
Security News
Python Overtakes JavaScript as Top Programming Language on GitHub
Python becomes GitHub's top language in 2024, driven by AI and data science projects, while AI-powered security tools are gaining adoption.
eslint-plugin-no-secrets
Advanced tools
An eslint rule that searches for potential secrets/keys in code
An eslint rule that searches for potential secrets/keys in code and JSON files.
npm i -D eslint-plugin-no-secrets
eslint.config.js
import noSecrets from "eslint-plugin-no-secrets";
export default [
{
files: ["**/*.js"],
plugins: {
"no-secrets": noSecrets,
},
rules: {
"no-secrets/no-secrets": "error",
},
},
];
.eslintrc
{
"plugins": ["no-secrets"],
"rules": {
"no-secrets/no-secrets": "error"
}
}
//Found a string with entropy 4.3 : "ZWVTjPQSdhwRgl204Hc51YCsritMIzn8B=/p9UyeX7xu6KkAGqfm3FJ+oObLDNEva"
const A_SECRET =
"ZWVTjPQSdhwRgl204Hc51YCsritMIzn8B=/p9UyeX7xu6KkAGqfm3FJ+oObLDNEva";
//Found a string that matches "AWS API Key" : "AKIAIUWUUQQN3GNUA88V"
const AWS_TOKEN = "AKIAIUWUUQQN3GNUA88V";
To include JSON files, install eslint-plugin-jsonc
npm install --save-dev eslint-plugin-jsonc
Then in your .eslint configuration file, extend the jsonc base config
{
"extends": ["plugin:jsonc/base"]
}
eslint.config.js
import noSecrets from "eslint-plugin-no-secrets";
import jsoncExtend from "eslint-plugin-jsonc";
export default [
...jsoncExtend.configs["flat/recommended-with-jsonc"],
{
languageOptions: { ecmaVersion: 6 },
plugins: {
"no-secrets": noSecret,
},
rules: {
"no-secrets/no-secrets": "error",
},
},
];
Decrease the tolerance for entropy
{
"plugins": ["no-secrets"],
"rules": {
"no-secrets/no-secrets": ["error", { "tolerance": 3.2 }]
}
}
Add additional patterns to check for certain token formats.
Standard patterns can be found here
{
"plugins": ["no-secrets"],
"rules": {
"no-secrets/no-secrets": [
"error",
{
"additionalRegexes": {
"Basic Auth": "Authorization: Basic [A-Za-z0-9+/=]*"
}
}
]
}
}
// Set of potential base64 characters
// eslint-disable-next-line no-secrets/no-secrets
const BASE64_CHARS =
"ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=";
This will tell future maintainers of the codebase that this suspicious string isn't an oversight
ignoreContent to ignore certain content{
"plugins": ["no-secrets"],
"rules": {
"no-secrets/no-secrets": ["error", { "ignoreContent": "^ABCD" }]
}
}
ignoreIdentifiers to ignore certain variable/property names{
"plugins": ["no-secrets"],
"rules": {
"no-secrets/no-secrets": [
"error",
{ "ignoreIdentifiers": ["BASE64_CHARS"] }
]
}
}
additionalDelimiters to further split up tokensTokens will always be split up by whitespace within a string. However, sometimes words that are delimited by something else (e.g. dashes, periods, camelcase words). You can use additionalDelimiters to handle these cases.
For example, if you want to split words up by the character . and by camelcase, you could use this configuration:
{
"plugins": ["no-secrets"],
"rules": {
"no-secrets/no-secrets": [
"error",
{ "additionalDelimiters": [".", "(?=[A-Z][a-z])"] }
]
}
}
| Option | Description | Default | Type |
|---|---|---|---|
| tolerance | Minimum "randomness"/entropy allowed. Only strings above this threshold will be shown. | 4 | number |
| additionalRegexes | Object of additional patterns to check. Key is check name and value is corresponding pattern | {} | {[regexCheckName:string]:string | RegExp} |
| ignoreContent | Will ignore the entire string if matched. Expects either a pattern or an array of patterns. This option takes precedent over additionalRegexes and the default regular expressions | [] | string | RegExp | (string|RegExp)[] |
| ignoreModules | Ignores strings that are an argument in import() and require() or is the path in an import statement. | true | boolean |
| ignoreIdentifiers | Ignores the values of properties and variables that match a pattern or an array of patterns. | [] | string | RegExp | (string|RegExp)[] |
| ignoreCase | Ignores character case when calculating entropy. This could lead to some false negatives | false | boolean |
| additionalDelimiters | In addition to splitting the string by whitespace, tokens will be further split by these delimiters | [] | (string|RegExp)[] |
Huge thanks to truffleHog for the inspiration, the regexes, and the measure of entropy.
FAQs
An eslint rule that searches for potential secrets/keys in code
The npm package eslint-plugin-no-secrets receives a total of 73,156 weekly downloads. As such, eslint-plugin-no-secrets popularity was classified as popular.
We found that eslint-plugin-no-secrets demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Python becomes GitHub's top language in 2024, driven by AI and data science projects, while AI-powered security tools are gaining adoption.

Security News
Dutch National Police and FBI dismantle Redline and Meta infostealer malware-as-a-service operations in Operation Magnus, seizing servers and source code.
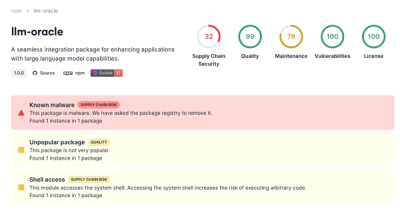
Research
Security News
Socket is tracking a new trend where malicious actors are now exploiting the popularity of LLM research to spread malware through seemingly useful open source packages.