Security News
Critical Security Vulnerability in React Server Components
React disclosed a CVSS 10.0 RCE in React Server Components and is advising users to upgrade affected packages and frameworks to patched versions now.


Sarah Gooding
January 23, 2024
A German court handed down a chilling verdict in a recent case involving a security researcher who analyzed software on behalf of a client and found Modern Solution GmbH & Co.'s retail customer passwords stored in plain text. The court ruled that the programmer’s actions constituted unauthorized access to external computer systems and spying on data, and issued a €3,000 ($3,265) fine.
Modern Solution offers services in the e-commerce sector, connecting 700,000 customers’ merchandise management systems to online marketplaces for large European marketplaces like Otto, Kaufland, and Check24. The incident took place in June 2021, when the researcher reported the issue to Modern Solution with a three-day deadline to fix it. The company denied that there was a gap in their security but took their systems offline the next day to fix the issue.
Following the chilly reception to the security report, and Modern Solution’s refusal to give comment to a reporter, the programmer went for blood with a speedy disclosure to tech journalist Mark Steier. Steier’s detailed report shows how easily accessible Modern Solution’s databases were, as the credentials were hard coded into the application:
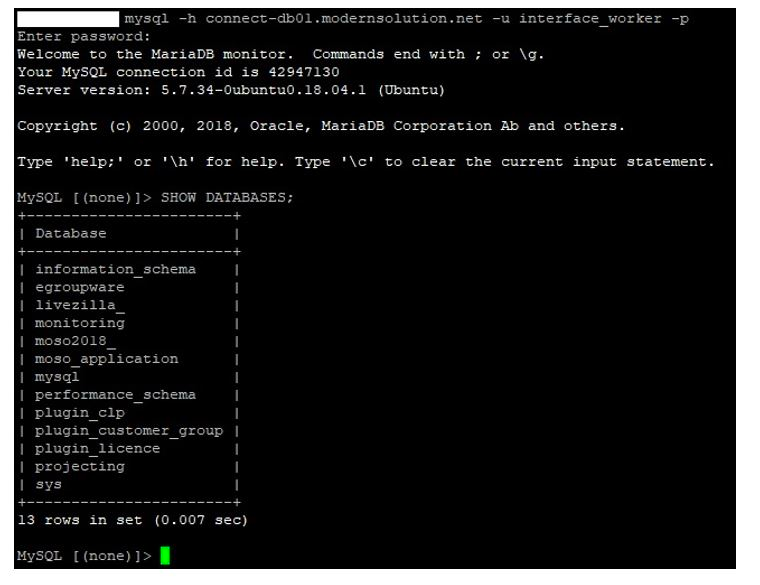
After connecting to the database, the researcher also demonstrated how retail customer data was accessible, not just for the client who had requested help debugging excessive log generation issues, but for all 700,000+ Modern Solution customers.
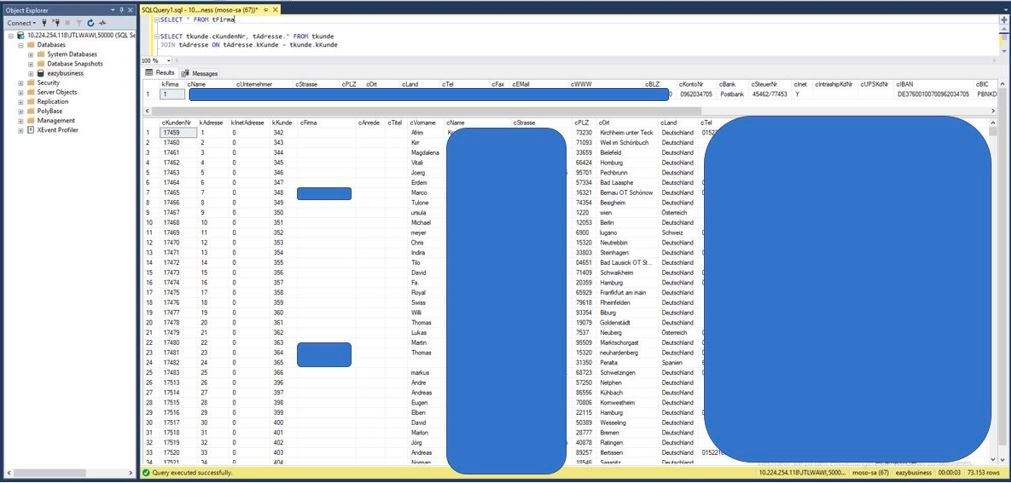
The publication called for customers to seek legal counsel, and characterized the security flaws as signs of corporate negligence and incompetence:
“It is advisable that you consult a lawyer if you are a customer of the JTL partner. GDPR violations are NOT to be trifled with.”
“According to a security expert who wishes to remain unnamed, both the software and the data leak indicate that it was developed sustainably with insufficient expertise and knowledge. The data leak appears to have existed in this form for several years.
"Since the open data points to a large number of omissions and negligence, it is certainly permissible to question the basic competence and suitability of the service provider. If Modern Solution reacts immediately, outages are likely to occur.”
Modern Solutions reported the programmer to the police, presumably because of how the situation unfolded so rapidly in the press. They also published a statement the same day as the news article:
Today, June 23, 2021 at 8:09am, an 'ethical hacker' alerted us to a security vulnerability in our system. Due to this vulnerability, it was possible to access the password to our database and access unencrypted passwords and personal data. Using this database password, the hacker gained external access to our database and our ticketing system. We currently do not know to what extent this data was passed on or further used by the 'ethical hacker' and whether further access occurred. We are working intensively to investigate the incident.
According to Heise, a German IT publication, police arrived at the researcher’s residence on September 15, 2021, “gained access to the apartment and pushed him against the wall. The police confiscated a PC, five laptops, a cell phone and five external storage media - the programmer's entire work device.”
The court convicted the researcher, calling into question whether accessing software with weak password protection through readily available methods constitutes hacking. The judge concluded that because the software had a password for connection, using that password to connect to the database was a criminal offense.
The defense countered that the researcher's actions were ethical security testing, exposing vulnerabilities to help the company improve its software's security as part of a “functional analysis” for one of Modern Solution’s customers. They argued that weak password protection shouldn't be criminalized, and that the researcher's methods were no different from what any skilled attacker could employ.
