
Security News
Research
Data Theft Repackaged: A Case Study in Malicious Wrapper Packages on npm
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.
Get a full Active Directory REST API in 30 seconds
Addict is a drop-in REST API microservice for Active Directory implementations. Just like that.
Doing this:
npm i addict-api -g
addict --url ldaps://[address] --user [user]@[domain] --pass [pass]
Gives you a web server with REST endpoints to add, remove, move, disable, enable, unlock or list Users, Groups and Organizational Units. It includes result caching by default and flexible filters for querying, sorting, pagination and column selection.
There's interactive API docs at /api:
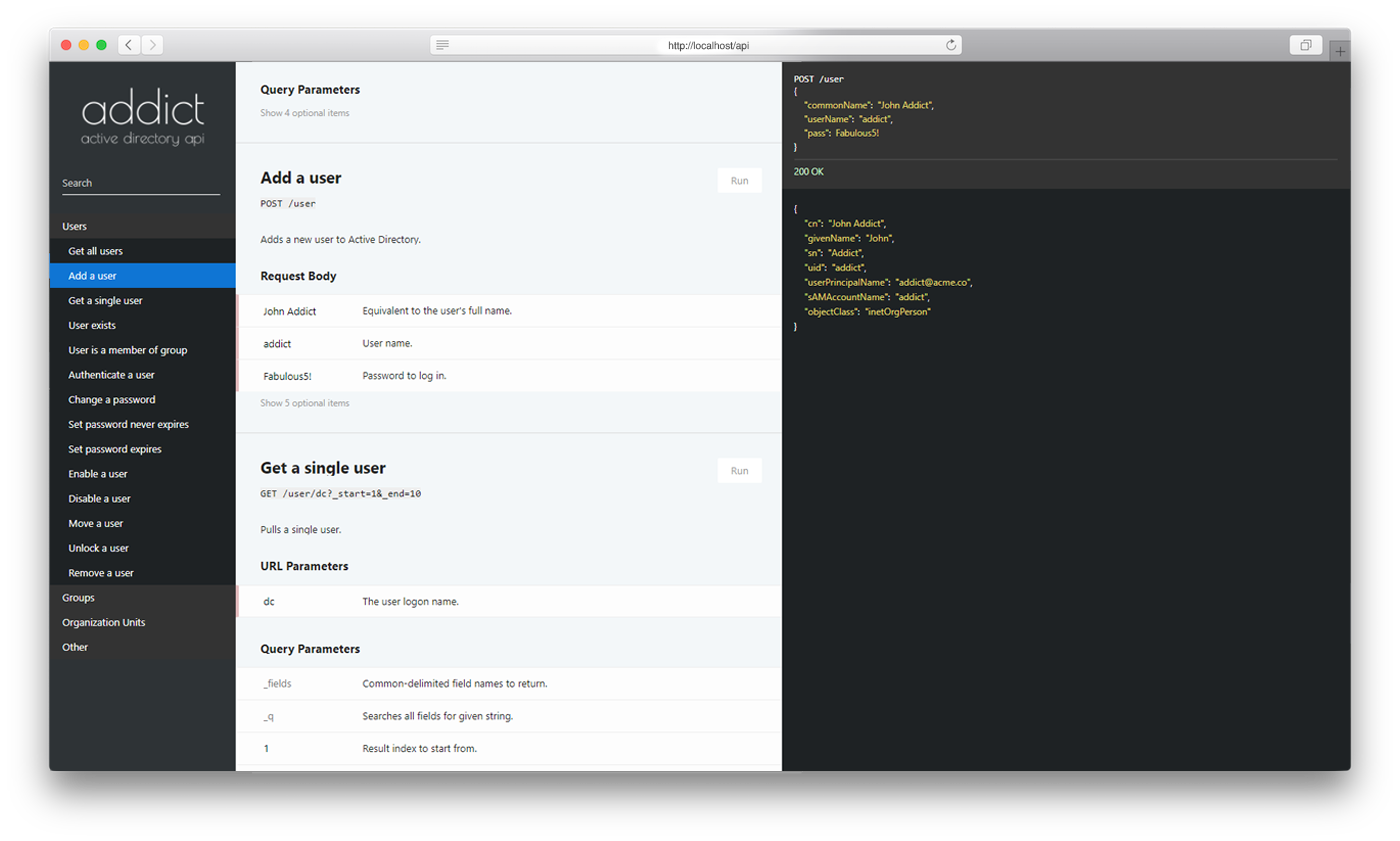
No, it's not Slate.
