
Security News
Research
Data Theft Repackaged: A Case Study in Malicious Wrapper Packages on npm
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.
ViZDoom is Doom-based AI Research Platform for Reinforcement Learning from Raw Visual Information.

ViZDoom allows developing AI bots that play Doom using only visual information (the screen buffer). It is primarily intended for research in machine visual learning, and deep reinforcement learning, in particular.
ViZDoom is based on ZDoom engine to provide the game mechanics.
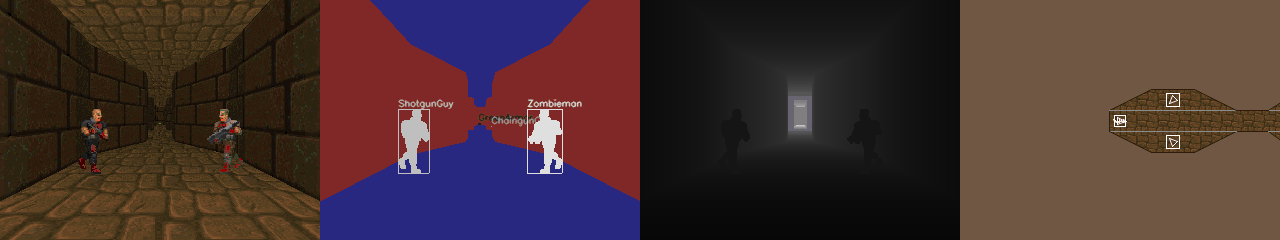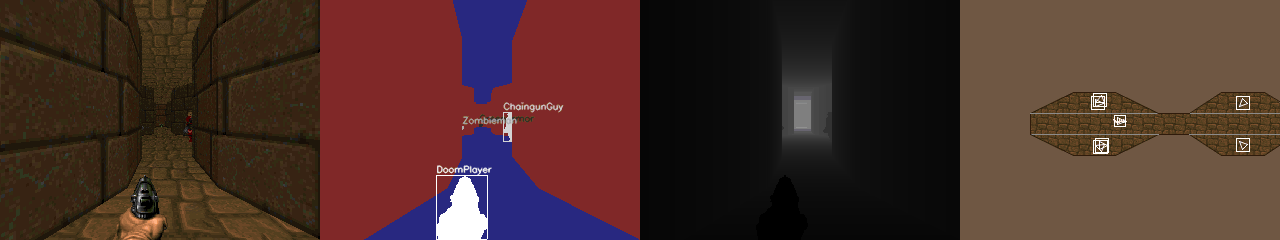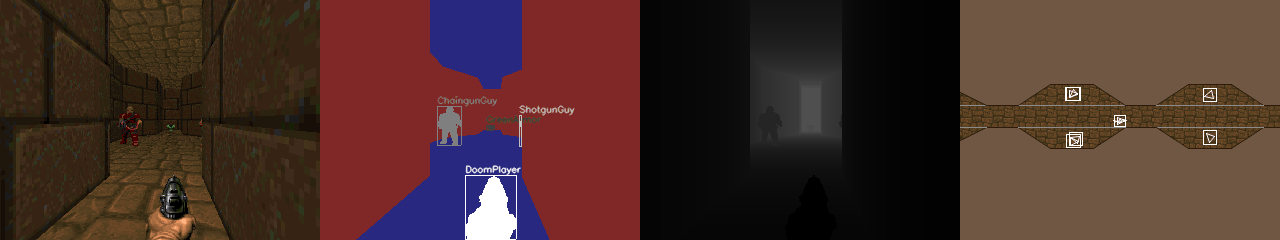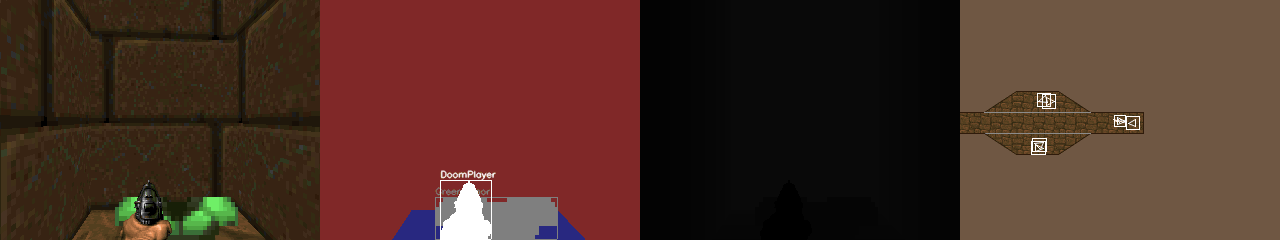
ViZDoom API is reinforcement learning friendly (suitable also for learning from demonstration, apprenticeship learning or apprenticeship via inverse reinforcement learning, etc.).
Julia (thanks to Jun Tian), Lua, and Java bindings are available in other branches but are no longer maintained.
M Wydmuch, M Kempka & W Jaśkowski, ViZDoom Competitions: Playing Doom from Pixels, IEEE Transactions on Games, vol. 11, no. 3, pp. 248-259, 2019 (arXiv:1809.03470)
@article{Wydmuch2019ViZdoom,
author = {Marek Wydmuch and Micha{\l} Kempka and Wojciech Ja\'skowski},
title = {{ViZDoom} {C}ompetitions: {P}laying {D}oom from {P}ixels},
journal = {IEEE Transactions on Games},
year = {2019},
volume = {11},
number = {3},
pages = {248--259},
doi = {10.1109/TG.2018.2877047},
note = {The 2022 IEEE Transactions on Games Outstanding Paper Award}
}
or
M. Kempka, M. Wydmuch, G. Runc, J. Toczek & W. Jaśkowski, ViZDoom: A Doom-based AI Research Platform for Visual Reinforcement Learning, IEEE Conference on Computational Intelligence and Games, pp. 341-348, Santorini, Greece, 2016 (arXiv:1605.02097)
@inproceedings{Kempka2016ViZDoom,
author = {Micha{\l} Kempka and Marek Wydmuch and Grzegorz Runc and Jakub Toczek and Wojciech Ja\'skowski},
title = {{ViZDoom}: A {D}oom-based {AI} Research Platform for Visual Reinforcement Learning},
booktitle = {IEEE Conference on Computational Intelligence and Games},
year = {2016},
address = {Santorini, Greece},
month = {Sep},
pages = {341--348},
publisher = {IEEE},
doi = {10.1109/CIG.2016.7860433},
note = {The Best Paper Award}
}
To install the latest release of ViZDoom, just run:
pip install vizdoom
Both x86-64 and AArch64 (ARM64) architectures are supported. Wheels are available for Python 3.8+ on Linux.
If Python wheel is not available for your platform (Python version <3.8, distros below manylinux_2_28 standard), pip will try to install (build) ViZDoom from the source. ViZDoom requires a C++11 compiler, CMake 3.12+, Boost 1.54+ SDL2, OpenAL (optional), and Python 3.8+ to install from source. See documentation for more details.
To install the latest release of ViZDoom, just run:
pip install vizdoom
Both Intel and Apple Silicon CPUs are supported. Pre-build wheels are available for Intel macOS 12.0+ and Apple Silicon macOS 14.0+.
If Python wheel is not available for your platform (Python version <3.8, older macOS version), pip will try to install (build) ViZDoom from the source. In this case, install the required dependencies using Homebrew:
