
Research
Security News
Malicious npm Packages Inject SSH Backdoors via Typosquatted Libraries
Socket’s threat research team has detected six malicious npm packages typosquatting popular libraries to insert SSH backdoors.
A decorator for the AWS Data API for Aurora Serverless. It decorates and abstracts the Amazon SDK's implementation to make it feel more like a traditional MySQL wrapper than an HTTP based web service. It is written in Typescript and provides type-aware re
A decorator for the AWS Data API for Aurora Serverless. It decorates and abstracts the Amazon SDK's implementation to make it feel more like a traditional MySQL wrapper than an HTTP based web service. It is written in Typescript and provides type-aware return objects which allows for better support in Typescript-based solutions.
npm install rds-data
The decoration allows you to query, insert and update information like you would traditionally do with MySQL.
import { RDSDatabase } from "rds-data";
const params = {
region: "us-east-1",
secretArn: arn:aws:secretsmanager:us-east-1:xxxx:secret:yyyy,
resourceArn: arn:aws:rds:us-east-1:xxxx:cluster:yyyy,
database: dbname
};
const db = new RDSDatabase(params).getInstance();
const results = db.query( "SELECT id, name FROM NameTable WHERE name = :name", { name: "Chris Schuld" });
assert( results.data.length === 1);
assert( results.data[0].name.string === "Chris Schuld" );
const results = db.query( "INSERT INTO Name (id, name) VALUES(null, :name)", { name: "Chris Schuld" });
assert( results.insertId === X); // the id of the insert
assert( results.numberOfRecordsUpdated === 1 );
const results = db.query( "UPDATE Name SET name = :name WHERE id = :id LIMIT 1", { id: 10, name: "Chris Schuld" });
assert( results.numberOfRecordsUpdated === 1 );
await rds.transaction().then(async (transactionId) => {
await rds.query("INSERT INTO Name (name) VALUES(:name)",{ name: "Jules Winnfield" }, transactionId);
await rds.query("INSERT INTO Name (name) VALUES(:name)", { name: "Vincent Vega" }, transactionId);
await rds.query("INSERT INTO Name (name) VALUES(:name)", { name: "Marsellus Wallace" }, transactionId);
await rds.commit(transactionId);
});
// can do a rollback easily
await rds.rollback(transactionId);
Amazon AWS produces a Data API for Aurora Serverless which is a great API if you are building serverless solutions. One of the consistent challenges with serverless lambda in a VPC has extended cold start times and does not have access to the outside world unless you stand up a NAT Gateway. Thus, inside the VPC you can see your Aurora instances but you cannot see the outside world. The API provides a nice way to exist in the traditional lambda pool but still access your private LAN Aurora instance. The API also helps with connection pooling and other challenges with building serverless applications that may end up with aggressive concurrency.

The following are the options for setting up the RDSDatabase.
| Property | Type | Description |
|---|---|---|
| resourceArn | string | required - the ARN of your Aurora Serverless Cluster. |
| secretArn | string | required - the ARN of the secret associated with your database credentials. |
| database | string | required - the name of the database. |
| region | string | optional - AWS region to use (defaults to the AWS-SDK default. |
In order to use the Data API, you must enable it on your Aurora Serverless Cluster and create a Secret. You also must grant your execution environment a number of permission (see below):
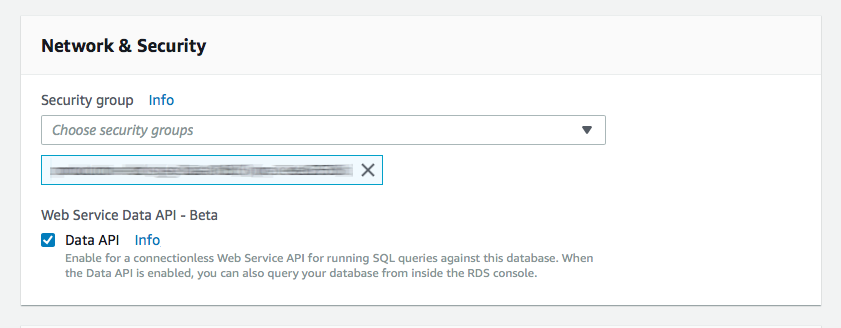
You need to modify your Aurora Serverless cluster by clicking "ACTIONS" and then "Modify Cluster". Just check the Data API box in the Network & Security section and you are done. Your Aurora Serverless cluster still runs in a VPC, even though you do not need to run your Lambdas in a VPC to access it via the Data API.
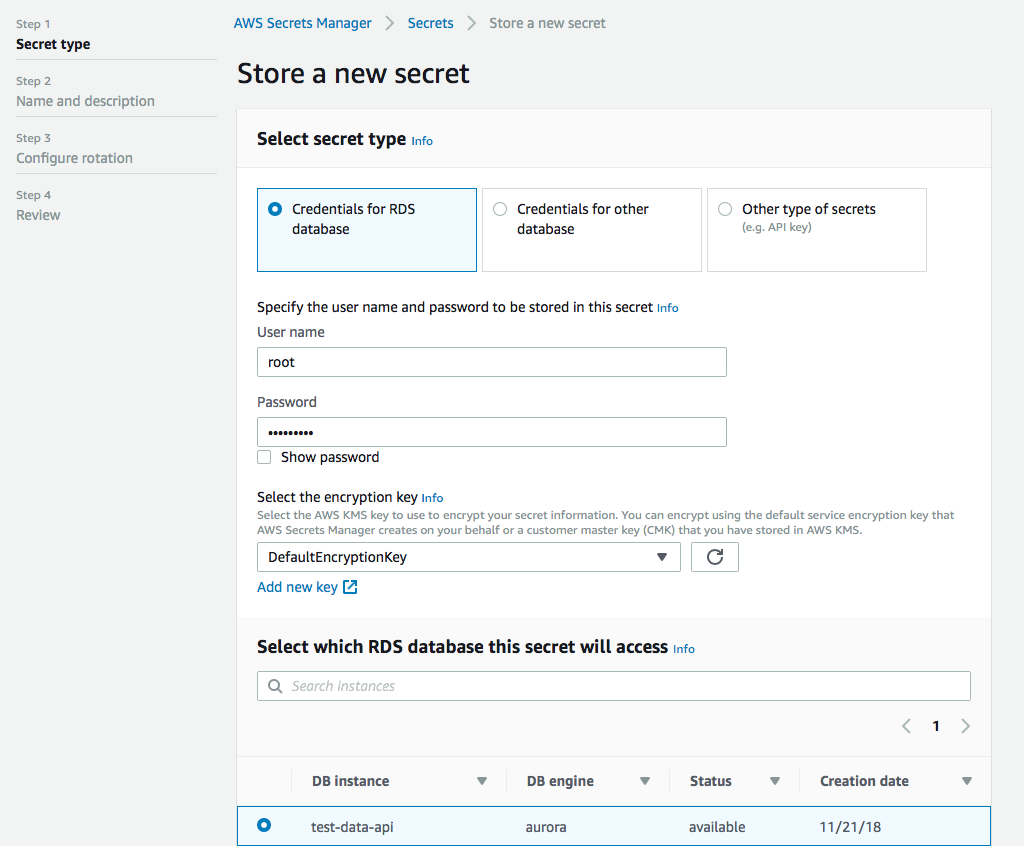
Next you need to setup a secret in the Secrets Manager. Username, password, encryption key (the default encryption key is probably fine for you), and select the database you want to access with the secret.
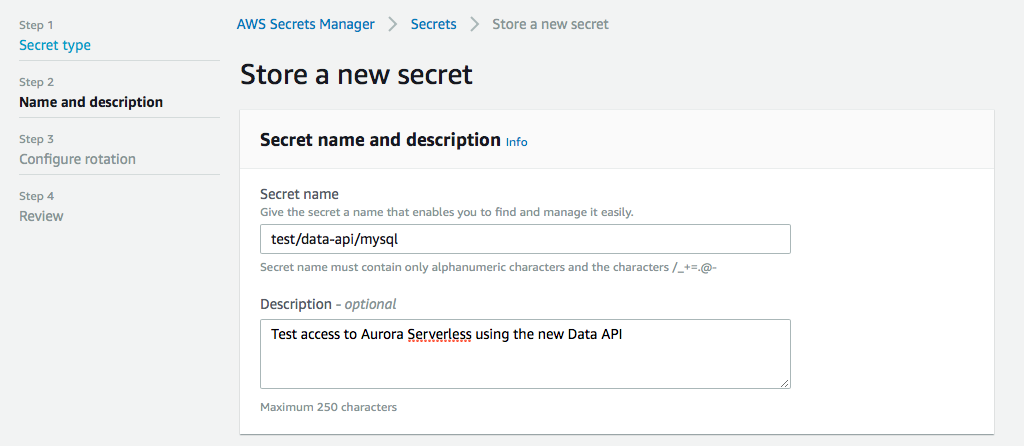
Next we give it a name, this is important, because this will be part of the arn when we set up permissions.
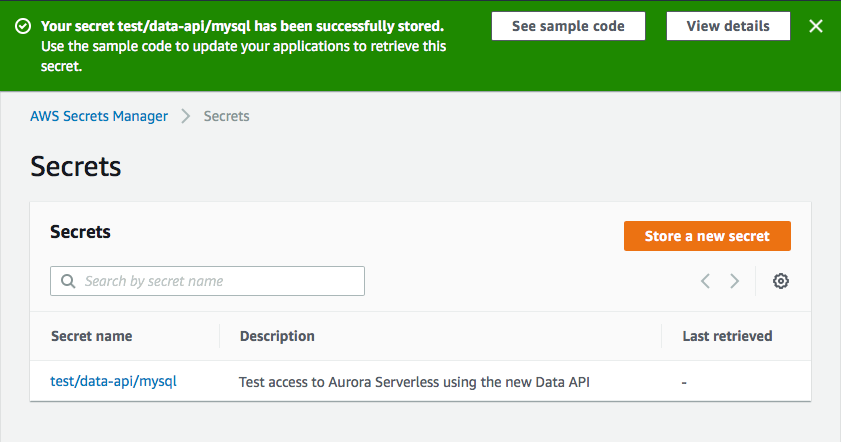
You can then configure your rotation settings, if you want, and then you review and create your secret. Then you can click on your newly created secret and grab the arn, we’re gonna need that next.
In order to use the Data API, your execution environment requires several IAM permissions. Below are the minimum permissions required.
YAML:
Statement:
- Effect: "Allow"
Action:
- "rds-data:ExecuteSql"
- "rds-data:ExecuteStatement"
- "rds-data:BatchExecuteStatement"
- "rds-data:BeginTransaction"
- "rds-data:RollbackTransaction"
- "rds-data:CommitTransaction"
Resource: "arn:aws:rds:{REGION}:{ACCOUNT-ID}:cluster:{YOUR-CLUSTER-NAME}"
- Effect: "Allow"
Action:
- "secretsmanager:GetSecretValue"
Resource: "arn:aws:secretsmanager:{REGION}:{ACCOUNT-ID}:secret:{PATH-TO-SECRET}/*"
JSON:
"Statement" : [
{
"Effect": "Allow",
"Action": [
"rds-data:ExecuteSql",
"rds-data:ExecuteStatement",
"rds-data:BatchExecuteStatement",
"rds-data:BeginTransaction",
"rds-data:RollbackTransaction",
"rds-data:CommitTransaction"
],
"Resource": "arn:aws:rds:{REGION}:{ACCOUNT-ID}:cluster:{YOUR-CLUSTER-NAME}"
},
{
"Effect": "Allow",
"Action": [ "secretsmanager:GetSecretValue" ],
"Resource": "arn:aws:secretsmanager:{REGION}:{ACCOUNT-ID}:secret:{PATH-TO-SECRET}/*"
}
]
Special thanks to Jeremy Daly whom was an early adopter of the RDS Data API as well and provides a similar package called the data-api-client. A lot of his work is similar but less type aware. Additionally portions of this readme are extracted from Jeremy's work!
FAQs
A decorator for the AWS Data API for Aurora Serverless. It decorates and abstracts the Amazon SDK's implementation to make it feel more like a traditional MySQL wrapper than an HTTP based web service. It is written in Typescript and provides type-aware re
The npm package rds-data receives a total of 52 weekly downloads. As such, rds-data popularity was classified as not popular.
We found that rds-data demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Security News
Socket’s threat research team has detected six malicious npm packages typosquatting popular libraries to insert SSH backdoors.

Security News
MITRE's 2024 CWE Top 25 highlights critical software vulnerabilities like XSS, SQL Injection, and CSRF, reflecting shifts due to a refined ranking methodology.

Security News
In this segment of the Risky Business podcast, Feross Aboukhadijeh and Patrick Gray discuss the challenges of tracking malware discovered in open source softare.