These docs let you add arguments, try the requests and see the results.
Lastly, it comes with a companion Javascript library.
Made with <3 by dthree.
# Users
GET /user
POST /user
GET /user/:user
GET /user/:user/exists
GET /user/:user/member-of/:group
POST /user/:user/authenticate
PUT /user/:user/password
PUT /user/:user/password-never-expires
PUT /user/:user/password-expires
PUT /user/:user/enable
PUT /user/:user/disable
PUT /user/:user/move
PUT /user/:user/unlock
DELETE /user/:user
# Groups
GET /group
POST /group
GET /group/:group
GET /group/:group/exists
POST /group/:group/user/:user
DELETE /group/:group/user/:user
DELETE /group/:group
# Organizational Units
GET /ou
POST /ou
GET /ou/:ou
GET /ou/:ou/exists
DELETE /ou/:ou
# Other
GET /other
GET /all
GET /find/:filter
GET /status
# Monitoring
GET /status
Want more? Just ask.
Choose which fields to include in the results:
GET /user?_fields=description,cn
Filter any field with fieldName=value.
GET /group?cn=Guests
We've got operators as well:
GET /user?userAccountControl_gte=500
=: Equals_ne=: Not equals_lt=: Less than_gt=: Greater than_gte=: Greater than or equal to_lte=: Less than or equal to_like=: Like (fuzzy search)GET /ou?_sort=whenCreated,dn&_order=desc,asc
GET /user?_page=6&limit=10
Add _start and _end or _limit:
GET /user?_start=20&_limit=40
GET /group?_q=addict
You can pass the AD details at runtime:
addict --url ldaps://[address] --user [user]@[domain] --pass [pass] --port [port]
Port is optional and defaults to 3000.
As environmental variables:
export ADDICT_URL=ldaps://[address]
export ADDICT_USER=[user]@[domain]
export ADDICT_PASS=[pass]
export ADDICT_PORT=[port] # optional
You can run it from docker as well, using environmental variables.
Or in ./config.json:
git clone https://github.com/dthree/addict.git
cd addict
vim ./config.json
{
...
"user": "[user]@[domain]",
"pass": "[pass]",
"url": "ldaps://[address]",
"port": 3000
}
This service defaults to no authentication. I can't and won't try to guess your flavor.
Addict uses express. The file ./middleware.js at the root of the directory exposes the app so you can add middleware hooks for auth logic.
If you connect to Active Directory over plain LDAP, it will refuse certain write operations including adding a user and changing a password. To make things even better, Windows Server doesn't support LDAPS out of the box. You're going to have to set up the Domain Controller as a cert authority by installing the Active Directory Certificate Services Role.
Here's a good tutorial on that.
MIT
FAQs
Get a full Active Directory REST API in 30 seconds
The npm package addict receives a total of 12 weekly downloads. As such, addict popularity was classified as not popular.
We found that addict demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
Research
The Socket Research Team breaks down a malicious wrapper package that uses obfuscation to harvest credentials and exfiltrate sensitive data.

Research
Security News
Attackers used a malicious npm package typosquatting a popular ESLint plugin to steal sensitive data, execute commands, and exploit developer systems.

Security News
The Ultralytics' PyPI Package was compromised four times in one weekend through GitHub Actions cache poisoning and failure to rotate previously compromised API tokens.