
Security News
The Changelog Podcast: Practical Steps to Stay Safe on npm
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.


Sarah Gooding
August 6, 2024
In April, 2023, PyPI (Python Package Index) introduced Trusted Publishers, a new, more secure publishing method for package maintainers that exchanges short-lived identity tokens between a trusted third-party service and PyPI. Trusted Publishers eliminates the need to use username/password combinations or manually generated API tokens to authenticate when publishing to PyPI.
OpenSSF has published a new guide for package repositories that encourages the adoption of Trusted Publishers, as the method was specifically designed for repositories that accept user-built packages. It allows developers to publish to a package repository without having to provision and manage a long-lived API key:
Authentication is performed by exchanging OIDC identity tokens for short-lived and tightly scoped API tokens for authenticating with package repository publishing APIs. Using short-lived API tokens removes the need to share long-lived and potentially highly privileged API tokens with external systems when publishing software.
The guide was written by contributors to the OpenSSF Securing Software Repositories Working Group (WG), which acts as a clearinghouse for new ideas that could benefit multiple ecosystems and works on projects that enable faster cross-pollination of existing ideas across ecosystems. The new guide goes into greater technical detail on how PyPI verifies the OIDC ID token against a pre-configured policy.
Adoption for this new authentication method is growing. In the 15 months since PyPI added support for Trusted Publishers, OpenSSF reports that more than 14,000 projects have voluntarily adopted this authentication method.
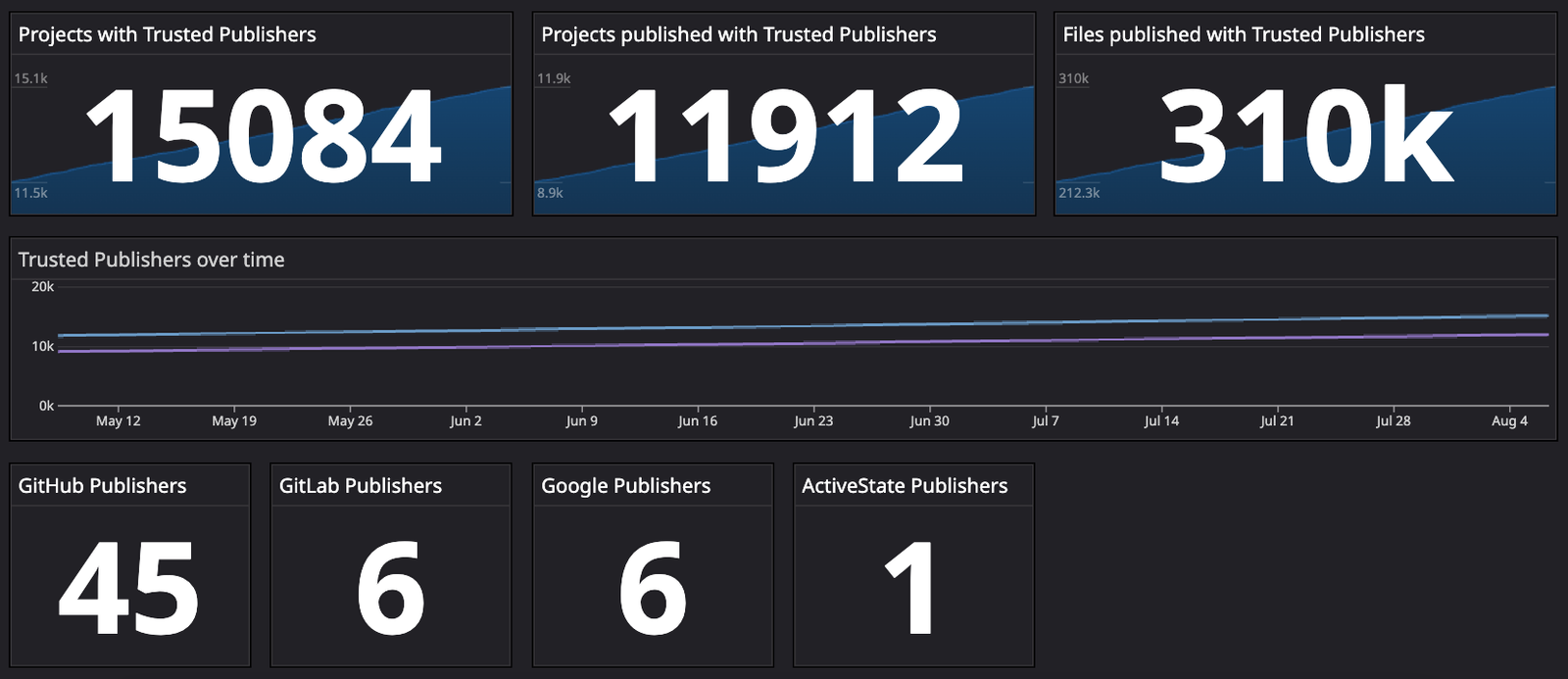
RubyGems.org also introduced support for Trusted Publishers in December 2023, inspired by PyPI.
“We want to encourage gem authors to push their gems from trusted environments, based on the state of public repositories,” Ruby Central’s Security Engineer in Residence Samuel Giddins said. “For many, that means using GitHub Actions (as a CI/CD platform) for gems with repos hosted on GitHub.com.
“Until now, MFA has been incompatible with automated gem pushes. You needed an API key with MFA disabled, stored by GitHub as a long-lived secret, and provided to every CI job. Even worse, given it was a clunky, multi-step process, many gem authors simply pushed gems from their laptops rather than go through the steps required to set that up.”
Giddins highlighted the benefits of using this mechanism for authentication, including the added security of short-lived tokens, which are less likely to be kept and reused by an attacker. Since the Trusted Publishers method pushes through a trusted environment in a way that’s transparent to users of a gem, they can have higher confidence in the release matching what’s in the repository.
Dart’s pub.dev also supports Trusted Publishers when configuring automated publishing, using temporary OpenID-Connect tokens signed by either GitHub Actions or Google Cloud IAM.
In a presentation titled Trusted Publishing: Lessons from PyPI, William Woodruff, open source engineering director at Trail of Bits, highlighted how his team worked with PyPI maintainers to improve publishing security.

Trusted Publishing makes it possible to meet a host of security goals that Woodruff outlined for the PyPI implementation:
Woodruff also noted his team can bring trusted publishing to other package indices where more ecosystems can reap the same benefits that PyPI has in adding this authentication method. The win for PyPI has been the ability to roll out a security improvement that makes users’ lives easier instead of harder. The increasing adoption demonstrates that engineers are willing and actually want to use this method to publish packages.
“Trusted publishing is a logical step towards our shared supply chain goals: source and build provenance, code signing, generalized verifiable attestation over software/dependency graphs,” he said.
The problem of long-lived secrets that are copied into automated deployment environments is an increasing concern, as leaked secrets can lead to unauthorized access, data breaches, and potential exploitation by malicious actors. The Trusted Publishers method reduces the window for abuse. If you maintain a software package repository or publish to one of these registries that have added support, check out OpenSSF’s new guide for implementing Trusted Publishers.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
Learn the essential steps every developer should take to stay secure on npm and reduce exposure to supply chain attacks.

Security News
Experts push back on new claims about AI-driven ransomware, warning that hype and sponsored research are distorting how the threat is understood.

Security News
Ruby's creator Matz assumes control of RubyGems and Bundler repositories while former maintainers agree to step back and transfer all rights to end the dispute.