
Research
Security News
Malicious npm Packages Inject SSH Backdoors via Typosquatted Libraries
Socket’s threat research team has detected six malicious npm packages typosquatting popular libraries to insert SSH backdoors.
generator-azuredatastudio
Advanced tools
The Azure Data Studio Extension Generator is a Yeoman-based generator to help get you started with authoring extensions. There are 13 different possible templates for you to use.
Ensure that you have Node.js and npm installed.
Install Yeoman and the Azure Data Studio Extension generator by using the following command:
npm install -g yo generator-azuredatastudio
To launch the generator type:
yo azuredatastudio
The extension generator will walk you through the steps required to create your customized extension with prompting for any required information.
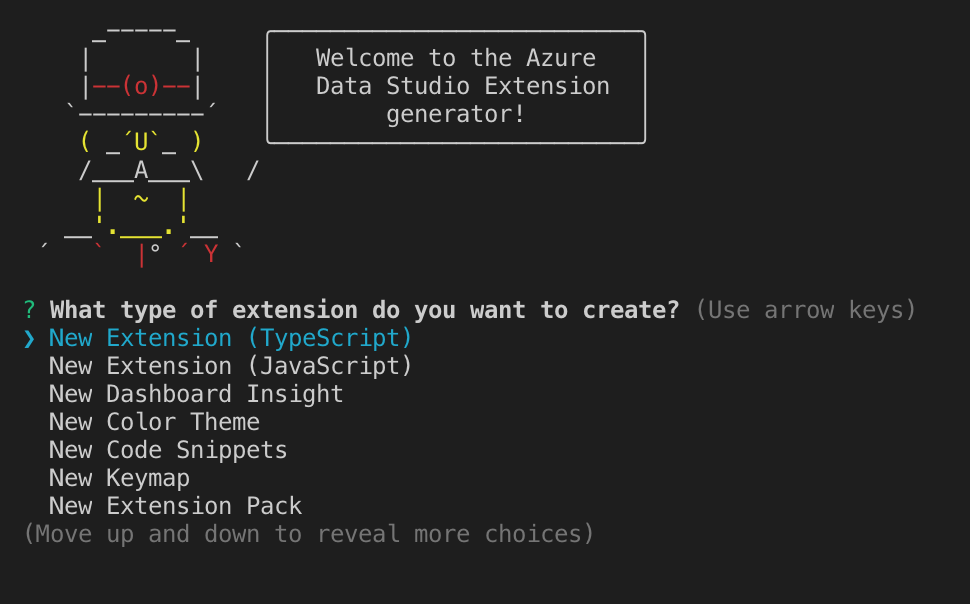
To learn more about extension authoring, there are a few resources you can view. For an overview on the extension authoring process, see Extension authoring. For a tutorial using the Extension Generator to create an extension, view Create an extension.
These templates will:
package.json using your answers from the provided promptslaunch.json for running your extension and attaching to a processvsc-extension-quickstart.md fileFAQs
Yeoman generator for Azure Data Studio Extensions
The npm package generator-azuredatastudio receives a total of 6 weekly downloads. As such, generator-azuredatastudio popularity was classified as not popular.
We found that generator-azuredatastudio demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 3 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Security News
Socket’s threat research team has detected six malicious npm packages typosquatting popular libraries to insert SSH backdoors.

Security News
MITRE's 2024 CWE Top 25 highlights critical software vulnerabilities like XSS, SQL Injection, and CSRF, reflecting shifts due to a refined ranking methodology.

Security News
In this segment of the Risky Business podcast, Feross Aboukhadijeh and Patrick Gray discuss the challenges of tracking malware discovered in open source softare.