
Security News
Research
Data Theft Repackaged: A Case Study in Malicious Wrapper Packages on npm
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.

ufolint is a source file linter for typeface development in Unified Font Object (UFO) source code. It was designed for continuous integration testing of UFO source contributions to typeface projects.
The application performs a UFO version specific static analysis of the source text files against the UFO v2 and v3 specifications for issues that include:
These tests are performed through a combination of public methods in the fontTools.ufoLib library and additional tests that are implemented in the ufolint application. ufolint catches exceptions raised in the ufoLib public read methods for all _.plist file types and all ufoLib validations performed on _.glif files. These are returned to users with informative error messages that indicate the filepath(s) of concern and exit status code 1.
ufolint can be run locally or with remote CI testing services.
Use the command:
$ pip install ufolint
Upgrade to a new version of the application with the command:
$ pip install --upgrade ufolint
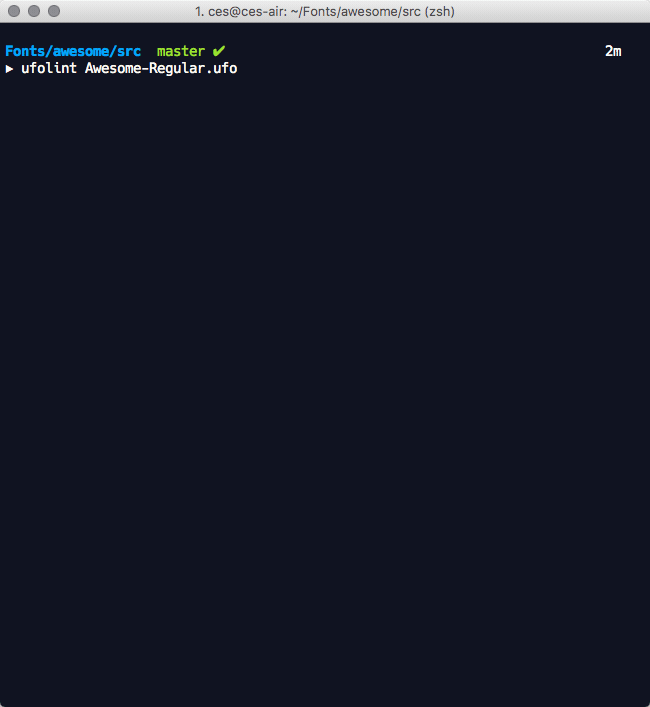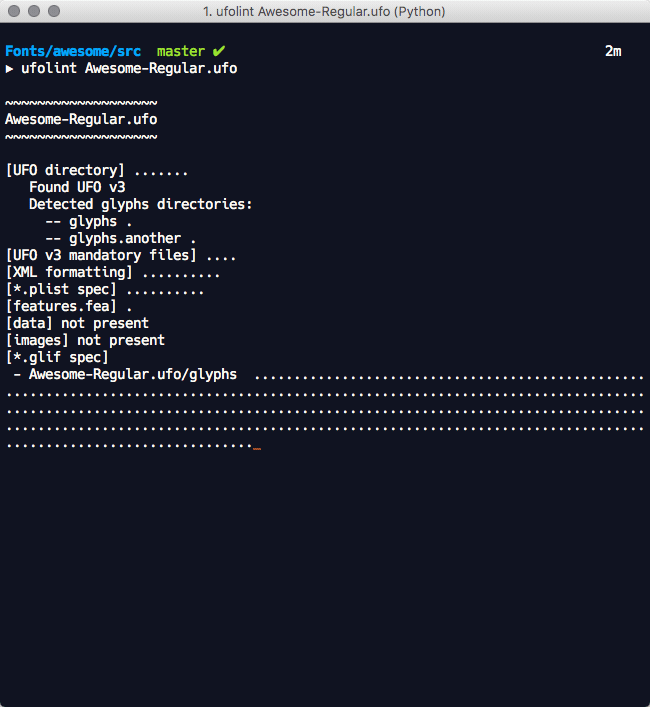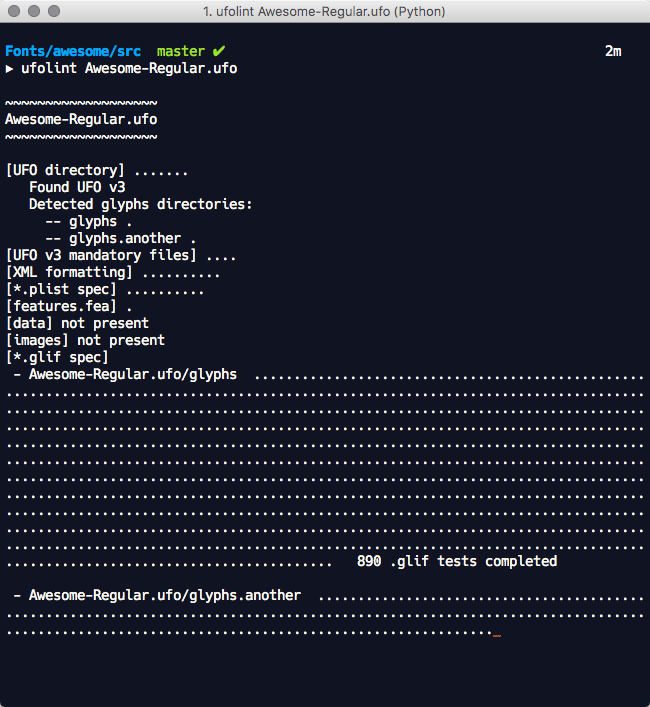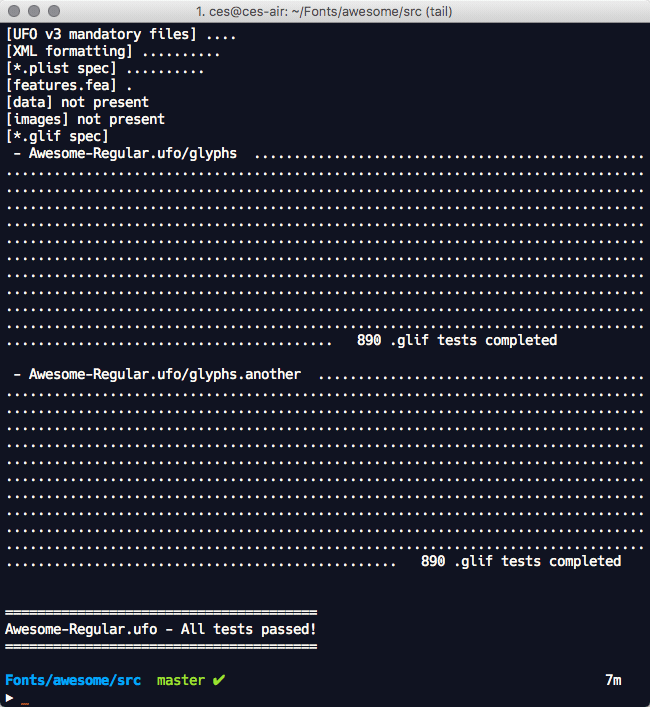
The process is fully automated. Simply point ufolint to one or more UFO source directories and it takes care of the rest. ufolint exits with status code 0 if all tests pass and exits with status code 1 if any tests fail.
$ ufolint [UFO source path] ([UFO path 2] [UFO path3]...)
$ ufolint Awesome-Regular.ufo Awesome-Bold.ufo
For critical failures that prevent the completion of further testing, ufolint exits immediately and other tests are aborted. In all other circumstances, failures are collected across the entire analysis and displayed at the completion of all tests.
ufolint provides verbose, useful error messages that include the file(s) of concern, the error type, and in many cases, the problematic line in the file.
To continuously test your UFO source changes on Travis with each commit pushed or pull request submitted to your Github repository, use these initial two steps from the Travis Getting Started Guide:
Then in your Github repository,
.travis.yml in the root of your Github repository that includes the following text:sudo: false
language: python
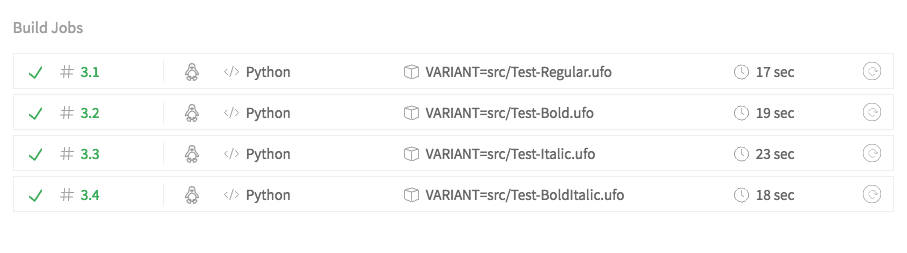
env:
- VARIANT=src/Test-Regular.ufo
- VARIANT=src/Test-Bold.ufo
- VARIANT=src/Test-Italic.ufo
- VARIANT=src/Test-BoldItalic.ufo
before_script: pip install ufolint
script: "ufolint $VARIANT"
notifications:
email: false
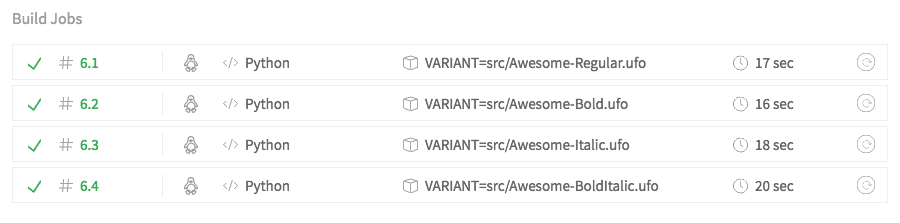
VARIANT=src/Test-*.ufo lines in the .travis.yml file with the actual paths to your UFO source files after the = character. Use one line per variant and add or subtract lines as necessary to test the desired source UFO directories in the repository. These should be relative paths from the root of your git repository.This Travis setting structure performs the variant tests in parallel for each of the variants specified under the env field of the Travis settings file. Each variant will be labeled on the Travis testing page like this:
Step 5: With each new commit pushed to your Github repository (or any new pull request submitted by others) Travis is automatically notified and performs the ufolint tests on the modified (or proposed modifications for pull requests) UFO source. You can view the test results on your Travis account page for the repository.
Optional: To add a Travis test result badge to your repository README page, insert the following Markdown in your README page and modify [ACCOUNT] and [REPOSITORY] with your Travis account and repository details:
[](https://travis-ci.org/[ACCOUNT]/[REPOSITORY])
Built with the fantastic fontTools ufoLib library where a majority of the UFO validation work has been performed!
FAQs
UFO source file linter
We found that ufolint demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Research
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.

Research
Security News
Attackers used a malicious npm package typosquatting a popular ESLint plugin to steal sensitive data, execute commands, and exploit developer systems.

Security News
The Ultralytics' PyPI Package was compromised four times in one weekend through GitHub Actions cache poisoning and failure to rotate previously compromised API tokens.