brew install cmake boost sdl2
We recommend using at least macOS High Sierra 10.13+ with Python 3.8+. On Apple Silicon (M1, M2, and M3), make sure you are using Python/Pip for Apple Silicon.
To install the latest release of ViZDoom, just run:
pip install vizdoom
At the moment, only x86-64 architecture is supported on Windows. Wheels are available for Python 3.9+ on Windows.
Please note that the Windows version is not as well-tested as Linux and macOS versions. It can be used for development and testing but if you want to conduct serious (time and resource-extensive) experiments on Windows, please consider using Docker or WSL with Linux version.
Gymnasium environments are installed along with ViZDoom. See documentation and examples on the use of Gymnasium API.
OpenAI-Gym wrappers are also available, to install them run:
pip install vizdoom[gym]
See documentation and examples on the use of Gym API. OpenAI-Gym wrappers are deprecated and will be removed in future versions in favor of Gymnasium.
Python examples are currently the richest, so we recommend looking at them, even if you plan to use C++. The API is almost identical between the languages, with the only difference being that Python uses snake_case and C++ camelCase for methods and functions.
Unfortunately, we cannot distribute ViZDoom with original Doom graphics.
If you own original Doom or Doom 2 games, you can replace Freedoom graphics by placing doom.wad or doom2.wad into your working directory or vizdoom package directory.
Alternatively, any base game WAD (including other Doom engine-based games and custom/community games) can be used by pointing to it with the set_doom_game_path/setDoomGamePath method.
Detailed descriptions of all ViZDoom types and methods can be found in the documentation.
Full documentation of the ZDoom engine and ACS scripting language can be found on ZDoom Wiki.
Useful articles (for advanced users who want to create custom environments/scenarios):
This project is maintained and developed in our free time. All bug fixes, new examples, scenarios, and other contributions are welcome! We are also open to feature ideas and design suggestions.
We have a roadmap for future development work for ViZDoom available here.
The code original to ViZDoom is under MIT license. ZDoom uses code from several sources with varying licensing schemes.
FAQs
ViZDoom is Doom-based AI Research Platform for Reinforcement Learning from Raw Visual Information.
We found that vizdoom demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 4 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Research
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.

Research
Security News
Attackers used a malicious npm package typosquatting a popular ESLint plugin to steal sensitive data, execute commands, and exploit developer systems.

Security News
The Ultralytics' PyPI Package was compromised four times in one weekend through GitHub Actions cache poisoning and failure to rotate previously compromised API tokens.