Language Server Protocol integration for Jupyter(Lab)






Installation | Configuring | Changelog | Roadmap | Contributing | Extending
Features
Examples show Python code, but most features also work in R, bash, typescript, and many other languages.
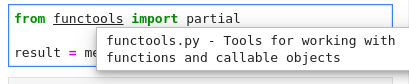
Hover
Hover over any piece of code; if an underline appears, you can press Ctrl
to get a tooltip with function/class signature, module documentation or any other
piece of information that the language server provides
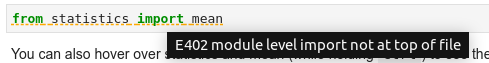
Diagnostics
Critical errors have red underline, warnings are orange, etc. Hover
over the underlined code to see a more detailed message
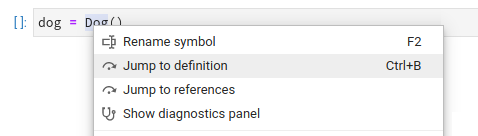
Jump to Definition and References
Use the context menu entry, or Alt + :computer_mouse: to jump to definitions/references (you can change it to Ctrl/⌘ in settings); use Alt + o to jump back.
Highlight References
Place your cursor on a variable, function, etc and all the usages will be highlighted
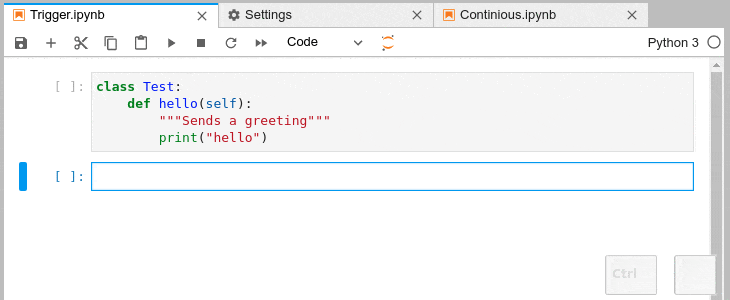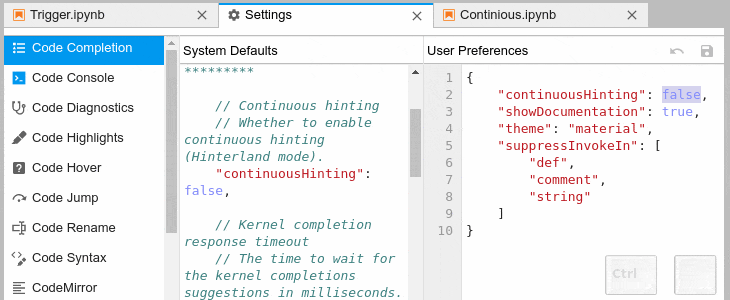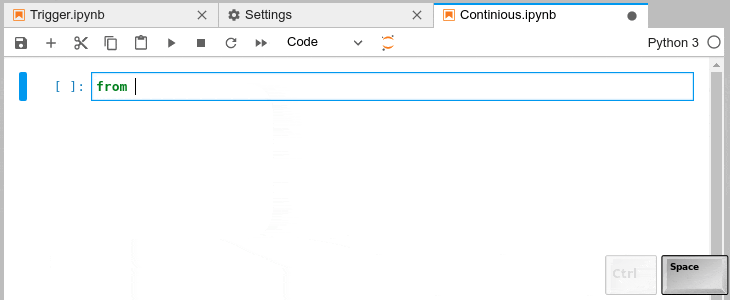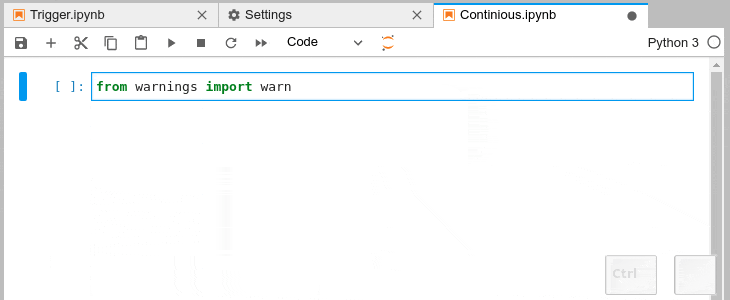
Automatic Completion and Continuous Hinting
- Certain characters, for example '.' (dot) in Python, will automatically trigger
completion.
- You can choose to receive the completion suggestions as you type by enabling
continuousHinting setting.
Automatic Signature Suggestions
Function signatures will automatically be displayed
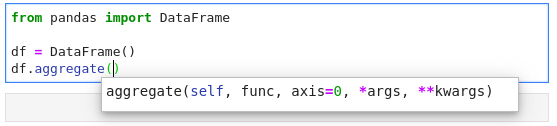
Kernel-less Autocompletion
Advanced static-analysis autocompletion without a running kernel
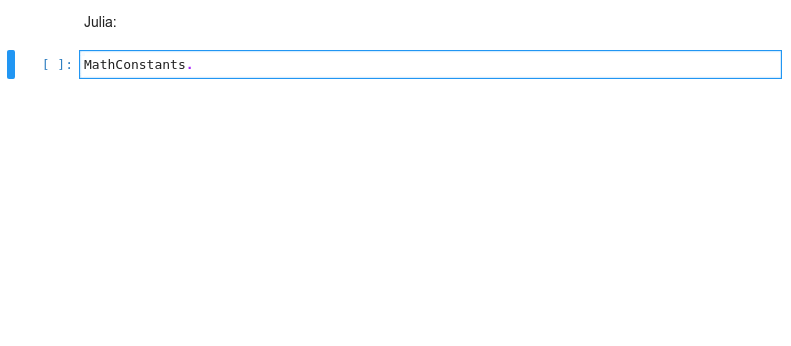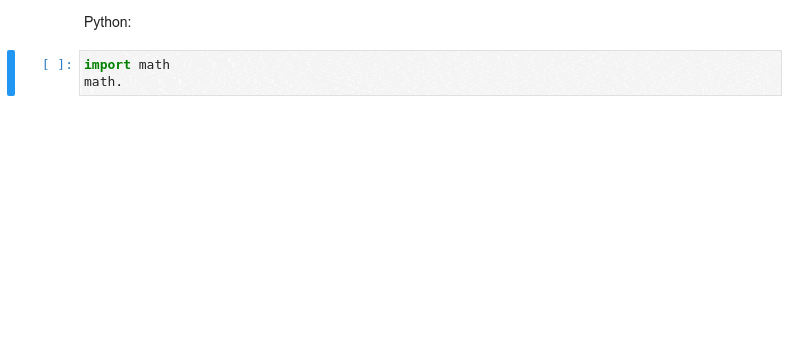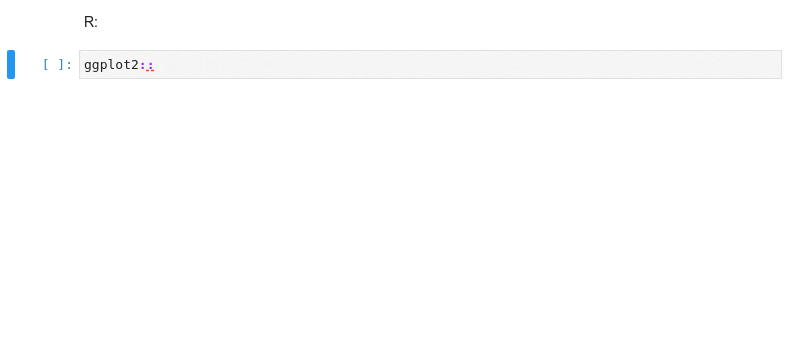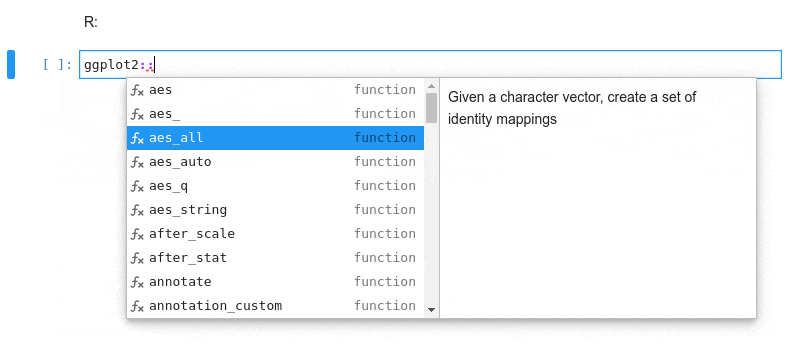
The runtime kernel suggestions are still there
When a kernel is available the suggestions from the kernel (such as keys of a
dict and columns of a DataFrame) are merged with the suggestions
from the Language Server (in notebook).
If the kernel is too slow to respond promptly only the Language Server suggestions will be shown (default threshold: 0.6s).
You can configure the completer to not attempt to fetch the kernel completions if the kernel is busy (skipping the 0.6s timeout).
You can deactivate the kernel suggestions by adding "Kernel" to the disableCompletionsFrom in the completion section
of Advanced Settings. Alternatively if you only want kernel completions you can add "LSP" to the same
setting; Or add both if you like to code in hardcore mode and get no completions, or if another provider has been added.
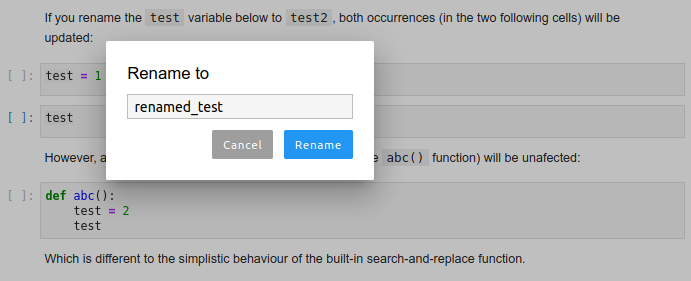
Rename
Rename variables, functions and more, in both: notebooks and the file editor.
Use the context menu option or the F2 shortcut to invoke.
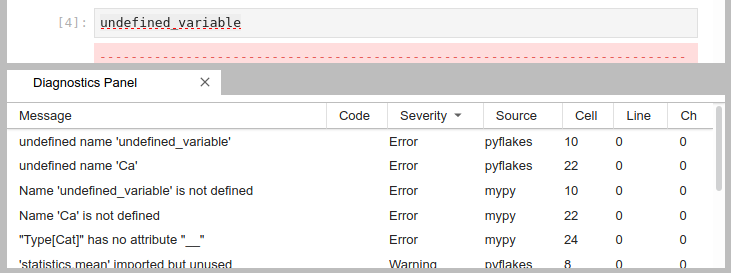
Diagnostics panel
Sort and jump between the diagnostics using the diagnostics panel.
Open it searching for "Show diagnostics panel" in JupyterLab commands palette or from the context menu.
Use context menu on rows in the panel to filter out diagnostics or copy their message.
Prerequisites
You will need to have both of the following installed:
- JupyterLab >=4.1.0,<5.0.0a0
- Python 3.8+
In addition, if you wish to use javascript, html, markdown or any other NodeJS-based language server you will need to have appropriate NodeJS version installed.
Note: Installation for JupyterLab 2.x requires a different procedure, please consult the documentation for the extension version 2.x.
Installation
For more extensive installation instructions, see the documentation.
For the current stable version, the following steps are recommended.
Use of a python virtualenv or a conda env is also recommended.
-
install python 3
conda install -c conda-forge python=3
-
install JupyterLab and the extensions
conda install -c conda-forge 'jupyterlab>=4.1.0,<5.0.0a0' jupyterlab-lsp
pip install 'jupyterlab>=4.1.0,<5.0.0a0' jupyterlab-lsp
Note: jupyterlab-lsp provides both the server extension and the lab extension.
