







 EOReader
EOReader
EOReader is a remote-sensing opensource python library reading optical
and SAR constellations, loading and stacking bands,
clouds, DEM and spectral indices in a sensor-agnostic way.
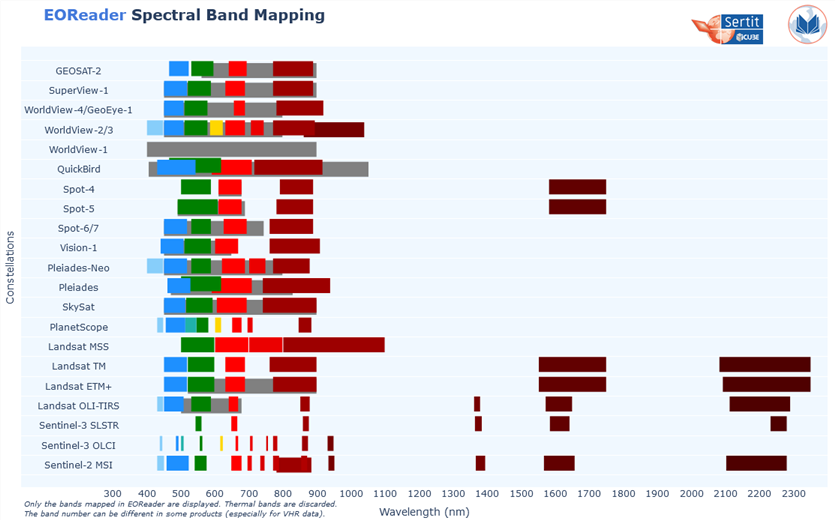
Managed optical constellations

Managed SAR constellations

Features
EOReader implements sensor-agnostic features:
load: Load many band types:
stack: Stack all these type of bands
EOReader works mainly with:
Python Quickstart
Optical
EOReader allows you ta load and stack spectral bands, spetrcal indices, DEM and cloud bands agnostically from every handled optical constellation:
from eoreader.reader import Reader
from eoreader.bands import *
s2_path = "S2B_MSIL1C_20181126T022319_N0207_R103_T51PWM_20181126T050025.SAFE"
reader = Reader()
s2_prod = reader.open(s2_path)
bands = s2_prod.load([NDVI, GREEN, CLOUDS])
stack = s2_prod.stack([RED, GREEN, BLUE], stack_path="s2_rgb_stack.tif")
EOReader aligns spectral bands from every handled sensor in order to make any call to a band generic:
SAR
In the same way, you can import and stack radar band from any handled SAR constellation, with the same pattern.
from eoreader.reader import Reader
from eoreader.bands import *
s1_path = "S1B_EW_GRDM_1SDH_20200422T080459_20200422T080559_021254_028559_784D.zip"
reader = Reader()
s1_prod = reader.open(s1_path)
bands = s1_prod.load([VV, VH])
stack = s1_prod.stack([VV_DSPK, VH_DSPK], stack_path="s1_stack.tif")
⚠️SNAP and SAR
SAR products need ESA SNAP
free software to be orthorectified and calibrated.
Ensure that you have the folder containing your gpt executable in your PATH.
If you are using SNAP 8.0, be sure to have your software up-to-date (SNAP version >= 8.0).
Documentation
The API documentation can be found here.
Examples
Available notebooks provided as examples:
Installation
Pip
You can install EOReader via pip:
pip install eoreader
EOReader mainly relies on geopandas and rasterio (through rioxarray).
On Windows and with pip, you may face installation issues due to GDAL.
The well known workaround of installing from Gohlke's wheels
also applies here.
Please look at the rasterio page
to learn more about that.
Conda
You can install EOReader via conda:
conda config --env --set channel_priority strict
conda install -c conda-forge eoreader
Context
As one of the Copernicus Emergency Management Service Rapid Mapping and Risk and Recovery Mapping operators,
SERTIT needs to deliver geoinformation (such as flood or fire delineation, landslides mapping, etc.) based on multiple EO constellations.
In rapid mapping, it is always important to have access to various sensor types, resolutions, and satellites. Indeed, SAR sensors are able to detect through clouds and during nighttime
(which is particularly useful during flood and storm events), while optical sensors benefit from of multi spectral bands to better analyze and classify the crisis information.
As every minute counts in the production of geoinformation in an emergency mode, it seemed crucial to harmonize the ground on which are built our production tools, in order to make them as
sensor-agnostic as possible.
This is why SERTIT decided to decouple the sensor handling from the extraction algorithms: the latter should be able to ingest semantic bands
(i.e. RED or VV) without worrying about how to load the specific sensor band or in what unit it is.
The assumption was made that all the spectral bands from optical sensors could be mapped between each other, in addition to the natural mapping between SAR bands.
Thus, thanks to EOReader, these tools are made independent to the constellation:
✅ the algorithm (and its developer) can focus on its core tasks (such as extraction) without taking into account the sensor characteristics
(how to load a band, which band correspond to which band number, …)
✅ new sensor addition is effortless (if existing in EOReader) and requires no algorithm modification
✅ maintenance is simplified and the code quality is significantly improved
✅ testing is also simplified as the sensor-related parts are tested in EOReader library
However, keep in mind that the support of all the constellations used in CEMS is done in the best effort mode, especially for commercial data.
Indeed, we may not have faced every product type, sensor mode or order configuration, so some details may be missing.
If this happens to you, do not hesitate to make a PR or write an issue about that !
Talks
Press Release
Articles
Blog
License
EOReader is licensed under Apache License v2.0. See LICENSE file for details.
Authors
EOReader has been created by ICube-SERTIT.
Credits
EOReader is built on top of amazing libs, without which it couldn't have been coded:











