
audiocat
Audiocat is a command-line utility for Linux that reads and writes encrypted data across peer-to-peer or broadcast audio connections, using minimodem and gpg.
It is a powerful tool that can be combined with any audio infrastructure (like PSTN, cellular network, internet, radio, walkie-talkies) to provide a secure communication channel through an audio tunnel.
The audio interfaces behave like data-diodes, each allowing unidirectional data transmission only, thus preventing data-leaks and malware-injection.
This enables an "enhanced"-end-to-end encryption (E-E2EE) which notably increases security and privacy, especially when the end devices are completely offline (air-gapped-system), thus providing an effective barrier against "legal or illegal" client-side-scanning!
See also https://www.codeproject.com/Articles/5295970/Audio-Chat-for-Quite-Good-Privacy-AC4QGP
Installation
pip install audiocat-clark
or with git:
git clone https://github.com/ClarkFieseln/audiocat.git
cd audiocat_clark
chmod +x audiocat
chmod +x *.sh
during first execution you will be asked to install dependencies: minimodem, gpg, bc
but you can also install them yourself with:
sudo apt install minimodem
sudo apt install gpg
sudo apt install bc
The package gnome-terminal is assumed to be already installed, install otherwise or change cfg/terminal.
How to use (pip installation)
Chat/Messenger
audiocat -c
enter and confirm password
On the other device a chat or a remote shell can be started.
Remote Shell
audiocat -s
then enter and confirm password
On the other device a chat shall be started to command the remote shell.
Note that this is technically a "reverse shell" which gives access to your system!
File Transfer
audiocat -f
enter and confirm password
On the other device a file transfer shall be started.
Probe
To check connectivity and adjust volumes if required.
audiocat -p
In addition, a separate terminal will be opened to read unencrypted probe messages being sent by the other side.
Configuration
Adapt the configuration as required using the 'terminal GUI' with:
audiocat -g
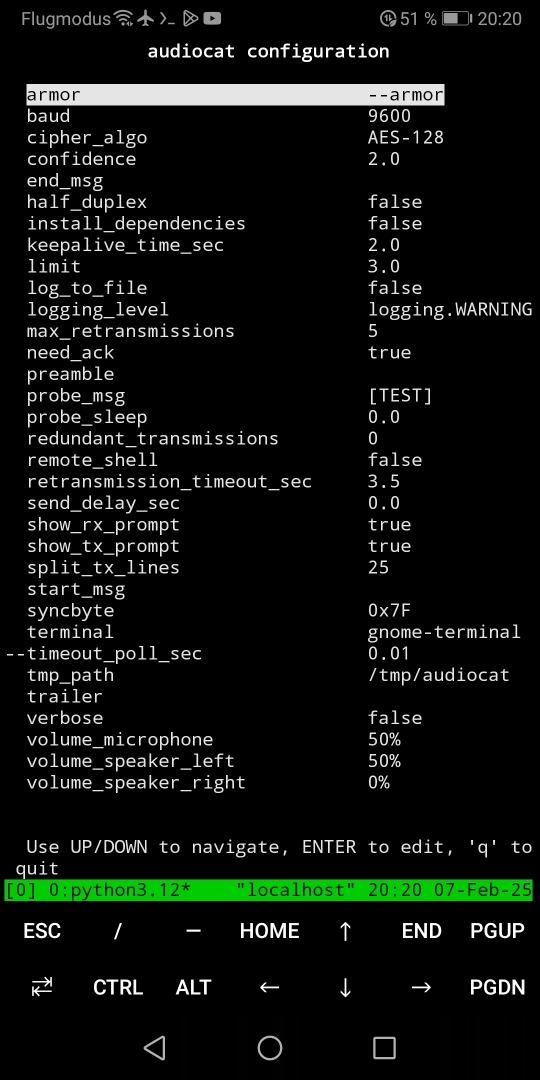
Alternatively, you may change the configuration by editing the files in the cfg folder directly. The 'Location' can be found with:
audiocat -d
The most important settings are:
- baud
- keepalive_time_sec
- retransmission_timeout_sec
- split_tx_lines
- volume_microphone
- volume_speaker_left
- volume_speaker_right
Note that the communication partners may require different values as it is the case with keepalive_time_sec !
How to use (git installation)
When installed with git, audiocat may be called with:
python3 audiocat.py -c
# or
./audiocat -c
This is an example to start a chat, but this is the same for any other option.
For more information check the documentation.
Features
on top of the audio modem provided by minimodem and encryption provided by GPG, audiocat offers a reliable transport layer and many other features:
-
modes: chat, remote-shell, file transfer (future: sniffer)
-
full-duplex communication
-
retransmit messages automatically after communication errors
-
split big messages into smaller data chunks in order to increase the probability of reception, thus reducing retransmissions
-
[keepalive] messages
-
redundant transmission of "data-messages"
-
composition of piped commands hidden to the user
-
tmp folder located in a configurable path beneath $HOME, independent of the current path.
-
probe, to check volume on receiver and adjust manually if needed
(very high and very low volumes may produce signal distortions)
-
"braodcast" transmissions also possible, e.g. when ACKs are deactivated
use-case: walkie-talkie, Radio station, ...
-
several configuration options: preamble, trailer, delays, cipher algorithm, confidence, log to file, verbose, etc.
Possible Abuses
please don't do the following if you are not allowed (it might be illegal!):
-
exfiltrate data over the air or cable to a nearby or remote computer
-
remote control over the air or cable from a nearby or remote computer
-
exfiltrate data from a computer evading classical auditing
(be aware that if you do this on your employer's computer you might be infringing the law!)
-
use the tool as a "side-channel" for covert communication e.g. to spread or inject malware,
even worse when combined with steganography (e.g. low volumes, data hidden in noise)
Typical Configuration
 A: audiocat in offline PC (Alice)
A: audiocat in offline PC (Alice)
D: audiocat in offline PC (Bob)
B, C: smartphone with call session (mobile, messenger app, etc.)
diodes: audio connections (sink/speaker -> source/microphone)
Communication in Linux over Linphone

A: audiocat in offline PC (Alice)
D: audiocat in offline PC (Bob)
B, C: smartphone with Linphone call session
Communication in Termux over qTox

A: audiocat in offline smartphone with Termux (Alice)
D: audiocat in offline smartphone with Termux (Bob)
B, C: PC with qTox call session
Communication in Linux over Walkie Talkies

Split Configuration

A: audiocat in offline PC (Alice)
D: audiocat in offline PC (Bob)
B1, B2, C1, C2: waklie-talkie
Limitations
The data transfer is usually done at low rates, typical of audio systems. Therefore, this tool is not adequate to transmit big files which may take a long time to complete.
Hints
Avoid using tools like PulseEffects, they may produce glitches!
PyPi Project
https://pypi.org/project/audiocat-clark
GitHub Project
https://github.com/ClarkFieseln/audiocat
Documentation
https://github.com/ClarkFieseln/audiocat/blob/main/doc/documentation.md
Screenshots
https://github.com/ClarkFieseln/audiocat/tree/main/screenshots
Videos
https://www.youtube.com/playlist?list=PLX24fhcibpHUx7ej_Tp4neobJUqOkqliN
License
(c) 2025 Clark Fieseln
This repository is licensed under the MIT license. See LICENSE for details.



 A: audiocat in offline PC (Alice)
A: audiocat in offline PC (Alice)