Note: With conda, you could take advantage of the bundles: jupyter-lsp-python
or jupyter-lsp-r to install both the server extension and the language server.
-
install LSP servers for languages of your choice; for example, for Python
(pylsp) and
R (languageserver) servers:
pip install 'python-lsp-server[all]'
R -e 'install.packages("languageserver")'
or from conda-forge
conda install -c conda-forge python-lsp-server r-languageserver
Please see our full list of
supported language servers
which includes installation hints for the common package managers (npm/pip/conda).
In general, any LSP server from the
Microsoft list
should work after some additional configuration.
Note: it is worth visiting the repository of each server you install as
many provide additional configuration options.
-
Restart JupyterLab
If JupyterLab is running when you installed the extension, a restart is required
for the server extension and any language servers to be recognized by JupyterLab.
-
(Optional, IPython users only) to improve the performance of autocompletion,
disable Jedi in IPython (the LSP servers for Python use Jedi too).
You can do that temporarily with:
%config Completer.use_jedi = False
or permanently by setting c.Completer.use_jedi = False in your
ipython_config.py file.
-
(Optional, Linux/OSX-only) As a security measure by default Jupyter server only allows
access to files under the Jupyter root directory (the place where you launch the Jupyter server).
Thus, in order to allow jupyterlab-lsp to navigate to external files such as packages
installed system-wide or to libraries inside a virtual environment (conda,
pip, ...) this access control mechanism needs to be circumvented: inside your Jupyter
root directory create a symlink named .lsp_symlink pointing to your system root /.
ln -s / .lsp_symlink
As this symlink is a hidden file the Jupyter server must be instructed to
serve hidden files. Either use the appropriate command line flag:
jupyter lab --ContentsManager.allow_hidden=True
or, alternatively, set the corresponding setting inside your jupyter_server_config.py.
Help in implementing a custom ContentsManager
which will enable navigating to external files without the symlink is welcome.
Configuring the servers
Server configurations can be edited using the Advanced Settings editor in JupyterLab (Settings > Advanced Settings Editor). For settings specific to each server, please see the table of language servers. Example settings might include:
{
"language_servers": {
"pylsp": {
"serverSettings": {
"pylsp.plugins.pydocstyle.enabled": true,
"pylsp.plugins.pyflakes.enabled": false,
"pylsp.plugins.flake8.enabled": true
}
},
"r-languageserver": {
"serverSettings": {
"r.lsp.debug": false,
"r.lsp.diagnostics": false
}
}
}
}
The serverSettings key specifies the configurations sent to the language servers. These can be written using stringified dot accessors like above (in the VSCode style), or as nested JSON objects, e.g.:
{
"language_servers": {
"pylsp": {
"serverSettings": {
"pylsp": {
"plugins": {
"pydocstyle": {
"enabled": true
},
"pyflakes": {
"enabled": false
},
"flake8": {
"enabled": true
}
}
}
}
}
}
}
Other configuration methods
Some language servers, such as pylsp, provide other configuration methods in addition to language-server configuration messages (accessed using the Advanced Settings Editor). For example, pylsp allows users to configure the server using a local configuration file. You can change the inspection/diagnostics for server plugins like pycodestyle there.
The exact configuration details will vary between operating systems (please see the configuration section of pycodestyle documentation), but as an example, on Linux you would simply need to create a file called ~/.config/pycodestyle, which may look like that:
[pycodestyle]
ignore = E402, E703
max-line-length = 120
In the example above:
- ignoring E402 allows imports which are not on the very top of the file,
- ignoring E703 allows terminating semicolon (useful for matplotlib plots),
- the maximal allowed line length is increased to 120.
After changing the configuration you may need to restart the JupyterLab, and please be advised that the errors in configuration may prevent the servers from functioning properly.
Again, please do check the pycodestyle documentation for specific error codes, and check the configuration of other feature providers and language servers as needed.
Acknowledgements
This would not be possible without the fantastic initial work at
wylieconlon/lsp-editor-adapter.















