string or object containing name and namedCurve. For convenience, discord-verify exports PlatformAlgorithm that contains values used by common platforms. You can use it like this:
import { isValidRequest, PlatformAlgorithm } from "discord-verify";
const isValid = await isValidRequest(
request,
publicKey,
PlatformAlgorithm.Vercel
);
The following platforms are currently supported:
FAQs
A library for verifying the authenticity of requests coming from the Discord Interactions API
The npm package discord-verify receives a total of 2,416 weekly downloads. As such, discord-verify popularity was classified as popular.
We found that discord-verify demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Security News
Socket’s threat research team has detected six malicious npm packages typosquatting popular libraries to insert SSH backdoors.

Security News
MITRE's 2024 CWE Top 25 highlights critical software vulnerabilities like XSS, SQL Injection, and CSRF, reflecting shifts due to a refined ranking methodology.

Security News
In this segment of the Risky Business podcast, Feross Aboukhadijeh and Patrick Gray discuss the challenges of tracking malware discovered in open source softare.