Ultimately the court sided with the prosecution, finding the researcher guilty of hacking. This raises concerns about how the verdict will impact ethical security research and and whether it could potentially hinder efforts to improve corporate software security.
Since the defendant had no prior convictions, the court was lenient in fining the researcher less the amount demanded by the public prosecutor, as opposed to the worst penalty which would have been three years in prison.
The researcher has appealed the verdict, and the case is likely to be retried in a higher court. The outcome could set a precedent for future cases involving ethical hacking and software vulnerabilities.
An ill-intentioned hacker could have done far more damage to the company and its reputation, potentially disrupting services, selling customer data, or selling the vulnerability on the black market. Instead of thanking the researcher, the company repaid him by criminalizing the activity that led to them securing their systems.
In related discussion on Mastodon, commenters likened the verdict to being convicted of breaking and entering after being handed the key, or after having found the key left under a door mat. One commenter, @ww@xyzzy.link, recommended a more precise metaphor:
“If you really want a metaphor, here's a more accurate one. There's a fulfillment center, and each customer is issued a delivery robot that will drive there and retrieve their deliveries. One customer followed the robot to see where it goes and saw that the door opens for any robot and stays open long enough for another person to enter, allowing access to everyone's deliveries. Reported that to the company and got sued.”
Tamas Lengyel, security researcher at Intel, noted that if a company has no defined security reporting policy and/or an active bug bounty, it’s not surprising that they might be a bad actor in other ways, like reporting a researcher who is trying to help the company address a critical issue.
This interpretation of the law in this disturbing case has sparked discussion about the nature of security research.
“It shouldn't matter how strong the protection was,“ systems administrator @wolf480pl@mstdn.io commented. “The purpose of security research is to find flaws in protections, the same flaws that could be used to do something malicious. That's the whole point. The difference between a security researcher and a cybercriminal isn't what protections they bypass, it's what they do after they find out that they can bypass a protection.”
Security researcher Wladimir Palant echoed that sentiment.
“Abusing hardcoded credentials can definitely constitute hacking and cause perfectly justified criminal charges,” Palant said. “But intention and damage caused definitely need to go into the equation, not merely ‘circumvention of protection mechanisms.’”
The verdict in this case doesn’t serve the greater good of the people, as a programmer reporting a vulnerability in good faith was mistreated, and the retail customers of the company had their data easily accessible for years without Modern Solution having any repercussions. If the next ruling doubles down on the court’s ignorance, security researchers in Germany may be less eager to evaluate vulnerable systems, potentially stifling essential cybersecurity efforts and leaving systems at risk.
“I very much hope that there will be a next instance ruling overturning this decision again,” security researcher Wladimir Palant said. “But it’s exactly as people feared: no matter how flawed the supposed ‘protection,’ its mere existence turns security research into criminal hacking under the German law. This has a chilling effect on legitimate research, allowing companies to get away with inadequate security and in the end endangering users.”
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
React disclosed a CVSS 10.0 RCE in React Server Components and is advising users to upgrade affected packages and frameworks to patched versions now.

Research
/Security News
We spotted a wave of auto-generated “elf-*” npm packages published every two minutes from new accounts, with simple malware variants and early takedowns underway.

Security News
TypeScript 6.0 will be the last JavaScript-based major release, as the project shifts to the TypeScript 7 native toolchain with major build speedups.